Introduction
In organizations, according to Zacarias (2017) (1), the Business Process Management (BPM) serves as a systematic approach to detect, customize, model, execute, document, measure, monitor, analyze, improve business processes (BP) and control automated and not automated processes.
In many business organizations, there is an interest in the BPM, as it is reflected in the report entitled: “The State of Business Process Management” (2019) (2), published in 2018, which shows interesting data such as: 93% of the organizations in the survey are engaged in multiple process improvement projects; 79% said they were using process software tools to model the processes they were analyzing and planning to change. Most of them said that the process models they developed were only used by the process change team, but 22% said that the models were shared with all employees. 65% of those surveyed agreed or strongly agreed that BPM processes and technologies have helped their organizations improve efficiency, versatility and customer satisfaction. In the same way, 59% of the organizations in the survey are engaged in one or more major transformational projects.
At the global level, organizations need to make use of technology for survival in the market, so they require personnel specialized in technology; ones who have knowledge of processes and tools of Information Technologies (IT) that are used on a daily basis. Meanwhile, IT must be aligned with the objectives of their business to be oriented to processes and customer satisfaction.
Among the processes of greatest impact on the organization, there is the IT incident process. For a proper management, the use of standards and best practices are recommended, such as the Information Technology Infrastructure Library (ITIL) (2007) (3), which allows a better performance of the company through the optimization of time, categorization of incidents, acquisition of a good tool for the incidents attention and the increase in user satisfaction.
Morán et al. (2009) (4) argue that incident management is the process that deals with the treatment of events that cause degradation or loss of the normal functionality of a service, with the aim of restoring the service with the minimum negative impact on the business. However, implementing ITIL processes through an organization is not an easy task and presents many difficulties, as indicated by Mahy (2017) (5), so the backing of the CEO of the organization is essential.
The IT incidents process management is operated through the user help desk, which is composed of a set of human and technological resources with the main objective of solving the intermissions of the service that needs attention in the shortest time possible, providing the highest level of technical solution to the problems related to IT.
The large organizations that provide IT services have their own user help desk; such as the case of National Superintendency of Public Registries (SUNARP); a public organization of the Peruvian state that also has its user help desk and this area is part of the Information Technology General Office (ITGO). The ITGO is located at the headquarters of SUNARP, located in the Surco district, Lima – Peru. This office is responsible for receiving the different requests for user attention; either by phone calls, emails or face-to-face requests.
At SUNARP, the attention is managed through a series of procedures which are not well defined or not fully designated for compliance, having no documentation, or lacking defined roles and responsibilities for their attention. So, the organization’s inefficiency in relation to the incidents management results in the ITGO working in a disorderly manner, and in several situations the attention does not come to be attended and it is not known to those who work in the help desk, until the user communicates again that he has not been attended yet. Likewise, the waiting time for the attention of the incidents is too long; sometimes they are not registered for their prompt solution, causing user dissatisfaction. On the other hand, there are also limitations in terms of IT tools to manage the incidents of SUNARP in charge of the help desk.
Among the main problems found in the incident management of the public entity of SUNARP, the most important ones mentioned are as follows:
- Undefined procedures.
- Limitations of available IT tools to manage incidents.
- Long waiting time to attend to users.
- Non-compliance in the operative part of the incident management.
- Lack of follow-up of the attention given to users.
- Some users becoming dissatisfied with the service provided.
For all this, the present investigation made a diagnosis of the current situation in the incident management process in SUNARP. The main objective of this research is to design a model to improve the IT incident management process in a public institution as is the SUNARP, based on ITIL V3 and the BPMN for the graphic notation of processes.
The rest of the paper is organized as follows. Literature Review section includes related works to incidents management. Theoretical frame Section related to the concepts and theories. Research Methodology section describes a sequence of phases for the research. Analysis of the current situation section describes the current situation of the organization, the current analysis of the incident attention process and the strategic evaluation. The section of the Model of processes to improve the management of incidents, describes the proposed TO BE diagram and its differences. Results section describes the comparison between the previous model and the proposed model with ten differences. Recommendations and finally the conclusions are presented in the last section.
Literature Review
This section describes the works realized by different authors, as well as a brief theoretical framework review of interesting topics, for a comprehensive understanding of the incidents management that can help the proposed model improve the incident management processes in a public organization.
Related Works
The publication by Galup et al. (2009) (6) has an objective to raise the awareness of IT service management (ITSM) because of the obvious importance of this IT discipline, they say that the focus of ITSM is on providing specific processes, metrics, and guidance to enable and manage the assessment, planning and implementation of IT service processes to optimize tactical and strategic IT asset use. ITSM is a discipline focusing on a set of well-established processes. These processes conform to standards such as ISO/IEC 20000 and best practices such as ITIL. The goal of ITSM is to optimize IT services in order to satisfy business requirements and manage the IT infrastructure while better aligning IT with organizational objectives.
The research study realized by Sarnovsky et al. (2018) (7), focused on creating predictive models that help in the process of incident resolution and implementation of IT infrastructure changes to increase the overall support of IT management. The main objective was to build the predictive models using machine learning algorithms and CRISP-DM methodology. They used the incident and related changes database obtained from the IT environment of the Rabobank Group company, which contained information about the processing of the incidents during the incident management process. They decided to investigate the dependencies between the incident observation of a particular infrastructure component and the actual source of the incident, as well as the dependency between the incidents and related changes in the infrastructure. They used Random Forests and Gradient Boosting Machine classifiers in the process of identifying incident sources as well as in predicting possible impacts of the observed incident. Both types of models were tested on a testing set and evaluated using defined metrics.
Palilingan et al. (2018) (8) mention in their manuscript that many of the problems that arise in academic information systems come from incidents that are not properly handled. The objective of the study aims to find the appropriate way of incident management. The incident can be managed so that it will not be a big problem. The research uses the ITIL framework to solve incident problems. The technique used in this study is a technique adopted and developed from the service operations section of the ITIL framework. The results of this research found that 84.5% of the incidents appearing in academic information systems can be handled quickly and appropriately. 15.5% of the incidents can be escalated so as not to cause any new problems. The model of incident management is applied to make the academic information system run quickly in providing academic services in a good and efficient way. The incident management model implemented in this research is able to manage resources appropriately so as to quickly and easily manage incidents.
The paper by Blaj et al. (2019) (9) highlights the importance that producers or service providers, who want to furnish an extraordinary experience of their products, have to be available and to give support to their customers 24/7. More companies are opting for Artificial Intelligent Chatbots as part of their customer service team. Some projects aim to optimize and automate support for customers using the Service Now platform with a chatbot. Customers will have their own personal assistant who will create, delete or modify the incidents assigned to them, but it can also be used for recreational purposes or weather forecasts. Users can communicate with the chatbot using normal language through various chat applications: Skype, Webex Teams or through an intelligent speaker. The objectives proposed were: illustrating the chatbot concept, illustrating the notion of chatbot through different scenarios and approaches, integrating and using common messaging services, using a platform, named Firebase, as a service and creating or modifying data streams structured as incidents through APIs.
Astuti et al. (2018) (10), indicate in their manuscript that Directorate of Information Technology and Systems Development (DPTSI) is an organization unit of Institut Teknologi Sepuluh Nopember (ITS) which is responsible for providing services related to information technology (IT) and system for all stakeholders. Incident management and requests fulfillment are part of the services managed by Service Desk unit of DPTSI. Incident management and requests fulfillment hold a significant role yet prone to error; they could pose threats and risks to the organization. Hence, the identification and assessment of risks, especially risks of IT processes, are highly required to avoid problems or disruption in organizational business processes to minimize losses. The research indicates that, COBIT 5 Enabling Process is used as a framework to identify the IT processes, whereas COBIT 5 for Risks is used to conduct the risk management activities. Risks are identified from the Service Desk’s business processes and the existing condition of DPTSI. Data and information were obtained from interviews and observation, and then they were mapped to corresponding ideal conditions based on COBIT 5 process, DSS02 Manage Service Requests and Incidents. Furthermore, risks related to IT processes were identified, assessed and managed based on COBIT 5 process APO12 Manage Risks. This research resulted in a document containing a list of IT risk assessment and risk control justification which can be used as a reference document for Service Desk unit of DPTSI ITS in managing risks associated with IT Processes. They conclude that a good risk management processes will help the decisions’ maker of the organization to make strategic decisions.
The paper by Serbest et al. (2015) (11), indicates that fast development and change in IT require organizations to use “Help Desk Systems”. These systems make people learn the information about the system’s overall structure after entering the system and with the help of this structure they can be acquainted with the process of the frequently asked questions step by step. The purpose of the study was to shorten the orientation time of the FAQS installed along with the increasing amount of countries that the Schneider Electric IT department serves, and to switch to a live system without reducing service quality with minimal job losses. The aims of the project were as follows: To set up a web-based system which doesn’t require installation, to make the help desk personnel utilize the pdf documents related to the works which are carried out in each factory of the company and prepared by the department experts, to increase the satisfaction of the user they have served by responding to problems in the shortest time and to decrease the work load of the location experts in the factory in question. Also, it enables experts to enter the system in a different page and create categories with processes like adding, deleting and searching for documents and viewing current work orders. A program aiming to present values such as selecting files, category ratios, how often experts upload documents to department managers has been developed and presented to the company.
The study realized by Eikebrokk et al. (2017) (12) indicates that ITIL lacks appropriate theories and models that capture the distinctive characteristics and implications of the ITIL implementation practice. The proposed model provides IT executives with practices for improving ITIL processes implementation quality and helps them assess the benefits of their efforts. The results show that implementing ITIL processes can positively influence BPM and lead to other additional benefits in IT departments and potential effects that should motivate IT managers to consider ITIL implementation projects.
Theoretical Frame
This section is based on the fundamental concepts for deepening some context issues as follows in details.
Business Process Management
BPM is an approach that focused on the continuous improvement of business processes in the organizations, providing a collection of best practices. According to Goby et al. (2016) (13), implying a continuous commitment to manage BPs, requires a lifecycle methodology with structured steps and feedback that establish a managerial practice in organizations, which helps in continuous improvement and meeting business objectives (BOs). BPM lifecycle is based on principles, such as modelling and documentation of BP, customer-orientation, constant assessment of the performance of BP, a continuous approach to optimization and improvement, following best practices for superior performance, and organizational culture change.
In the last few years, many authors have contributed with BPM lifecycle proposals, contributing to the growth of BPM. Dumas et al. (2013) (14) consider that the BPM lifecycle proposed consists of the following phases: process identification, process discovery, process analysis, process redesign, process implementation, and process monitoring and controlling. The implementation of the BPM lifecycles in the organizations can address BP change and identify the improvements required to achieve the desired BOs.
BP is defined within a business model as a functional and organizational-border linkage of value-added activities that generate the expected customer benefits and convert the business strategy derived from process goals. However, it must be observed that without BPM there are no Business Process Modeling and Notation.
According to Paschek et al. (2016) (15), based on the definition of the European Association of BPM (EABPM), a process is considered a number of specified activities, which are carried out by people or machines for generating a company’s value.
Business Process Modelling Notation
Several publications of the literature indicate a variety of modeling languages and tools for the design of processes. Despite the increasing use of flowcharts or event-driven process chains today, the Business Process Modeling Notation (BPMN) is used as a new standard worldwide in a short time. As indicated by Paschek et al (2016) (15), BPMN is considered part of BPM tools which is used for the holistic, precise, and formal and consistent description of BP. It additionally emphasizes the benefits of process modeling as noted below:
- Creating transparency over BP;
- Clear and comprehensive documentation of BP as a prerequisite for automation;
- Communication of BP and promoting understanding of the process;
- Analysis, measurement, controlling, benchmarking and optimization of BP;
- As well as risk and compliance management.
IT Service Management
Sarnovsky et al. (2018) (7) argue that ITSM is considered a discipline and it is defined as a set of specialized organizational capabilities for providing value to customers in a form of services. The main goal of ITSM is to ensure delivery of quality IT Services that support the BOs of the organization by using the cost-effective resources.
The publication by Galup et al. (2009) (6) considers that ITSM is a subset of Service Science that focuses on IT operations, such as service delivery and service support. In contrast to the traditional technology-oriented approaches of IT area, ITSM is a discipline for managing IT operations as a service that is process oriented and accounts representing more than half of the total cost of IT ownership. Today, providers of IT services have to consider the quality of the services they provide and focus on the relationship with customers. Due to its processes-focus, it shares a common theme with the process improvement (such as, TQM, Six Sigma, BPM and CMMI), as well as providing a framework to align IT operations-related activities and the interactions of IT technical personnel with business customers and user processes.
The ITSM is a subset of services that focuses on IT operations, such as the provision of services and service support. ITSM is an emerging discipline that focuses on a set of well- established processes. ITSM evolved during the time into highly standardized frameworks based on best practices. These processes correspond to standards such as ISO/IEC 20000 (2009) (16) and best practices such as ITIL or CoBiT (2009).
Mera et al. (2018) (17) argue that ITSM is characterized by its emphasis on IT services, customers, Service Level Agreement (SLA), and the management of the IT function and its daily activities functions through processes, but the IT services need to be classified into a catalog . The information technology service catalog (ITSC) is a structure where the IT services are identified and classified within a given organization. This catalog is the basis for the IT services portfolio to be properly managed during its useful life so that the financial, technological, and human and time resources are used correctly. For this reason, Mera et al. (2019) (18) make a proposal based on automatic learning to identify ITS in public organizations, adapting the catalog of services and taking the history of requests and incidents accredited by the department of information technologies in public organizations, as its main input.
Applying ITSM is a key issue in the management of an organization’s IT functions. ITIL is the most popular and influential framework for applying ITSM. With adoption growing globally, it is important to understand the benefits that ITIL processes can bring to an organization. According to Mcnaughton et al. (2010) (19), the benefits of implementing and using ITIL processes have been predicted or assumed with very little research and minimal anecdotal evidence.
Managing and using IT services is considered very important for modern businesses to improve their performance, for all this, the IT management needs to ensure an adequate flow of complex tasks of the projects and operations with dependence on IT. Achieving a good IT management depends in large parts on an IT Governance Framework adequate into the organization.
Aguilar et al. (2017) (20) argue that IT Governance is part of the enterprise governance which contributes to the management of IT resources, with focus on prioritization and justification of IT investments, controlling, budgeting and defining authorization levels. Gërvalla et al. (2019) (21) indicate that ITIL is one of the IT management frameworks that provide a systematic approach to contribute to the best IT Governance. Its study is based on secondary data focused on understanding the ITIL framework in relation to IT Governance; the paper contributes to IT investments and IT resource management in an organization, starting with technological changes, reduction of the operating costs, maintenance and decision-making process with the focus on improving organization sustainability.
Incident Management
IT incident is referred to as an inadequate functioning of the hardware, software or an information system, reduction in the quality and interruption or failure of a configuration item (CI) that has an impact on IT service (for example; failure of one disk from a mirror set). Incidents may be recognized by the technical staff, detected and reported by event monitoring tools, communicated by users (usually via a telephone call to the service desk), or reported by third-party suppliers and partners. Incident management is the process responsible for managing the lifecycle of all incidents.
Richard et al. (2019) (22) argue that an incident is any event occurred outside the standard operation of a service and may cause an interruption or reduction in the quality of service. The purpose of Incident Management is return services and processes to the normal service level as soon as possible by mitigating the effects of disturbances in IT services. In addition, the authors of the paper consider that the main objective of incident management process is to ensure that every incident occurred during operational activities must be solved by standardized procedure to create quick resolution for the incidents.
Acording to Office of Goverment Commerce, ITIL Service Operation (23), consider six main activities to ITIL Incident Management Process, such as: Incident Identification, Incident Logging, Incident Categorization, Incident Prioritization, Resolution and Discovery, and Incident Closure.
Morán et al. (2009)(4) argue that incident management is the process in charge of the study and solution of the events that cause loss or degradation of the normal operability of a service, its main objective is to restore the service to minimize the negative impact on the organization, to maintain the highest level of availability and quality of service. Alonso et al. (2009) (24) believe that incidents management is considered an IT tactical demand due to its relation to IT services. They argue that the demand for IT services comes from many different sources and surfaces in many different forms. This demand can be segmented into three main categories: 1) strategic, 2) tactical, and 3) operational.
The objectives of incident management are:
- Reduce the time to solve the incidents.
- Prioritize incident attention according to service commitments.
- Increase business efficiency by reducing the impact of incidents through a timely resolution.
- Attend the service requests of customers or users on time.
- Optimize the attention and resolution procedures of incidents.
- Improve customer and user satisfaction.
Service Desk
Some authors as Paramesh et al. (2018) (25) argue that the employees of an organization raise the issue ticket through the IT service desk or Helpdesk which is typically of web based. The submitted tickets will then be assigned to a proper domain expert group or service desk agent for resolving the problem ticket depending upon the category of the ticket, such as typical IT infrastructure problems related to hardware issues, software issues, network issues, email issues etc. Web based IT service desk systems contains the structured fields like submitter, ticket category, priority, severity etc. It also contains the free form fields like ticket description where the user enters the description about the ticket in his natural language.
Suryotrisongko et al. (2017) (26), argue that the Service desk and help desk is kind of the same thing defined by different names. Help desk is also defined as an area in any organization which helps end-users find answers and solutions to problems they face. Service desk is a specific type of service; an outsourced support group aiding callers by resolving the problem or transfer the call to others for help.
The service desk is the single point of contact for users when there is a service disruption, service requests of the IT support or even for some categories of requests for change. The service desk provides a point of communication to users and customers, as well as a point of coordination for several IT groups and processes. This means that the service desk symbolizes the total concentration of services for users and customers, being the reference center for users of the service (SPOC, Single point of contact), as indicated by Rios (2013) (27).
Morán et al. (2009) (4) argue that the service desk is also named the service center, it consists of a team of people who receive contacts from customers or users either through calls, messages, tickets, etc. to register, classify and attempt to resolve or forward problems to appropriate support groups.
The functions of a Help desk are as follows:
- Be the space for communication and contact between users and services.
- Provide provisional solutions to errors and incidents, in relation to problem management.
- Record events that have caused loss or degradation of a service reported by an affected user, following the process indicated by the protocol of best practices.
- Track the events reported above and inform the user of the status of the event.
- Derive change requests when necessary.
- Provide users with the information requested by them, so that the database must be kept updated.
Information Technology Infrastructure Library (ITIL)
ITIL contains a set of best practices but it does not provide a step-by-step guideline that details how to conduct the implementation of an ITSM framework in companies. As indicated by Orta et al. (2019) (28), ITIL has been accepted in the industry as the de facto standard more popular in ITSM and it is adopted by public and private organizations worldwide. The standard provides the basis to ensure quality ITSM through documented and well- established processes that cover all the service lifecycle. Alonso et al. (2009) (29) indicate that in recent years, a growing number of CEOs and CIOs are implicated in the IT demand process life cycle, for future business success driven from within the IT governance. Through the IT tactical demand, they are implementing ITIL to improve their ITSM processes and provide significant benefits for their organizations.
Bartolini et al. (2010) (30) argue that ITIL is a comprehensive set of concepts and techniques for managing IT infrastructure, development and operations. Developed by the UK Office of Government Commerce, ITIL is the de facto best practice standard for ITSM today.
Ilvarianto et al. (2017) (31) argue that to determine ITIL processes, organizations must be situated in the context of continuous improvement of end-user services both internally and externally. IT’s concentration on customer value will contribute to the strategic alignment of IT services with the business of the company. ITIL V3 (3) defines five sections and more emphasis on managing the lifecycle of IT services provided.
- Service Strategy: This stage is used for practical decision-making. At this stage of the cycle, the role of IT needs are defined (32).
- Service Design: This stage is the blueprint of IT services. This part of IT services is designed to meet the needs of the business, so that the service can be arranged (manageable) and cost-effective (cost effective) (33).
- Service Transition: This stage is used to change management (Change Management), minimize risk and ensure quality. The service will be tested and introduced in the IT infrastructure. Service Transition ensures that IT can respond to changes in both the business and IT environment (34).
- Service Operation: This stage is needed to make the service more responsive and stable. At this stage, the service is provided (23).
- Continual Service Improvement: This stage involves the regulatory process, the measurement of the quality and the cost of the service. This stage also identifies which areas can be improved while still adjusting to changing business needs (35).
In the introduction section of ITIL Service Transition, sub section 1.3 (2011) (34) highlights that ITIL is part of a portfolio of best-practice publications, known collectively as Best Management Practice (BMP) aimed at helping organizations and individuals manage projects, programs and services consistently and effectively. All BMP guidance is intended to be tailored for use by individual organizations. Likewise, it indicates that ITIL can be used in harmony with other BMP products and international or internal organization standards. ITIL’s relationship with other Best Management Practice guides includes: Management of Portfolios (MoP), Management of Risk (MoR), Management of Value (MoV), Managing Successful Programs (MSP), Managing Successful Projects with PRINCE2, Portfolio, Program and Project Offices (P3O). All these guides contribute to improving the IT management.
Research Methodology
To develop the work with certified knowledge, the authors of this paper attended the training of the ITIL V3 Workshop, and the Process Modeling Workshop using Bizagi Process Modeler tools at the National Engineering University (UNI).
To achieve the objectives of this work, they considered the best practices of ITIL V3 (3). At the same time, to realize the processes diagram designs for the incidents management, they used the Business Process Modeling Notation (BPMN), a standard for business process modeling that provides a graphical notation for specifying business processes in a Business Process Diagram (BPD), based on a flowcharting technique very similar to activity diagrams from Unified Modeling Language (UML).
To develop the research work, a sequence of five phases was considered as shown in Figure 1.
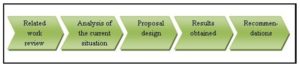
Fig. 1: Proposal to carry out the investigation
Below, a brief description of each of the processes is presented in the proposal to develop the research work.
- Related work review: It is the first stage of the methodology, which relates literature review to the last relevant proposals in relation with the research.
- Analysis of the current situation: It is the second stage to study the entity where the work was carried out and the required information obtained from it, as well as the improvement of incident management process for which the study is done. It is considered the strategy in the ITIL life cycle (36).
- Design of the proposal: This is the stage where the incident management process proposed with its time indicators, as well as the metrics, is modeled to be considered in the process.
- Results obtained: It is related to the results obtained in the proposal, making a comparison between before and after the incident management and verifying the initial goals.
- Recommendations: They are the recommendations for developing the proposal.
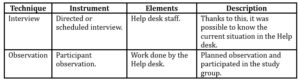
The data collection techniques used for the investigation, were direct techniques that require an interpersonal relationship between the examiner and the individuals participating in the study, according to Sánchez (2015) (37). Among the direct techniques, the interviews and observations were considered.
To carry out this work, direct techniques have been used: structured interviews and observation. The observation technique can be of two types: natural or systematic participant. The participant observation is the one in which the examiner is part of the study group. The details of data collection techniques are shown in Table 1.
Table 1: Details of Data Collection Techniques
Analysis of the Current Situation
Current Situation of the Organization
SUNARP is the public entity part of the National System of Public Registries, and the autonomous public entity of the Justice Sector. Its main roles and powers are: to program, order, regulate, direct and validate the heading and propaganda of the acts and contracts of the registries that the system controls, as well as the policies of the controlled registries that are part of this system.
By Law No. 26366, the National Public Registry System and the National Superintendence of Public Records – SUNARP are created, and by Supreme Resolution No. 135-2002-JUS, the Statute of SUNARP is approved.
Through Resolution N ° 346-2015-SUNARP / SN, the National Superintendence of Public Registries approved its Institutional Strategic Plan for the period 2016-2018, in which it indicated that the vision is developed at the Justice Sector level and Human rights and the mission is defined at the institutional level.
The Headquarters is located in the district of Santiago de Surco. It has 230 employees, of which 7 are located in the help desk area. Currently, the help desk area is composed of a Coordinator and 8 supporting people. The attention to the users is realized with the reception of requests and/or incidents that can be through: telephone calls, mails or in person.
The justice group is one of the vital sectors in the country, its purpose is to take care of compliance with laws, justice and people’s rights, promote human rights and have a reliable and inclusive justice, and focus on the vulnerable population. Likewise, by means of the formulation, evaluation and execution of institutional policies of the State, it provides legal advice and defense of its interests.
Current analysis of the IT incident Attention Process
Knowing the scope of the process allows knowing the incidents that the help desk addresses in the organization in their day-to-day activities.
The scope of the IT incident attention process is presented in Table 2.
Table 2: Scope of incident management

An evaluation of the current situation of the processes was carried out through an interview with the 8 members of the help desk; the questions asked were linked to knowledge, roles, activities and compliance with the current process which allowed the authors of this paper to know the current situation of the “Incident attention” process. To carry out the interview, the following research questions were posed:
- Do you know if there is a process for incident management?
- In the current process for incident management, are your roles determined?
- In the current process for incident management, are your activities well defined?
- Does the tool for recording incidents allow better control and help with compliance process?
The following results were obtained from the survey of the members of the help desk service to know the current situation of the incident management process.
- For the first question, 83.33% of the respondents replied that they are unaware of the existence of the incident management process (5 of the members).
- For the second question, after showing the flowchart of the “Incident Attention” process, 33.33% of the respondents indicated that their roles are not well defined (2 of the 6 members).
- For the third question, after showing the flowchart of the “Incident Attention” process, 66.67% of the respondents (4 of the 6 members) indicated that the activities they carry out are not well defined.
- For the fourth question, 100% of the respondents indicated that there is no support technology tool for incident management in order to have better control and help with compliance of the processes.
Strategic Evaluation
Identification of Customers and their Needs
To enrich the incident management process, it is necessary to know those involved in the process; to which the services are offered, and their needs. In the organization, two types of customers involved were identified in the process, the internal and external customers.
The internal clients identified are: the head of the ITGO and the headquarters staff. The needs of internal customers are the following:
- Resource operability (software and hardware)
- Resource availability (software and hardware)
- Resource support (software and hardware).
The external customers identified are: users from other areas and outside the headquarters. The needs of external customers are the following:
- Resource operability (software)
- Resource availability (software)
- Resource support (software).
After identifying the clients and their needs, the SWOT analysis is carried out to identify the current situation of the help desk of the organization.
SWOT Analysis of the Current Situation of the Help Desk
The SWOT analysis provides a quick image of the participants’ own assessment of the organization (or even group, project or any other part of the organization) and its environment.
Using the observation technique for the analysis of the organization, the Strengths, Opportunities, Weaknesses and Threats of the internal and external factors of the help desk were identified, which is easily summarized in Table 3.
Table 3: SWOT matrix of the current situation of the help desk
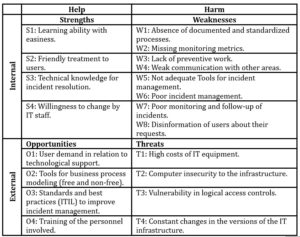
Internal Factors: these are the strengths that contribute to the help desk, four strengths were identified. There are also weaknesses, which are detrimental to the help desk, eight weaknesses were identified.
External Factors: these are the opportunities or conditions which favour the help desk, four opportunities were identified. Likewise, there are threats that cause damage in the area, four threats were identified.
The AS IS/TO BE Process Mapping is a management tool that helps in the description and improvement of the internal processes of the organizations. It is dedicated to the exploration of the company’s business through methodologies and practices used in day-to-day activities.
The AS IS process mapping is the definition of the current process situation. The participants of this assignment are the users who are involved in the daily process (known as key users). In this context, a good practice is to ask the executor of the process to report how to execute it, or a questionnaire is made to gather the information.
Doing the strategic evaluation, it is also important to know how this process works in the SUNARP. For this specific case, the diagram AS IS is used as shown in Figure 2.
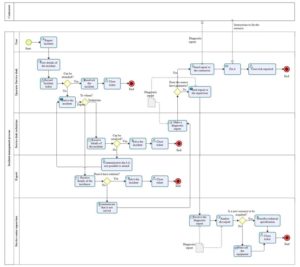
Fig. 2: AS IS diagram
In figure 2, the current IT Incident Attention process in the help desk is shown. As this process is in a manual form and is not standardized, the transfer for the modeling of processes was made using a suitable tool (Bizagi Process Modeler); the change made is for a better explanation of the current situation of the process without making any disturbance.
Taking into account this diagram as an initial base, it is possible to make a new process model to improve the incidents management in the organization.
Model to Improve IT Incident Management Processes
For the proposal, the TO BE process mapping is used, the mapping defines the future of the IT incident management process situation. It is also where the authors of the paper document what is defined in the mapping with the help of tools that add value to the process, such as BPM (Business Process Management) technologies.
Having the information obtained in the analysis of the situation of the organization, the TO BE diagram is proposed, which is the business model to be proposed, as shown in Figure 3.
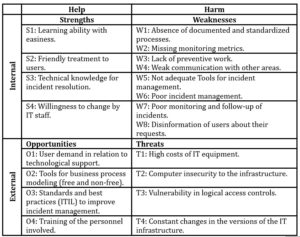
Fig. 3: TO BE diagram
As seen in the above figure, the proposed model for the IT incident management process is divided into three phases, as indicated below:
- First phase: Registration.
- Second phase: Attention.
- Third phase: Answer.
Results Obtained
After making the proposal of the new model, a comparison is made between the initial model and the proposed model, finding the differences indicated below:
First Difference: Phases of the Proposed Model.
The Incident Management process has been divided into 3 phases or milestones: Registration, Attention and Response. This allows identifying and defining the phases for a better reading of the process and its understanding.
Second Difference: Roles and responsibilities for the incident management process.
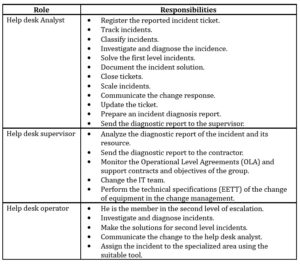
Initially, the roles of the staff of the user attention process are not well defined. The proposed diagram, such as indicated, has some actors involved; users, help desk analysts, help desk operators and contractors. In the help desk, there are two analysts one coordinator and four operators.
It is important to identify the members involved in the team work and establish specific roles for each of them according to the nature of the organization. Table 4 shows a list of roles and responsibilities identified and assigned to the members involved in the incidents management process for better performance of its duties in the day to day activities.
Table 4: Roles and Responsibilities for the incident Management Process
Third Difference: Classification of the Incidence
In the incident management process of the old model, the activity of classifying incidences was not considered. However, the new model includes the activity of classifying or categorizing the incidence as indicated in ITIL V3.
According to the incident management process, the time of this activity must be 5 minutes maximum in an SLA. Its previous activity was to register an incident ticket in case the user did not enter the details of the incident in a ticket, but if the incident details are in the ticket, the incident is classified. The subsequent activity is to investigate and diagnose the incidence. It is a user-type activity, since the help desk analyst must classify the incident through the use of the incident management tool.
The activity of classifying incidents is related to prioritization, which is one of the objectives of this work. This activity aims to establish the impact and priority of resolution. Depending on this activity, the time of resolution of the incidents varies, as well as the allocation of the resources that will be needed for their solution. After the classification of the incident, the prioritization of the incident will be carried out. Prioritization should be based on impact and urgency.
Fourth Difference: Investigation and Diagnosis of the Incidence
In the process of incidents attention, after registering the ticket of the incident, the authors of the paper proceed to evaluate; while in the incident management process, the activity of investigating and diagnosing the incident as indicated by ITIL V3, is considered.
This activity must have a maximum SLA of 1 hour and the information is provided by the incident database, this task is performed by the help desk analyst.
Fifth Difference: Database of Incidents
The activity of solving incidents is involved in the process of incidents attention, but the difference found is that this activity is based on incidents database for its solution; this activity is performed by the help desk analyst.
Sixth Difference: Documentation and Closing of the Incident
The activity of documenting and closing a ticket refers to the documentation of the solution of the first level incidents carried out by the help desk analyst in case the incident occurs again, the solution can be at hand until the total solution, then close the ticket again. This activity must have a maximum SLA of 10 minutes. With the culmination of this activity, the process is closed.
The difference between the processes of the models is that in the previous model, the undocumented activities processes had negative implications on efficiency.
Seventh Difference: Scaling Process
In the new business model, the embedded sub process; called scaling process, was added. The previous model had too many activities which do not allow the model to be simple and easy to understand, for this reason, a new sub process was incorporated. This process is performed by the operator of the help desk.
Another difference identified in the proposed model is the proposal of 4 levels of escalation indicated below:
- N1: Help Desk Analyst
- N2: Support Operator
- N3: Specialized area
- N4: Help Desk Supervisor (Change Management).
Eighth Difference: Change Management
The new business model incorporates the reusable sub process; called the change management process. The previous model had too many activities which did not allow a simple and easy understanding of the model, for this reason, the new sub process was incorporated, this process is performed by the help desk operator and the analyst. If then, in the sub-escalation process, the solution of the incidence is not achieved, the change management is continued.
Ninth Difference: Time of attention of the incidents
In the incident’s attention process of the previous model, the times of the activities are not indicated, this makes any incident, however simple, take the longest time for the solution. With the new incident management process model proposed, all processes and sub processes are temporized, allowing time saving in incidence management.
Below are the times of the incidents attended during the months (January, February and March) and subsequently the same incidents with their times of solution, taking into account the process model with ITIL V3 and BPMN, showing the saving time that occurs with the use of the new proposal, as evidence.
In January, 490 incidents were recorded.
- A total of 4070 minutes was used in the incidents attention reported.
- With the proposed model, a total of 2085 minutes would have been spent in the incidents attention.
In the month of February, 363 incidents were recorded.
- In the month of February, a total of 4512 minutes was used in the attention of the reported incidents.
- With the proposed model, a total of 3230 minutes would have been spent in the incidents attention.
In March, 192 incidents were recorded.
- In the month of March, a total of 6152 minutes was used in the attention of the reported incidents.
- With the proposed model a total of 3123 minutes would have been spent in the incidents attention.
Tenth Difference: Inclusion of Artifacts
Considering the differences found between previous and proposed models, the proposed model process consider two artifacts: the database of the incidents and the diagnostic report. The artifacts serve to make the model understandable and easy to read.
Recommendations
In this section, the following recommendations are made:
- The implementation of the proposed model based on best ITIL V3 practices to improve the service to the end user by reducing service time.
- The change of the IT incident management tools in the help desk to achieve the classification and prioritization of the incidents.
- Training related to the implementation of best practices ITIL V3 to help improve the incidents management in the help desk, as well as the use of the proposed tool for the use of incidents, to work efficiently, optimizing the processes indicated by ITIL V3.
Conclusions
The IT incident management process was modeled with its sub processes: Scaling process and Change management according to the BPMN standard and based on best practices of ITIL V3. This has improved the incident management in the help desk of SUNARP, Surco.
With the improvement of the time based in best practices of ITIL, deficiencies in the service can be identified to be solved and thus comply with the care process in less time.
The new process model for incident management has made it possible to prioritize the attention of the incidents through the classification of these incidents, with the tool of the emergency matrix for impact, allowing to record and classify the incidents properly.
With the knowledge of the proposal based on ITIL best practices, the help desk staff achieves improvements in customer service, in terms of providing good service and user satisfaction.
Acknowledgment
The research was developed as part of an undergraduate thesis in Professional School of System Engineering. Thanks to a special acknowledgement by economic financing and the logistics provided by the Institute of Research (IR) of the National Technological University of South Lima, Peru.
(adsbygoogle = window.adsbygoogle || []).push({});
References
- Zacarias M, Ventura Martins P, Gonçalves A. An Agile Business Process and Practice Meta-model. In: Procedia Computer Science. Elsevier B.V.; 2017. p. 170–7.
- Harmon P. The future of business process management. In: Business Process Trends. Elsevier; 2019. p. 441–55.
- Cartlidge A, Hanna A, Colin R, Macfarlane I, Windebank J, Rance S. An Introductory Overview of ITIL® V3. The UK Chapter of the itSMF; 2007.
- Morán Abad L, Pérez Sánchez A, Trujillo Gaona J, Bathiely Fernández D, González-Simancas Sanz MJ. ISO/IEC 20000: Guía completa de aplicación para la gestión de los servicios de tecnologías de la información. 2009.
- Mahy Y, Ouzzif M, Bouragba K. Supporting ITIL processes implementation using business process management systems. Proc – 2016 3rd Int Conf Syst Collab SysCo 2016. 2017;31–4.
- Galup SD, Dattero R, Quan JJ. An Overview of IT Service Management. Commun ACM. 2009;52(5):124–7.
- Sarnovsky M, Surma J. Predictive Models for Support of Incident Management Process in IT Service Management. Procedia Comput Sci. 2018;18(1):57–62.
- Palilingan VR, Batmetan JR. Incident Management in Academic Information System using ITIL Framework. 2018;306:1–9.
- Blaj R, Coiciu A, Bălan T. Incident management assistant using artificial intelligence chatbots. Sci Bull Nav Acad. 2019;22(1).
- Astuti HM, Muqtadiroh FA, Tyas Darmaningrat EW, Putri CU. Risks Assessment of Information Technology Processes Based on COBIT 5 Framework : A Case Study of ITS Service Desk. In: 4th Information Systems International Conference 2017, ISICO 2017, 6-8 November 2017, Bali, Indonesia [Internet]. Elsevier B.V.; 2018. p. 569–76. Available from: https://doi.org/10.1016/j.procs.2017.12.191
- Serbest S, Goksen Y, Dogan O, Tokdemir A. Design and Implementation of Help Desk System on the Effective Focus of Information System. In: 7th International Conference, The Economies of Balkan and Eastern Europe Countries in the changed world, EBEEC 2015, Kavala, Greece. Elsevier B.V.; 2015. p. 461–7.
- Eikebrokk TR, Iden J. Strategising IT service management through ITIL implementation: model and empirical test. Total Qual Manag Bus Excell. 2017;28(3–4):238–65.
- Goby N, Brandt T, Stefan F, Neumann D. Business Process Modelling to Improve Incident Management Process. In: Conference: 24th European Confrence on Information Systems (ECIS 2016). 2016.
- Dumas M, La Rosa M, Mendling J, Reijers HA. Fundamentals of Business Process Management. Fundamentals of Business Process Management. Springer Heidelberg; 2013.
- Paschek D, Rennung F, Trusculescu A, Draghici A. Corporate Development with Agile Business Process Modeling as a Key Success Factor. Procedia Comput Sci [Internet]. 2016;100(0):1168–75. Available from: http://dx.doi.org/10.1016/j.procs.2016.09.273
- Disterer G, Stadtweg R. ISO 20000 for IT. Bus Inf Syst Eng. 2009;6:463–7.
- Mera Macias C, Alonso IA. Review of Proposals for the Construction and Management of the Catalog of Information Technology Services. IEEE Access. 2018;6.
- Mera Macias C, Aguilar Alonso I. Proposal for the Identification of Information Technology Services in Public Organizations. Symmetry (Basel). 2019;11(10):1–32.
- Mcnaughton B, Ray P, Lewis L. Designing an evaluation framework for IT service management. Inf Manag [Internet]. 2010;47(4):219–25. Available from: http://dx.doi.org/10.1016/j.im.2010.02.003
- Aguilar Alonso I, Carrillo Verdún J, Tovar Caro E. Description of the structure of the IT demand management process framework. Int J Inf Manage. 2017;37:1461–73.
- Gërvalla M, Preniqi N, Kopacek P. IT Infrastructure Library ( ITIL ) framework approach to IT Governance. In: IFAC- Conference Paper Archive. Elsevier B.V.; 2018. p. 181–5.
- Richard, Gaol FL, Warnars HLHS, Abdurachman E, Soewito B. Development of Web Application based on ITIL – Incident Management Framework in Computer Laboratory. In: Proceedings of 2019 International Conference on Information Management and Technology, ICIMTech 2019. IEEE; 2019. p. 120–5.
- ITIL. ITIL Service Operation [Internet]. 2011 Editi. Published by TSO; 2011. Available from: www.tsoshop.co.uk
- Alonso IA, Verdún JC, Caro ET. IT, senior executives and board of directors contribute to the success of the business: Implicates on the it demand process – Life cycle. In: ICCIT 2009 – 4th International Conference on Computer Sciences and Convergence Information Technology. 2009. p. 149–56.
- Paramesh SP, Ramya C, Shreedhara KS. Classifying the Unstructured IT Service Desk Tickets Using Ensemble of Classifiers. In: Proceedings 2018 3rd International Conference on Computational Systems and Information Technology for Sustainable Solutions, CSITSS 2018. IEEE; 2018. p. 221–7.
- Suryotrisongko, HatmaQoiru Mucharomah MD. Ideal Help Desk/Service Desk in E-Government and Service Quality: A Literature Review. In: 2017 International Conference On Information & Communication Technology and Systems (ICTS). 2017. p. 203–8.
- Ríos Huercano S. Manual ITIL V3 Integro. Biable Manag Excell Innov. 2013;
- Orta E, Ruiz M. Met4ITIL: A process management and simulation-based method for implementing ITIL. Comput Stand Interfaces [Internet]. 2019;61:1–19. Available from: https://doi.org/10.1016/j.csi.2018.01.006
- Alonso IA, Verdún JC, Caro ET. IT, Senior Executives and Board of Directors Contribute to the Success of the Business: Implicates on the IT Demand Process–Life Cycle. In: 2009 Fourth International Conference on Computer Sciences and Convergence Information Technology [Internet]. IEEE; 2009 [cited 2016 Feb 16]. p. 149–56. Available from: http://www.scopus.com/inward/record.url?eid=2-s2.0-77749319293&partnerID=tZOtx3y1
- Bartolini C, Stefanelli C, Tortonesi M. SYMIAN: Analysis and performance improvement of the IT incident management process. IEEE Trans Netw Serv Manag. 2010;7(3):132–44.
- Ilvarianto DS, Legowo N. Incident management implementation using continual service improvement method at PT AOP. Proc – 2017 Int Conf Appl Comput Commun Technol ComCom 2017. 2017;2017-Janua:1–7.
- ITIL. ITIL Service Strategy. 2017. 45–63 p.
- ITIL. ITIL Service Design [Internet]. 2011 Editi. Published by TSO; 2011. Available from: www.tsoshop.co.uk
- ITIL. ITIL Service Transition [Internet]. London: TSO (The Stationery Office); 2011. Available from: www.tsoshop.co.uk%0AMail,
- ITIL. ITIL Continual Service Improvement [Internet]. London: TSO (The Stationery Office); 2011. Available from: www.tsoshop.co.uk
- Office of Government Commerce. The Official Introduction to the ITIL Service Lifecycle. London: The Stationery Office; 2007.
- Sánchez H, Reyes C. Metodología y diseños en la investigación científica. 2015;










