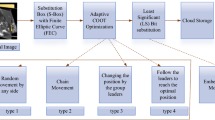
Abstract
The development of the Internet of Things (IoT) is predicted to change the healthcare industry and might lead to the rise of the Internet of Medical Things. The IoT revolution is surpassing the present-day human services with promising mechanical, financial, and social prospects. This paper investigated the security of medical images in IoT by utilizing an innovative cryptographic model with optimization strategies. For the most part, the patient data are stored as a cloud server in the hospital due to which the security is vital. So another framework is required for the secure transmission and effective storage of medical images interleaved with patient information. For increasing the security level of encryption and decryption process, the optimal key will be chosen using hybrid swarm optimization, i.e., grasshopper optimization and particle swarm optimization in elliptic curve cryptography. In view of this method, the medical images are secured in IoT framework. From this execution, the results are compared and contrasted, whereas a diverse encryption algorithm with its optimization methods from the literature is identified with the most extreme peak signal-to-noise ratio values, i.e., 59.45 dB and structural similarity index as 1.








Similar content being viewed by others
Change history
14 December 2022
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s00521-022-08143-y
References
Gaber T, Abdelwahab S, Elhoseny M, Hassanien AE (2018) Trust-based secure clustering in WSN-based intelligent transportation systems. Comp Netw. https://doi.org/10.1016/j.comnet.2018.09.015
Safi A (2017) Improving the security of the internet of things using encryption algorithms. World Acad Sci Eng Technol Int J Comput Electr Autom Control Inf Eng 11(5):546–549
Islam SR, Kwak D, Kabir MH, Hossain M, Kwak KS (2015) The internet of things for health care: a comprehensive survey. IEEE Access 3:678–708
Thibaud M, Chi H, Zhou W, Piramuthu S (2018) Internet of things (IoT) in high-risk environment, health, and safety (EHS) industries: a comprehensive review. Decis Support Syst 108:79–95
Elhoseny M, Abdelaziz A, Salama AS, Riad AM, Muhammad K, Sangaiah AK (2018) A hybrid model of internet of things and cloud computing to manage big data in health services applications. Future Gener Comput Syst 86:1383–1394
Pizzolante R, Castiglione A, Carpentieri B, De Santis A, Palmieri F, Castiglione A (2017) On the protection of consumer genomic data on the internet of living things. Comput Secur 74:384–400
Tankard C (2015) The security issues of the internet of things. Comput Fraud Secur 2015(9):11–14
Rahmani AM, Gia TN, Negash B, Anzanpour A, Azimi I, Jiang M, Liljeberg P (2018) Exploiting smart e-health gateways at the edge of healthcare internet-of-things: a fog computing approach. Future Gener Comput Syst 78:641–658
Kothmayr T, Schmitt C, Hu W, Brünig M, Carle G (2013) DTLS based security and two-way authentication for the internet of things. Ad Hoc Netw 11(8):2710–2723
Al Hasib A, Haque AAMM (2008) A comparative study of the performance and security issues of AES and RSA cryptography. In: Third international conference on convergence and hybrid information technology, 2008, ICCIT’08, vol 2. IEEE, pp. 505–510
Sharma R, Sandhu C (2015) Hyper spectral image restoration using low-rank matrix recovery and neural network. J Adv Res Comput Eng Technol 4(7):3312–3318
da Cruz MA, Rodrigues JJP, Al-Muhtadi J, Korotaev VV, de Albuquerque VHC (2018) A reference model for internet of things middleware. IEEE Internet Things J 5(2):871–883
Zhang J, Duong TQ, Woods R, Marshall A (2017) Securing wireless communications of the internet of things from the physical layer, an overview. Entropy 19(8):420
Kuppuswamy P, Al-Khalidi SQ (2014) Hybrid encryption/decryption technique using new public key and symmetric key algorithm. Int J Inf Comput Secur 6(4):372–382
RebouçasFilho PP, Cortez PC, da Silva Barros AC, Albuquerque VHC, Tavares JMR (2017) Novel and powerful 3D adaptive crisp active contour method applied in the segmentation of CT lung images. Med Image Anal 35:503–516
Alshammari FH (2017) An efficient approach for the security threats on data centers in iot environment. Int J Adv Comput Sci Appl 8(4):73–80
Usman M, Ahmed I, Aslam MI, Khan S, Shah UA (2017) Sit: a lightweight encryption algorithm for secure internet of things. arXiv preprint arXiv:1704.08688
Moraes JL, Rocha MX, Vasconcelos GG, Vasconcelos Filho JE, de Albuquerque VHC (2018) Advances in photopletysmography signal analysis for biomedical applications. Sensors (Basel, Switzerland) 18(6):1–26
Shehab A, Elhoseny M, Muhammad K, Sangaiah AK, Yang P, Huang H, Hou G (2018) Secure and robust fragile watermarking scheme for medical images. IEEE Access 6:10269–10278
Hossain M, Islam SR, Ali F, Kwak KS, Hasan R (2017) An internet of things-based health prescription assistant and its security system design. Future Gener Comput Syst 1–26
Yaqoob I, Ahmed E, ur Rehman MH, Ahmed AIA, Al-garadi MA, Imran M, Guizani M (2017) The rise of ransomware and emerging security challenges in the internet of things. Comput Netw 129:444–458
Elhoseny M, Ramírez-González G, Abu-Elnasr OM, Shawkat SA, Arunkumar N, Farouk A (2018) Secure medical data transmission model for IoT-based healthcare systems. IEEE Access 6:20596–20608
Limaye A, Adegbija T (2018) ERMIT: a benchmark suite for the internet of medical things. IEEE Internet Things J 1–10
Lakshmanaprabu SK, Shankar K, Khanna A, Gupta D, Rodrigues JJ, Pinheiro PR, De Albuquerque VHC (2018) Effective features to classify big data using social internet of things. IEEE Access 6:24196–24204
Ewees AA, Elaziz MA, Houssein EH (2018) Improved grasshopper optimization algorithm using opposition-based learning. Expert Syst Appl 1–31
Shankar K, Eswaran P (2017) RGB based multiple share creation in visual cryptography with aid of elliptic curve cryptography. China Commun 14(2):118–130
Mahmoud MM, Rodrigues JJ, Ahmed SH, Shah SC, Al-Muhtadi JF, Korotaev VV, De Albuquerque VHC (2018) Enabling technologies on cloud of things for smart healthcare. IEEE Access 6:31950–31967
Rodrigues JJ, Segundo DBDR, Junqueira HA, Sabino MH, Prince RM, Al-Muhtadi J, De Albuquerque VHC (2018) Enabling technologies for the internet of health things. Ieee Access 6:13129–13141
Abdelaziz A, Elhoseny M, Salama AS, Riad AM (2018) A machine learning model for improving healthcare services on cloud computing environment. Measurement 119:117–128
Darwish A, Hassanien AE, Elhoseny M, Sangaiah AK, Muhammad K (2017) The impact of the hybrid platform of internet of things and cloud computing on healthcare systems: opportunities, challenges, and open problems. J Ambient Intell Humaniz Comput 1–16
Neve AG, Kakandikar GM, Kulkarni O (2017) Application of grasshopper optimization algorithm for constrained and unconstrained test functions. Int J Swarm Intell Evol Comput 6(165):2
Shankar K, Lakshmanaprabu SK (2018) Optimal key based homomorphic encryption for color image security aid of ant lion optimization algorithm. Int J Eng Technol 7(9):22–27
Elhoseny M, Yuan X, El-Minir HK, Riad AM (2016) An energy efficient encryption method for secure dynamic WSN. Secur Commun Netw 9(13):2024–2031
Shankar K, Eswaran P (2016) RGB-based secure share creation in visual cryptography using optimal elliptic curve cryptography technique. J Circuits Syst Comput 25(11):1650138
Shankar K, Eswaran P (2016) An efficient image encryption technique based on optimized key generation in ECC using genetic algorithm. Adv Intell Syst Comput Springer 394:705–714
DiazCortes MA, OrtegaSanchez N, Hinojosa S, Oliva D, Cuevas E, Rojas R, Demin A (2018) A multi-level, thresholding method for breast thermograms analysis using dragonfly algorithm. Infrared Phys Technol. https://doi.org/10.1016/j.infrared.2018.08.007
Hinojosa S, Avalos O, Oliva D, Cuevas E, Pajares G, Zaldivar D, Galvez J (2018) Unassisted thresholding based on multi-objective evolutionary algorithms. Knowl Based Syst. https://doi.org/10.1016/j.knosys.2018.06.028
Oliva D, Hinojosa S, Osuna-Enciso V, Cuevas E, Pérez-Cisneros M, Sanchez-Ante G (2017) Image segmentation by minimum cross entropy using evolutionary methods. Soft Comput. https://doi.org/10.1007/s00500-017-2794-1
Oliva D, Hinojosa S, Cuevas E, Pajares G, Avalos O, Gálvez J (2017) Cross entropy based thresholding for magnetic resonance brain images using crow search algorithm. Expert Syst Appl 79:164–180. https://doi.org/10.1016/j.eswa.2017.02.042
Avudaiappan T, Balasubramanian R, Sundara Pandiyan S, Saravanan M, Lakshmanaprabu SK, Shankar K (2018) Medical image security using dual encryption with oppositional based optimization algorithm. J Med Syst 42(11):1–11. https://doi.org/10.1007/s10916-018-1053-z
Shankar K, Eswaran P (2016) A New k out of n secret image sharing scheme in visual cryptography. In: 10th international conference on intelligent systems and control (ISCO). IEEE, pp 369–374
Dhanalakshmi L, Ranjitha S, Suresh HN (2016) A novel method for image processing using particle swarm optimization technique. In: International conference on electrical, electronics, and optimization techniques (ICEEOT). IEEE, pp 3357–3363
Shankar K, Eswaran P (2015) Sharing a secret image with encapsulated shares in visual cryptography. Procedia Comput Sci 70:462–468
Shankar K, Eswaran P (2015) A secure visual secret share (vss) creation scheme in visual cryptography using elliptic curve cryptography with optimization technique. Aust J Basic Appl Sc 9(36):150–163
Shankar K, Eswaran P (2015) ECC based image encryption scheme with aid of optimization technique using differential evolution algorithm. Inte J Appl Eng Res 10(5):1841–1845
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
This article has been retracted. Please see the retraction notice for more detail:https://doi.org/10.1007/s00521-022-08143-y
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Elhoseny, M., Shankar, K., Lakshmanaprabu, S.K. et al. RETRACTED ARTICLE: Hybrid optimization with cryptography encryption for medical image security in Internet of Things. Neural Comput & Applic 32, 10979–10993 (2020). https://doi.org/10.1007/s00521-018-3801-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-018-3801-x