Abstract
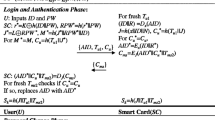
Recently Lee and Liu proposed an efficient password based authentication and key agreement scheme using smart card for the telecare medicine information system [J. Med. Syst. (2013) 37:9933]. In this paper, we show that though their scheme is efficient, their scheme still has two security weaknesses such as (1) it has design flaws in authentication phase and (2) it has design flaws in password change phase. In order to withstand these flaws found in Lee-Liu’s scheme, we propose an improvement of their scheme. Our improved scheme keeps also the original merits of Lee-Liu’s scheme. We show that our scheme is efficient as compared to Lee-Liu’s scheme. Further, through the security analysis, we show that our scheme is secure against possible known attacks. In addition, we simulate our scheme for the formal security verification using the widely-accepted AVISPA (Automated Validation of Internet Security Protocols and Applications) tool to show that our scheme is secure against passive and active attacks.





Similar content being viewed by others
References
Aumasson, J. P., Henzen, L., Meier, W., and Plasencia, M. N., Quark: a lightweight hash. In: Workshop on Cryptographic Hardware and Embedded Systems (CHES 2010), LNCS. Vol. 6225, pages 1–15, 2010.
AVISPA. automated validation of internet security protocols and applications. http://www.avispa-project.org/. Accessed on January 2013.
AVISPA. AVISPA web tool. http://www.avispa-project.org/web-interface/expert.php/. Accessed on April 2013.
Basin, D., Modersheim, S., and Vigano, L., OFMC: A symbolic model checker for security protocols. Int. J. Inf. Secur. 4(3):181–208, 2005.
Chang, Y.-F., Yu, S.-H., and Shiao, D.-R., An uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J. Med. Syst., 37:9902, 2013.
Das, A. K., Analysis and improvement on an efficient biometricbased remote user authentication scheme using smart cards. IET Inf. Secur. 5(3):145–151, 2011.
Das, A. K., A random key establishment scheme for multi-phase deployment in large-scale distributed sensor networks. Int. J. Inf. Secur. 11(3):189–211, 2012.
Das, A. K., A secure and effective user authentication and privacy preserving protocol with smart cards for wireless communications. Netw. Sci. 2(1–2):12–27, 2013.
Das, A. K., Chatterjee, S., and Sing, J. K., A novel efficient access control scheme for large-scale distributed wireless sensor networks. Int. J. Found. Comput. Sci. (In press).
Das, A. K., and Goswami, A., A secure and efficient Uniquenessand-Anonymity-Preserving remote user authentication scheme for connected health care. J. Med. Syst. 37(3):1–16, 2013.
Das, A. K., Massand, A., and Patil, S., A novel proxy signature scheme based on user hierarchical access control policy. J. King Saud University—Comput. Inform. Sci. 25(2):219–228, 2013.
Das, A. K., Paul, N. R., and Tripathy, L., Cryptanalysis and improvement of an access control in user hierarchy based on elliptic curve cryptosystem. Inf. Sci. 209:80–92, 2012.
Das, M. L., Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 8(3):1086–1090, 2009.
Das, M. L., Saxena, A., and Gulati, V. P., A dynamic ID-based remote user authentication scheme. IEEE Trans. Consum. Electron. 50(2):629–631, 2004.
Dolev, D., and Yao, A., On the security of public key protocols. IEEE Trans. Inf. Theory 29(2):198–208, 1983.
He, D., Chen, J., and Zhang, R., A more secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1989–1995, 2012.
Jaspher, G., Kathrine, W., Kirubakaran, E., and Prakash, P., Smart card based remote user authentication schemes: a survey. Procedia Eng. 38:1318–1326, 2012.
Khan, M. K., Kim, S.-K., and Alghathbar, K., Cryptanalysis and security enhancement of a ‘more efficient & secure dynamic IDbased remote user authentication scheme’. Comput. Commun. 34(3):305–309, 2011.
Kocher, P., Jaffe, J., and Jun, B., Differential power analysis. In: Proceedings of Advances in Cryptology–CRYPTO’99, LNCS. Vol. 1666, pages 388–397, 1999.
Lee, T.-F., and Liu, C.-M., A secure smart-card based authentication and key agreement scheme for telecare medicine information systems. J. Med. Syst. 37(3), 2013.
Madhusudhan, R., and Mittal, R. C., Dynamic ID-based remote user password authentication schemes using smart cards: A review. J. Netw. Comput. Appl. 35(4):1235–1248, 2012.
Manuel, S., Classification and generation of disturbance vectors for collision attacks against SHA-1. Des. Codes Crypt. 59(1–3):247–263, 2011.
Messerges, T. S., Dabbish, E. A., and Sloan, R. H., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 51(5):541–552, 2002.
Rivest, R. L., Shamir, A., and Adleman, L. M., A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 21:120–126, 1978.
Sarkar, P., A simple and generic construction of authenticated encryption with associated data. ACM Trans. Inf. Syst. Secur. 13(4):33, 2010.
Stallings, W., Cryptography and Network Security: Principles and Practices, 3rd edn. Prentice Hall, Englewood Cliffs, 2003
Secure Hash Standard. FIPS PUB 180-1, National Institute of Standards and Technology (NIST), U. S. Department of Commerce, April 1995.
Stinson, D. R., Some observations on the theory of cryptographic hash functions. Des. Codes Crypt. 38(2):259–277, 2006.
Wang, Y.-Y., Liu, J.-Y., Xiao, F.-X., and Dan, J., A more efficient and secure dynamic ID-based remote user authentication scheme. Comput. Commun. 32(4):583–585, 2009.
Wei, J., Hu, X., and Liu, W., An improved authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3597–3604, 2012.
Wu, Z. Y., Lee, Y.-C., Lai, F., Lee, H.-C., and Chung, Y.-F., A secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1529–1535, 2012.
Zhu, Z., An efficient authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3833–3838, 2012.
Acknowledgments
The authors would like to acknowledge the many helpful suggestions of the anonymous reviewers, which have improved the content and the presentation of this paper.
Author information
Authors and Affiliations
Corresponding author
Additional information
Conflict of interests
The authors declare that they have no conflict of interest.
Rights and permissions
About this article
Cite this article
Das, A.K., Bruhadeshwar, B. An Improved and Effective Secure Password-Based Authentication and Key Agreement Scheme Using Smart Cards for the Telecare Medicine Information System. J Med Syst 37, 9969 (2013). https://doi.org/10.1007/s10916-013-9969-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-013-9969-9