Abstract
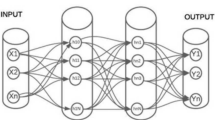
Cloud environment is an assembly of resources for furnishing on-demand services to cloud customers. Here access to cloud environment is via internet services in which data stored on cloud environment are easier to both internal and external intruders. To detect intruders, various intrusion detection systems and authentication systems was proposed in earlier researches which are primarily ineffective. Many existing researchers were concentrated on machine learning approaches for detecting intrusions using fuzzy clustering, artificial neural network, support vector machine, fuzzy with neural network and etc., which are not furnishing predominant results based on detection rate and false negative rates. Our proposed system directed on intrusion detection system and it uses cloudlet controller, trust authority and virtual machine management in cloud environment. We propose two novel algorithms such as (i) packet scrutinization algorithm which examines the packets from the users and (ii) hybrid classification model called “NK-RNN” which is a combination of normalized K-means clustering algorithm with recurrent neural network. For preventing the user from intruders, we propose a one time signature for cloud user in order to access the data on cloud environment. Our proposed classifier effectively detects the intruders which are experimentally proved by comparing with existing classification models. Thus our proposed results are expressed by packet loss ratio, average packet delay, throughput, detection rate, false positive rate and false negative rate.








Similar content being viewed by others
References
Mehmood, Y., Shibli, M.A., Habiba, U., Masood, R.: Intrusion detection system in cloud computing: challenges and opportunities. In: IEEE 2nd National Conference on Information Assurance (NCIA), pp. 59–66 (2013)
Manogarana, G., Thotab, C., Vijay Kumar, M.: MetaCloudDataStorage architecture for big data security in cloud computing. In: 4th International Conference on Recent Trends in Computer Science & Engineering, Elsevier, pp. 128–133 (2016)
Jin, H., Xiang, G., Zou, D., Wu, S., Zhao, F., Li, M., Zhengm, W.: A VMM-based intrusion prevention system in cloud computing environment. J. Supercomput. 66, 1133–1151 (2011)
Abazari, F., Analoui, M., Takabi, H.: Effect of anti-malware software on infectious nodes in cloud environment. Comput. Security 58, 139–148 (2015)
Pandeeswari, N., Kumar, G.: Anomaly detection system in cloud environment using fuzzy clustering based ANN. Mobile Netw. Appl. 21(3), 494–505 (2015)
Xing, T., Xiong, Z., Huang, D., Medhi, D.: SDNIPS: enabling software-defined networking based intrusion prevention system in clouds. In: CNSM Short Paper and Workshop, pp. 308–311 (2014)
Le, A., Loo, J., Chai, K.K., Mahdi, A.: A specification-based IDS for detecting attacks on RPL-based network topology. MDPI J. 7(25), 1–19 (2016)
Deshpande, P., Sharma, S.C., Peddoju, S.K., Junaid, S.: HIDS: a host based intrusion detection system for cloud computing environment. Int. J. Syst. Assur. Eng. Manag. doi:10.1007/s13198-014-0277-7 (2014)
Tolupa, S., Nischenko, V.: Analysis of intrusion detection systems TAXONOMY in the CONTExt of current development level of information systems. Exclus. J. 2, 1–6 (2015)
Raja, S., Ramaiah, S.: An efficient fuzzy-based hybrid system to cloud intrusion detection. Int. J. Fuzzy Syst. 19(1), 62–77 (2016)
Ramachandran, M.: Software security requirements management as an emerging cloud computing service. Int. J. Inf. Manag. 36, 580–590 (2016)
Pasquale, L., Hanvey, S., Mcgloin, M., Nuseibeh, B.: Adaptive evidence collection in the cloud using attack scenarios. Comput. Soc. 59(C), 236–256 (2016)
Chen, Y., Member, Y.C., Cao, Q., Yang, X.: PacketCloud: a cloudlet-based open platform for in-network services. IEEE Trans. Parallel Distrib. Syst. 27(4). doi:10.1109/TPDS.2015.2424222 (2015)
El Mir, I., Haqiq, A., Kim, D.S.: Performance analysis and security based on intrusion detection and prevention systems in cloud data centers. Adv. Intell. Syst. Comput. 552, 456–465 (2016)
Patel, S.K., Sonker, A.: Rule-based network intrusion detection system for port scanning with efficient port scan detection rules using snort. Int. J. Future Gen. Commun. Netw. 9(6), 339–350 (2016)
Keegan, N., Ji, S.-Y., Chaudhary, A., Concolato, C., Yu, B., Jeong, D.H.: A survey of cloud-based network intrusion detection analysis. Hum. Centr. Comput. Inf. Sci. 6, 19 (2016)
Labib, K.: Computer security and intrusion detection. The ACM Student Magazine (2004)
Deshpande, P., Sharma, S.C., Sateeshkumar, P.: Security threats in cloud computing. In: IEEE International Conference on Computing, Communication and Automation, pp. 632–636 (2015)
Gupta, S., Kumar, P.: Profile and back off based distributed NIDS in cloud. Wireless Pers. Commun. 94(4), 2879–2900 (2016)
Patel, A., Taghavi, M., Bakhtiyari, K., Junior, J.C.: An intrusion detection and prevention system in cloud computing: a systematic review. J. Netw. Comput. Appl. 36(1), 25–41 (2013)
Carlin, A., Hammoudeh, M., Aldabbas, O.: Intrusion detection and countermeasure of virtual cloud systems—state of the art and current challenges. Int. J. Adv. Comput. Sci. Appl. 6(6) (2015). doi:10.14569/IJACSA.2015.060601
Kumar, U., Gohil, B.N.: A survey on intrusion detection systems for cloud computing environment. Int. J. Comput. Appl. 109(1), 6–15 (2015)
Zargar, S.T., Joshi, J., Tipper, D.: A survey of defense mechanisms against distributed denial of service (DDoS) flooding attacks. IEEE Commun. Surv. Tutorials 15(4), 2046–2069 (2013)
Cerroni, W., Moro, G., Pasolini, R., Ramilli, M.: Decentralized detection of network attacks through P2P data clustering of SNMP data. Comput. Security 52, 1–16 (2015)
Osanaiye, O., Kim-Kwang, R.C., Dlodlo, M.: Distributed denial of service (DDoS) resilience in cloud: review and conceptual cloud DDoS mitigation framework. J. Netw. Comput. Appl. 67, 147–165 (2016)
Zineddine, M.: Vulnerabilities and mitigation techniques toning in the cloud: a cost and vulnerabilities coverage optimization approach using Cuckoo search algorithm with Lévy flights. Comput. Security 48, 1–8 (2015)
Duessel, P., Gehl, C., Flegel, U., Dietrich, S., Meier, M.: Detecting zero-day attacks using context-aware anomaly detection at the application-layer. J. Netw. Comput. Appl. 16(5), 475–490 (2016)
Alshehry, B., Allen, W.: Proactive approach for the prevention of DDoS attacks in cloud computing environments. In: Applied Computing and Information Technology. Springer, Cham, pp. 119–133 (2016)
Ranjan, N., Ekhlasur Rahman, Md., Uddin, M.S.: Generation and verification of digital signature with two factor authentication. In: IEEE International Workshop on Computational Intelligence, pp. 131–135 (2016)
Yu, Z., Zhang, W., Dai, A.: A trusted architecture for virtual machines on cloud servers with trusted platform module and certificate authority. J. Signal Process. Syst. 86(2—-3), 327–336 (2017)
Dawoud, M.M., Ebrahim, G.A., Youssef, S.A.: A cloud computing security framework based on cloud security trusted authority, pp. 133–138. In: Proceedings of the 10th International Conference on Informatics and Systems. ACM Digital Library (2016)
Sadhasivan, D.K., Balasubramanian, K.: A fusion of multiagent functionalities for effective intrusion detection system. Security Commun. Netw. 2017. doi:10.1155/2017/6216078 (2017)
Negi, P., Mishra, A., Gupta, B.B.: Enhanced CBF packet filtering method to detect DDoS attack in cloud computing environment. Cryptography and Security, Cornell University Library, pp. 1– 5 (2013)
Kim, J., Kim, H.: Applying recurrent neural network to intrusion detection with hessian free optimization. In: International Workshop on Information Security Applications, pp. 357–369. Springer, Cham (2016)
Javed, A., Larijani, H., Ahmadinia, A., Emmanuel, R.: Comparison of the robustness of RNN, MPC, and ANN controller for residential heating system. In: Fourth International Conference on Big Data and Cloud Computing (IEEE), pp. 604–612 (2014)
Hong, M., Zhao, W., Wang, P.: Homomorphic encryption scheme based on elliptic curve cryptography for privacy protection of cloud computing. In: 2nd International Conference on Big Data Security on Cloud (IEEE), pp. 152–157 (2016)
Chintawar, N.N., Gajare, S.J., Fatak, S.V., Shinde, S.S., Virkar, G.: Enhancing cloud data security using elliptical curve cryptography. Int. J. Adv. Res. Comput. Commun. Eng. 5(3), 1–4 (2016)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Balamurugan, V., Saravanan, R. Enhanced intrusion detection and prevention system on cloud environment using hybrid classification and OTS generation. Cluster Comput 22 (Suppl 6), 13027–13039 (2019). https://doi.org/10.1007/s10586-017-1187-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-017-1187-7