Abstract
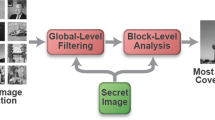
In this paper, we present a new adaptive contourlet-based steganography method that hides secret data in a specific or automatically selected cover image. Our proposed steganography method primarily decomposes the cover image by contourlet transform. Then, every bit of secret data is embedded by increasing or decreasing the value of one coefficient in a block of a contourlet subband. Contourlet coefficients are manipulated relative to their magnitudes to hide the secret data adaptively. In addition to proposing contourlet-based steganography method, this work investigates the effect of cover selection on steganography embedding and steganalysis results. We demonstrate, through the experiments, that choosing suitable cover image by a proper selection measure could help the steganographer reduce detectability of stego images. The proposed technique is examined with some state-of-the-art steganalysis methods, and the results illustrate that an image can successfully hide secret data with average embedding capacity of 0.02 bits per pixel in a random selected cover image. Cover selection improves the embedding capacity up to 0.06 bits per pixel. Several experiments and comparative studies are performed to show the effectiveness of the proposed technique in enhancing the security of stego images, as well as to demonstrate its gain over the previous approaches in literature.
Similar content being viewed by others
References
Raja, K.B., Chowdary, C.R., Venugopal, K.R., Patnaik, L.M.: A secure image steganography using LSB, DCT and compression techniques on raw images. In: Proceeding of 3rd International Conference of Intelligent Sensing and Information, pp. 170–176 (2005)
Martin, A., Sapiro, G., Seroussi, G.: Is image steganography natural? Technical Report. Information Theory Research Group, HP Laboratories Palo Alto (2004)
Westfeld, A.: F5-a steganographic algorithm: high capacity despite better steganalysis. In: Proceedings of 4th International Workshop on Information Hiding (2001)
Sallee, P.: Model-based steganography. In: Proceedings of International Workshop on Digital Watermarking, Korea (2003)
Fridrich, J., Goljan, M., Soukal, D.: Perturbed quantization steganography with wet paper codes. In: Proceedings of ACM Multimedia Workshop, Germany (2004)
Sarkar, A., Solanki, K., Manjunath, B.S.: Further study on YASS: steganography based on randomized embedding to resist blind steganalysis. In: Proceedings of SPIE, vol. 6819, pp. 681917–681917-11 (2008)
Raja, K.B., Vikas, Venugopal, K.R., Patnaik, L.M.: High capacity lossless secure image steganography using wavelets. In: Proceeding of International Conference on Advanced Computing and Communications, pp. 230–235 (2006)
Chan C.K., Cheng L.M.: Hiding data in images by simple LSB substitution. Pattern Recognit. 7(3), 469–474 (2004)
Fridrich, J., Pevny, T., Kodovsky, J.: Statistically undetectable JPEG steganography: dead ends, challenges, and opportunities. In: Proceedings of the Workshop on Multimedia and Security (2007)
Westfeld, A., Pfitzmann, A.: Attacks on steganographic systems. In: Proceedings of 3rd International Workshop Information Hiding (2000)
Solanki, K., Sarkar, A., Manjunath, B.S.: YASS: yet another steganographic scheme that resists blind steganalysis. In: Proceedings of 9th International Workshop on Information Hiding (2007)
Li, B., Shi, Y.Q., Huang, J.: Steganalysis of YASS. In: Proceedings of ACM MM&Sec’08 (2008)
Zhiwei K., Jing L., Yigang H.: Steganography based on wavelet transform and modulus function. J. Syst. Eng. Electron. 18(3), 628–632 (2007)
Sajedi, H., Jamzad, M.: Adaptive steganography method based on contourlet transform. In: Proceedings of 9th International Conference on Signal Processing (2008)
Do M.N., Vetterli M.: The contourlet transform: an efficient directional multiresolution image representation. IEEE Trans. Image Process. 14(12), 2091–2106 (2005)
Kharrazi, M., Sencar, H., Memon, N.: Cover selection for steganograpic embedding. In: Proceedings of ICIP, pp. 117–121 (2006)
Watson, B.A.: DCT quantization matrices visually optimized for individual images, human vision, visual processing and digital display IV. In: Proceedings of SPIE, vol. 1913, pp. 202–216 (2005)
Wang Z., Bovik A., Sheikh H., Simoncelli E.: Perceptual image quality assessment: from error visibility to structural similarity. IEEE Trans. Image Process. 13(4), 600–612 (2004)
Kermani, Z.Z., Jamzad, M.: A robust steganography algorithm based on texture similarity using gabor filter. In: Proceedings of IEEE International Symposium Signal processing and Information Technology, pp. 578–582 (2005)
Sajedi, H., Jamzad, M.: Cover selection steganography method based on similarity of image blocks. In: Proceedings of IEEE 8th CIT Conference, Sydney, Australia (2008)
Do, M., Vetterli, M.: Contourlets: a directional multiresolution image representation. In: Proceedings of IEEE International Conference on Image Processing, vol. 1, pp. 357–360 (2002)
Po, D.D.-Y.: Image modeling in contourlet domain, master’s thesis. University of Illinois, Urbana-Champaign (2003)
Po, D.D.-Y., Do, M.N.: Directional multiscale modeling of images using the contourlet transform. In: Proceedings of IEEE Workshop on Statistical Signal Processing, pp. 262–265 (2003)
Do M.N., Vetterli M.: Rotation invariant texture characterization and retrieval using steerable wavelet-domain hidden markov models. IEEE Trans. Multimed. 4(4), 517–527 (2002)
Fridrich, J.: Feature-based steganalysis for jpeg images and its implications for future design of steganographic schemes. In: Proceedings of 6th Information Hiding Workshop, Toronto (2004)
Lyu, S., Farid, H.: Detecting hidden messages using higher-order statistics and support vector machines. In: Proceedings of 5th International Workshop on Information Hiding (2002)
Pevny, T., Fridrich, J.: Merging markov and DCT features for multi-class JPEG steganalysis. In: Proceedings of SPIE, San Jose, CA (2007)
Chen, C., Shi, Y.Q., Chen, W., Xuan, G.: Statistical moments based universal steganalysis using JPEG-2D array and 2-D characteristic function. In: Proceedings of ICIP, pp. 105–108 (2006)
Wang Y., Moulin P.: Optimized feature extraction for learning-based image steganalysis. IEEE Trans. Inf. Forensics Secur. 2(1), 31–45 (2007)
Xuan, G., Shi, Y.Q., Gao, J., Zou, D., Yang, C., Yang, C., Zhang, Z., Chai, P., Chen, C., Chen, W.: Steganalysis based on multiple features formed by statistical moments of wavelet characteristic functions. In: Proceeding of 7th International Workshop on Information Hiding (2005)
Niimi, M., Noda, H., Kawaguchi, E.: An image embedding in image by a complexity based region segmentation method. In: Proceedings of International Conference on Image Processing, pp. 112–119 (1997)
Jamzad M., Yaghmaee F.: Achieving higher stability in watermarking according to image complexity. Sci. Iran. J. 13(4), 404–412 (2006)
Haller, R.S.: Complexity of real images evaluated by densitometric analysis and by psychophysical scaling. M.Sc. Thesis, University of Arizona (1970)
Seong, Y.K., Choi, Y.H., Choi, T.S.: Scene-based watermarking method for copy protection using image complexity and motion vector amplitude. In: Proceedings of ICASSP, pp. III-409-412 (2004)
Bae S., Paris S., Durand F.: Two-scale tone management for photographic look. ACM Trans. Graph. 25(3), 637–645 (2006)
Fridrich, J., Goljan, G.: Detecting LSB steganography in color and gray-scale images. In: Proceedings of Workshop on Multimedia and security, pp. 27–30 (2001)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sajedi, H., Jamzad, M. Using contourlet transform and cover selection for secure steganography. Int. J. Inf. Secur. 9, 337–352 (2010). https://doi.org/10.1007/s10207-010-0112-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10207-010-0112-3