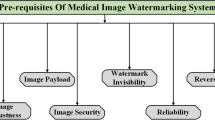
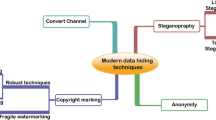
Abstract
The ever-growing numbers of medical digital images and the need to share them among specialists and hospitals for better and more accurate diagnosis require that patients’ privacy be protected. As a result of this, there is a need for medical image watermarking (MIW). However, MIW needs to be performed with special care for two reasons. Firstly, the watermarking procedure cannot compromise the quality of the image. Secondly, confidential patient information embedded within the image should be flawlessly retrievable without risk of error after image decompressing. Despite extensive research undertaken in this area, there is still no method available to fulfill all the requirements of MIW. This paper aims to provide a useful survey on watermarking and offer a clear perspective for interested researchers by analyzing the strengths and weaknesses of different existing methods.






Similar content being viewed by others
References
Kuang LQ, Zhang Y, Han X: A Medical image authentication system based on reversible digital watermarking, in Information Science and Engineering (ICISE), 2009 1st International Conference. pp 1047–1050, 2009.
Bhatnagar G, Jonathan WU QM: Biometrics inspired watermarking based on a fractional dual tree complex wavelet transform. Futur Gener Comput Syst 29(1):182–195, 2013
Pan W, Coatrieux G, Cuppens-Boulahia N, Cuppens F, Roux C: Medical image integrity control combining digital signature and lossless watermarking, in Data Privacy Management and Autonomous Spontaneous Security In: Garcia-Alfaro J, et al Eds. Springer Berlin: Heidelberg, 2010, pp 153–162.
Zain JM, Clarke M: Reversible region of non-interest (RONI) watermarking for authentication of DICOM images. Int J Comput Sci Netw Secur 7(9):19–28, 2007
Wu N-I, Hwang M-S: Data hiding current status and key issues. Int J Netw Secur 4(1):1–9, 2007
Heylena K, Dams T: An image watermarking tutorial tool using matlab. Mathematics of Data/Image Pattern Recognition, Compression, and Encryption with Applications XI, Proc. of SPIE 2008. 7075, 70750D: p. 1–12.
Mohanty SP, Ramakrishnan KR: A dual watermarking technique for images, in Proceedings of the 7th ACM International Multimedia. ACM Press, 1999, pp 49–51.
Memon NA, Chaudhry A, Ahmad M, Keerio ZA: Hybrid watermarking of medical images for ROI authentication and recovery. Int J Comput Math 88(10):2057–2071, 2011
Jabade VS, Gengaje SR: Literature review of wavelet based digital image watermarking techniques. Int J Comp Appl 31(1):28–35, 2011
Memon NA, Gilani SAM: Watermarking of chest CT scan medical images for content authentication. Int J Comput Math 88(2):265–280, 2010
Kaur M, KAUR R: Reversible watermarking of medical images authentication and recovery-a survey. J Inf Oper Manag 3(1):241–244, 2012
Cheddad A, Condell J, Curran K, Mc Kevitt P: Digital image steganography: Survey and analysis of current methods. Signal Process 90(3):727–752, 2010
Mohanty SP: Digital Watermarking : A Tutorial Review. 1999.
Adnan WAW, Hitarn S, Abdul-Karim S, TamJis MR: A review of image watermarking, in Research and Development, 2003. SCORED 2003. Proceedings. Student Conference. pp 381–384, 2003.
Memon NA: Watermarking of medical images for content authentication and copyright protection, in Computer Science and Engineering. 2010, GIK Institute of Engineering Sciences and Technology Topi: Swabi, pp 1–166.
Hajjaji MA, Mtibaa A, Bourennane E-B: A watermarking of medical image : new approach based on “multi-layer” method. Int J Comp Sci Issues (IJCSI) 8(4):33–41, 2011
Le THN, Nguyen KH, Le HB: Literature survey on image watermarking tools, watermark attacks, and benchmarking tools, in Second International Conferences on Advances in Multimedia, IEEE Computer Society, 2010, pp 67–73.
Hanhan AHAM: Digital image watermarking, in Faculty of Engineering Electrical Engineering Department. AN-Najah National University, 2011.
Navas KA, Sasikumar M: Survey of medical image watermarking algorithms, in International Conference: Sciences of Electronic Technologies of Information and Telecommunications. TUNISIA, 2007, pp 1–6.
Wenyin Z, Shih FY: Semi-fragile spatial watermarking based on local binary pattern operators. Opt Commun 284(16–17):3904–3912, 2011
Van Schyndel RG, Tirkel AZ, Osborne CF: A digital watermark, in Image Processing Proceedings. (ICIP), IEEE Int Conf 86–90,1994.
Badran EF, Sharkas MA, Attallah OA: Multiple watermark embedding scheme in wavelet-spatial domains based on ROI of medical images, in Radio Science Conference, NRSC, National, 2009, pp 1–8.
Celik MU, Sharma G, Tekalp AM, Saber E: Lossless gneralized-LSB data embedding. IEEE Trans Image Process 14(2):253–266, 2005
Agung BWR, Adiwijaya, Permana FP: Medical image watermarking with tamper detection and recovery using reversible watermarking with LSB modification and run length encoding (RLE) compression, in Communication, Networks and Satellite (ComNetSat), 2012 IEEE International Conference. pp 167–171, 2012.
Dehkordi AB, Esfahani SN, Avanaki AN: Robust LSB watermarking optimized for local structural similarity, in Electrical Engineering (ICEE), 19th Iranian Conference. pp 1–1, 2011.
Bamatraf A, Ibrahim R, Salleh MNBM: Digital watermarking algorithm using LSB, in Computer Applications and Industrial Electronics (ICCAIE), 2010 International Conference. pp 155–159, 2010.
Chang JD, Chen BH, Tsai CS: LBP-based fragile watermarking scheme for image tamper detection and recovery, in Next-Generation Electronics (ISNE), 2013 IEEE International Symposium. pp 173–176, 2013.
Shu, L., F. Wei, A.C.S. Chung, and Y. Dit-Yan, Facial expression recognition using advanced local binary patterns, yallis entropies and global appearance features, in Image Processing, 2006 I.E. Int Conf 665–668, 2006.
Ahonen T, Hadid A, Pietikäinen M: Face recognition with local binary patterns. In T. Pajdla, J. Matas (Eds.) Computer Vision - ECCV 2004, Springer Berlin Heidelberg. pp 469–481, 2004.
Wenhua M, Lei H, Changping L: Advanced local binary pattern descriptors for crowd estimation. in Computational Intelligence and Industrial Application, 2008. PACIIA ’08. Pacific-Asia Workshop on. 2008.
Ni Z, Shi Y-Q, Ansari N, Su W: Reversible data hiding. IEEE Trans Circ Syst V Technol 16(3):354–362, 2006
Solachidis V, Pitas L: Circularly symmetric watermark embedding in 2-D DFT domain. Image Process IEEE Trans 10(11):1741–1753, 2001
Kaushik AK: A novel approach for digital watermarking of an image using DFT. Int JElectronComp Sci Eng 1(1):35–41, 2012
Cedillo-Hernandez M, Garcia-Ugalde F, Nakano-Miyatake M, Perez-Meana H: Robust watermarking method in DFT domain for effective management of medical imaging. SIViP pp 1–16, 2013.
Ramkumar M, Akansu AN, Alatan AA: A robust data hiding scheme for images using DFT, in Image Processing, 1999. ICIP 99. Proceedings. 1999 International Conference. pp 211–215, 1999
Ruanaidh JJKO, Dowling WJ, Boland FM: Phase watermarking of digital images, in Image Processing, 1996. Proc Int Conf pp. 239–242,1996.
Das S. Kundu M: Hybrid Contourlet-DCT Based Robust Image Watermarking Technique Applied to Medical Data Management. In: Kuznetsov S, Mandal D, Kundu M, Pal S (Eds.) Pattern Recognition and Machine Intelligence, Springer Berlin Heidelberg. pp 286–292, 2011.
Kundur D, Hatzinakos D: Digital watermarking for telltale tamper proofing and authentication. Proc IEEE 87(7):1167–1180, 1999
Hernandez JR, Amado M, Perez-Gonzalez F: DCT-domain watermarking techniques for still images: detector performance analysis and a new structure. IEEE Trans Image Process 9(1):55–68, 2000
Yang B, Schmucker M, XiaMu N, Busch C, Sun S: Reversible image watermarking by histogram modification for integer DCT coefficients, in Multimedia Signal Processing, IEEE 6th Workshop pp 143–146, 2004.
Yang B, Schmucker M, Funk W, Busch C, Sun S: Integer DCT-based reversible watermarking for images using compounding technique. Proc SPIE 5306:405–415, 2004
Rohani M, Avanaki AN: A watermarking method based on optimizing SSIM index by using PSO in DCT domain, in Computer Conference, 2009. CSICC 2009. 14th International CSI pp 418–422,2009.
Langelaar GC, Setyawan I, Lagendijk RL: Watermarking digital image and video data. A state-of-the-art overview. Signal Proc Mag IEEE 17(5):20–46, 2000
Ali M, Ahn CW, Pant M: A robust image watermarking technique using SVD and differential evolution in DCT domain. Opt Int J Light Electron Opt 125(1):428–434, 2014
Li J, Du W, Bai Y, Chen YW: 3D-DCT based zero-watermarking for medical volume data robust to geometrical attacks, in Wireless Communications and Applications. In: Sénac P, Ott M, Seneviratne A Eds. Springer Berlin: Heidelberg, 2012, pp 433–444.
Hyung-Kyo L, Hee-Jung K, Ki-Ryong K, Jong-Keuk L: ROI medical image watermarking using DWT and bit-plane, in Asia-Pacific Conference on Communications, Perth, Western Australia p. 512–515,2005.
Long M, Changjun L, Shuni S: Digital watermarking of spectral images using DWT-SVD, in Communications, Circuits and Systems Proceedings, 2006 International Conference on p. 15–18,2006.
Kasmani SA, Naghsh-Nilchi A: A new robust digital image watermarking technique based on joint DWT-DCT transformation, in Convergence and Hybrid Information Technology, 2008. ICCIT ’08. Third International Conference on, 2008, pp 539–544.
Wang M-S, Chen W-C: A hybrid DWT-SVD copyright protection scheme based on k-means clustering and visual cryptography. Comp Stand Interfaces 31(4):757–762, 2009
Kalra GS, Talwar R, Sadawarti H: Robust blind digital image watermarking using DWT and dual encryption technique, in Computational Intelligence, Communication Systems and Networks (CICSyN), 2011 Third International Conference on 225–230,2011.
Keyvanpour M-R, Merrikh-Bayat F: Robust dynamic block-based image watermarking in DWT domain. Procedia Comput Sci 3:238–242, 2011
Makhloghi M, Tab FA, Danyali H: A new robust blind DWT-SVD based digital image watermarking, in Electrical Engineering (ICEE), 2011 19th Iranian Conference on. Tehran pp 1–5,2011.
Giakoumaki A, Pavlopoulos S, Koutouris D: A medical image watermarking scheme based on wavelet transform, in Engineering in Medicine and Biology Society, 2003. Proceedings of the 25th Annual International Conference of the IEEE. pp 856–859, 2003.
Wen-Nung L, Tze-Liang H, Guo-Shiang L: Verification of image content integrity by using dual watermarking on wavelets domain, in Image Processing, 2003. ICIP 2003. Proceedings. Int Conf pp II-487-490,2003.
Guorong X, Chengyun Y, Yizhan Z, Shi YQ, Zhicheng N: Reversible data hiding based on wavelet spread spectrum, in Multimedia Signal Processing, 2004 I.E. 6th Workshop on pp 211–214,2004.
Kaarna A, Parkkinen J: Multiwavelets in watermarking spectral images, in Geoscience and Remote Sensing Symposium, 2004. IGARSS ’04. Proceedings. 2004 I.E. Int pp 3225–3228,2004.
Kamstra L, Heijmans HJAM: Reversible data embedding into images using wavelet techniques and sorting. Image Process IEEE Trans 14(12):2082–2090, 2005
Na L, Xiaoshi Z, Yanling Z, Huimin W, Shifeng L: Robust algorithm of digital image watermarking based on Discrete Wavelet Transform, in Electronic Commerce and Security, 2008 Int Symp 942–945,2008.
Lin T-C, Lin C-M: Wavelet-based copyright-protection scheme for digital images based on local features. Inf Sci 179(19):3349–3358, 2009
Lin WH, Wang YR, Horng SJ: A block-based watermarking method using wavelet coefficient quantization, in Algorithms and Architectures for Parallel Processing. In: Hua A, Chang SL Eds. Springer Berlin: Heidelberg, 2009, pp 156–164.
Memon NA, Gilani SAM: Adaptive data hiding scheme for medical images using integer wavelet transform, in Emerging Technologies, 2009. ICET 2009. International Conference on. Islamabad, 2009, pp. 221–224.
Youngseock L, Jihah N, Jongweon K: Digital image watermarking using bidimensional empirical mode decomposition in wavelet domain, in Multimedia, 2009. ISM ’09. 11th IEEE International Symposium on pp. 583–588,2009.
Arsalan M, Malik SA, Khan A: Intelligent reversible watermarking in integer wavelet domain for medical images. J Syst Softw 85(4):883–894, 2012
Agreste S, Puccio L: Wavelet-based watermarking algorithms: theory, applications and critical aspects. Int J Comput Math 88(9):1885–1895, 2011
Giakoumaki A, Pavlopoulos S, Koutsouris D: Multiple image watermarking applied to health information management. Inf Technol Biomed IEEE Trans 10(4):722–732, 2006
Selesnick IW, Baraniuk RG, Kingsbury NC: The dual-tree complex wavelet transform. Signal Process Mag IEEE 22(6):123–151, 2005
Kingsbury N: The dual-tree complex wavelet transform: a new efficient tool for image restoration and enhancement, in Proc. EUSIPCO pp 319–322,1998.
Kingsbury N: The dual-tree complex wavelet transform: a new technique for shift invariance and directional filters, in Proc. 8th IEEE DSP Workshop: Bryce Canyon, 1998, pp 319–322.
Rahimi F, Rabbani H: A dual adaptive watermarking scheme in contourlet domain for DICOM images. BioMed Eng OnLine 10(1):1–18, 2011
Do MN, Vetterli M: Contourlets: a directional multiresolution image representation, in Image Processing. 2002. Proceedings. 2002 Int Conf pp I-357-360, 2002.
Do MN, Vetterli M: The contourlet transform: an efficient directional multiresolution image representation. Image Process IEEE Trans 14(12):2091–2106, 2005
Khalighi S, Tirdad P, Rabiee HR: A contourlet-based image watermarking scheme with high resistance to removal and geometrical attacks. EURASIP J Adv Signal Process 2010:1–13, 2010
Aslantas V: An optimal robust digital image watermarking based on SVD using differential evolution algorithm. Opt Commun 282(5):769–777, 2009
Mansouri A, Mahmoudi A: Aznaveh, and F. Torkamani Azar, Secure Digital Image Watermarking Based on SVD-DCT Advances in Computer Science and Engineering. In: Sarbazi-Azad H, et al Eds. Springer Berlin: Heidelberg, 2009, pp 645–652.
Al-Nuaimy W, El-Bendary MAM, Shafik A, Shawki F, Abou-El-azm AE, El-Fishawy NA, Elhalafawy SM, Diab SM, Sallam BM, Abd FE: El-Samie, and H.B. Kazemian, An SVD audio watermarking approach using chaotic encrypted images. Digit Signal Proc 21(6):764–779, 2011
Tsai H-H, Jhuang Y-J, Lai Y-S: An SVD-based image watermarking in wavelet domain using SVR and PSO. Appl Soft Comput 12(8):2442–2453, 2012
Ali M, Ahn CW: An optimized watermarking technique based on self-adaptive DE in DWT–SVD transform domain. Signal Process 94:545–556, 2014
Liu R, Tan T: An SVD-based watermarking scheme for protecting rightful ownership. IEEE Trans Multimed 4(1):121–128, 2002
Lei BY, Soon IY, Li Z: Blind and robust audio watermarking scheme based on SVD–DCT. Signal Process 91(8):1973–1984, 2011
Lai C-C: An improved SVD-based watermarking scheme using human visual characteristics. Opt Commun 284(4):938–944, 2011
Patra JC, Phua JE, Bornand C: A novel DCT domain CRT-based watermarking scheme for image authentication surviving JPEG compression. Digit Signal Proc 20(6):1597–1611, 2010
Mansouri A, Mahmoudi Aznaveh A, Torkamani Azar F: SVD-based digital image watermarking using complex wavelet transform. Sadhana 34(3):393–406, 2009
Faragallah OS: Efficient video watermarking based on singular value decomposition in the discrete wavelet transform domain. Int J Electron Commun (AEU) 67(3):189–196, 2013
Gonzalez RC, Woods RE: Digital image processing, 3rd Edition. Prentice-Hall, Inc,2006.
Muharemagic E, Furht B: Survey of watermarking techniques and applications. 2006 pp 1–30.
Guo X, Zhuang TG: A region-based lossless watermarking scheme for enhancing security of medical data. J Digit Imaging 22(1):53–64, 2009
Chang C-Y, Wang H-J, Pan S-W: A robust DWT-based copyright verification scheme with Fuzzy ART. J Syst Softw 82(11):1906–1915, 2009
Gunjal BL, Mali SN: ROI Based embedded watermarking of medical images for secured communication in telemedicine. Int J Comp Commun Eng pp 293–298,2012
Kutter M, Petitcolas FAP: A fair benchmark for image watermarking systems. Electronic Imaging ’99. Security and Watermarking of Multimedia Contents: Sans Jose, 1999, 3657:226–239.
Al-Qershi OM, Khoo BE: Authentication and data hiding using a hybrid ROI-based watermarking scheme for DICOM images. J Digit Imaging 24(1):114–125, 2011
Zain J, Baldwin L, Clarke M: Reversible watermarking for authentication of DICOM images, in Proceedings of the 26th Annual International Conference of the IEEE Engineering in Medicine and Biology Society pp 3237–3240,2004.
Lin C-H, Yang C-Y, Chang C-W: Authentication and protection for medical image, vol. 6422. Springer, Berlin Heidelberg, 2010, pp 278–287
Al-Qershi OM, Khoo BE: High capacity data hiding schemes for medical images based on difference expansion. J Syst Softw 84(1):105–112, 2011
Tian J: Reversible data embedding using a difference expansion. Circ Syst V Technol IEEE Trans 13(8):890–896, 2003
Yeo D-G, Lee H-Y, Kim BM: High capacity reversible watermarking using differential histogram shifting and predicted error compensation. J Electron Imaging 20(1):013001–1-11, 2011
Wakatani A: Digital watermarking for ROI medical images by using compressed signature image, in System Sciences, 2002. HICSS. Proceedings of the 35th Annual Hawaii International Conference on. pp 2043–2048,2002.
Viswanathan P, Krishna PV: Fusion of cryptographic watermarking medical image system with reversible property, in Computer Networks and Intelligent Computing.In: Venugopal KR, Patnaik LM Eds. Springer Berlin: Heidelberg, 2011, pp 533–540.
Acknowledgments
The authors would like to acknowledge Universiti Teknologi Malaysia (UTM) for providing facilities and resources to get this work done. Also many thanks to the Research Management Center (RMC) of Universiti Teknologi Malaysia as well as Malaysian International Scholarship (MIS) for funding and supporting this research and providing excellent research environment in which this work was conducted and the scientific research targets fully accomplished.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Mousavi, S.M., Naghsh, A. & Abu-Bakar, S.A.R. Watermarking Techniques used in Medical Images: a Survey. J Digit Imaging 27, 714–729 (2014). https://doi.org/10.1007/s10278-014-9700-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10278-014-9700-5