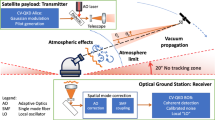
Abstract
The transmission security between ground station and satellite is challenging. Some existing multistep algorithms leave lots of loopholes for eavesdropping and attacking in satellite-to-ground communication. For high security, optical communication is a promising solution. In this paper, we propose a control code multiple encryption algorithm (CCMEA) for the single-photon-transmission between satellite and ground station. CCMEA can utilize the control code to respectively encrypt three cognitive optimization sections: loop iteration, polarization coding and order rearrangement, and simulation shows that CCMEA can realize one step transmission to decrease loopholes compared with multistep encryption algorithm. In addition, we design a security detection method by combining the decoy photon analysis and the quantum bit error rate (QBER) analysis. The numerical results show that CCMEA can reduce the security threshold by 27% compared with multistep encryption algorithm of BB84 scheme. Finally, for satellite-to-ground communication, we construct an analytic QBER model on CCMEA with four factors: quantum channel transmission rate, single-photon acquisition probability, measurement factor and data filtering factor. The result demonstrates the effectiveness of CCMEA on satellite-to-ground communication.



















Similar content being viewed by others
References
Jia M, Liu X, Gu X, Guo Q (2017) Joint cooperative spectrum sensing and channel selection optimization for satellite communication systems based on cognitive radio. Int J Satell Commun Netw 35(2):139
Chen Y, Zhao N, Ding Z, Alouini M (2018) Multiple UAVs as Relays: Multi-Hop Single Link Versus Multiple Dual-Hop Links. IEEE Trans Wirel Commun 17(9):6348
Zhao N, Cheng F, Yu FR, Tang J, Chen Y, Gui G, Sari H (2018) Caching UAV Assisted Secure Transmission in Hyper-Dense Networks Based on Interference Alignment. IEEE Trans Commun 66(5):2281
Cheng F, Zhang S, Li Z, Chen Y, Zhao N, Yu FR, Leung VCM (2018) UAV Trajectory Optimization for Data Offloading at the Edge of Multiple Cells. IEEE Trans Veh Technol 67(7):6732
Jia M, Gu X, Guo Q, Xiang W, Zhang N (2016) Broadband Hybrid Satellite-Terrestrial Communication Systems Based on Cognitive Radio toward 5G. IEEE Wirel Commun 23(6):96
Zhao Y, Xie L, Chen H, Wang K (2017) Ergodic Channel Capacity Analysis of Downlink in the Hybrid Satellite-Terrestrial Cooperative System. Wirel Pers Commun 96(3):3799
Li M, Hong Y, Zeng C, Song Y, Zhang X (2018) Investigation on the UAV-to-satellite optical communication systems. IEEE J Select Areas Commun 36(99):1
Cao Y, Zhao N, Yu FR, Jin M, Chen Y, Tang J, Leung VCM (2018) Optimization or Alignment: Secure Primary Transmission Assisted by Secondary Networks. IEEE J Sel Areas Commun 36(4):905
Deng FG, Li XH, Li CY, Zhou P, Zhou HY (2006) Quantum secure direct communication network with Einstein Podolsky Rosen pairs. Phys Lett A 359(5):359
Deng FG, Gui LL, Liu XS (2003) Two-step quantum direct communication protocol using the Einstein-Podolsky-Rosen pair block. Phys Rev A 68(4):113
Salih H, Li ZH, Al-Amri M, Zubairy MS (2013) Protocol for direct counterfactual quantum communication. Phys Rev Lett 110(17):170502
Gao F, Qin SJ, Wen QY, Zhu FC (2010) Cryptanalysis of multiparty controlled quantum secure direct communication using Greenberger Horne Zeilinger state. Opt Commun 283(1):192
Patwardhan S, Moulick SR, Panigrahi PK (2016) Efficient Controlled Quantum Secure Direct Communication Protocols. Int J Theor Phys 55(7):1
Liu WJ, Chen HW, Liu JF, Liu ZH (2009) Three-dimension single photon quantum secure direct communication based on mutual authentication. J Cent South Univ 40(1):309
Zang P, Tulin YI, Song RY, Jiang Y, School HN (2017) Controlled Teleportation of 3 Particle GHZ State via 2 EPR Pairs. Journal of Anhui Normal University 40(3):242
Zhao X, Li J, Niu P, Ma H, Ruan D (2017) Two-step quantum secure direct communication scheme with frequency coding. Chin Phys B 26(3):231
Tan X, Zhang X, Liang C (2014) Multi-party Quantum Secure Direct Communication. In: International Conference on P2P, pp 251–255
Li HW, Xu ZM, Yin ZQ (2018) Quantum Key Distribution in the Presence of the Intercept-Resend with Faked States Attack. Quantum Inf Process 17(10):257
Howard M (2015) . Phys Rev A 91(4):042103
Behzadi N, Ahansaz B (2017) Effects of Oscillatory Deformations on the Coherent and Incoherent Quantum Transport. Int J Theor Phys 56(11):3441
Yang YG, Sun SJ, Zhao QQ (2015) Trojan-horse attacks on quantum key distribution with classical Bob. Quantum Inf Process 14(2):681
Vinay SE, Kok P (2018) Extended analysis of the Trojan-horse attack in quantum key distribution. Phys Rev A 97(4):042335
Sajeed S, Minshull C, Jain N, Makarov V (2017) Invisible Trojan-horse attack. Sci Rep 7(1):8403
Hong-Xin LI, Chi YG, Han Y, Yan B, Wang W (2018) . Analysis on Photon-number-splitting Attack Against Decoy-state Quantum Key Distribution Schemes. Journal of Cryptologic Research 5(1):1
Kakkar A, Navarro JR, Schatz R, Pang X, Ozolins O, Nordwall F, Zibar D, Jacobsen G, Popov S (2017) Influence of lasers with non-white frequency noise on the design of coherent optical links. In: 2017 Optical Fiber Communications Conference and Exhibition, pp. 1–3
Cao J, Zhao X, Liu W, Gu H (2017) Performance analysis of a coherent free space optical communication system based on experiment. Opt Express 25(13):15299
Deng F, Long G (2004) Secure direct communication with a quantum one-time pad. Physics 69(5):521
Wang C, Deng FG, Li YS, Liu XS, Long GL (2005) Quantum secure direct communication with high-dimension quantum superdense coding. Phys Rev A 71(4):44305
Wang C, Deng FG, Long GL (2005) Multi-step quantum secure direct communication using multi-particle Green-Horne-Zeilinger state. Opt Commun 253(1):15
Kielpinski D, Monroe C, Wineland DJ (2002) Architecture for a large-scale ion-trap quantum computer. Nature 417(6890):709
Birnbaum KM, Boca A, Miller R, Boozer AD, Northup TE, Kimble HJ (2005) Photon blockade in an optical cavity with one trapped atom. Nature 436(7047):87
Jia M, Liu X, Yin Z, Guo Q, Gu X (2017) Joint cooperative spectrum sensing and spectrum opportunity for satellite cluster communication networks. Ad Hoc Netw 58(C):231
Hu JY, Yu B, Jing MY, Xiao LT, Jia ST, Qin GQ, Long GL (2016) Experimental quantum secure direct communication with single photons. Light Science & Applications 5(9):e16144
Acknowledgements
This work was supported by the National Natural Science Foundation of China (Grant No. 61601145, 61471142, 61571167, 61871157), the Fund of Aeronautics Science of China (Grant No. ASFC-2017ZC77004), SAST fund (Grant No. SAST2017050) and HIRP fund (Grant No. HO2017050001C9).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Liu, J., Yang, Z., Wu, Z. et al. Control Code Multiple Encryption Algorithm on Satellite-to-ground Communication. Mobile Netw Appl 24, 1955–1974 (2019). https://doi.org/10.1007/s11036-019-01338-z
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-019-01338-z