Abstract
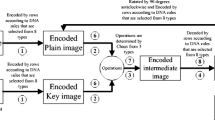
A new block cipher for gray images is proposed in this paper which fully utilizes whole set of DNA complementary rules dynamically for encoding and decoding each pixel of a block. The most significant (MSB) part of each block is added under DNA addition operation with least significant (LSB) while LSB part itself get encrypted by chaotically selecting different DNA rules for each pixel. The initial condition is calculated from 128-bits external input key and then the said key is modified for each subsequent block of an image. An image is permuted by Piecewise Linear Chaotic Map (PWLCM) while logistic sequence is used for the selection of encoding and decoding rules for each pixel of a block. The simulated experimental results and the security analysis in terms of quantitative and qualitative way show that our cipher can not only achieve good encryption effect to resist the exhaustive and statistical attacks but also is a good candidate for encrypting large sized uncompressed gray images.









Similar content being viewed by others
References
Adelman (1994) Molecular computation of solution of combinatorial problems. Science 266:1021–1024
Alvarez G, Li S (2006) Some basic cryptography requirements for chaos based cryptosystems. J Bifurcation Chaos 16:2129–2151
Behnia S, Akhshani A, Mahmodi H, Akhavan A (2008) “A novel algorithm for image encryption based on mixture of chaotic maps”. Chaos, Solitons Fractals 35:408–419
Biham E, Shamir A (1991) “Differential cryptanalysis of DES-like cryptosystems,” In Proceedings of the 10th Annual International Cryptology Conference on Advances in Cryptology: Springer-Verlag
Biham E, Shamir A (1993) Differential cryptanalysis of the Full 16-round DES, In Proceedings of the 12th Annual International Cryptology Conference on Advances in Cryptology: Springer-Verlag
Chang WC, Wong KW, Yu H, Zhu ZL (2012) An image encryption scheme using light weight bit level confusion and cascade cross circular diffusion. Opt Commun 285:2343–2354
Chen G, Mao Y, Chui C (2004) “A symmetric image encryption scheme based on 3D chaotic cat maps”. Chaos, Solitons Fractals 21:749–761
Francois M, Grosges T, Barchiesi D, Erra R (2012) A new image encryption scheme based on a chaotic function. Signal Process Image Commun 27:249–259
Fridrich J (1998) Symmetric ciphers based on two-dimensional chaotic maps. J Bifurcation Chaos 8:1259–1262
Hermassi H, Rhouma R, Belghith S (2010) Joint compression and encryption using chaotically mutated Huffman trees. Commun Nonlinear Sci Numer Simulat 15:2987–2999
Hongjun L, Xingyuan W (2010) Color image encryption based on one time keys and robust chaotic maps. Comput Math Appl 59:3320–3327
Hui CG, Kai H, Ding Yi (2012) Image permutation scheme based on modified logistic map, IPCSIT 52
Kaneko K (1989) Pattern dynamics in spatiotemporal chaos: pattern selection, diffusion of defect and pattern competition intermittency, Physica D 34
King OD, Gabroit P (2007) Binary templates for comma free DNA codes. Discret Appl Math 155:831–839
Liu H, Wang X, Kadir A (2012) Image encryption using DNA complementary rule and chaotic maps. Appl Soft Comput 12:1457–1466
Liu L, Zhang Q, Wei X, A RGB image encryption algorithm based on DNA encoding and chaos map Computers and Electrical Engineering 38(2012) 1240-1248
Menezes AJ, Oorschot PC, Vanstone SA (1996) Handbook of applied cryptography. CRC Press, Boca Raton
Socek D, Magliveras S, C’ulibrik D, Marques O, Kalva H, Furhat B, Digital video encryption algorithm based on correlation preserving permutations, EURASIP Journal on Information Security, doi:10.1155/2007/52965
Stallings W (1999) Cryptography and network security: principles and practices. Prentice Hall, Upper Saddle River
Stinson DR (2002) Crtography: theory and prctise, 2nd edn. CRC, Boca Raton
Wang Y, Liao X, Xiang T, Wang KW (2007) Cryptanalysis and improvement on a block cryptosystems based on iterating a chaotic map. Phys Lett A 363:277–281
Wang Y, Wong KW, Liao X, Chen G (2011) A new chaos-based fast image encryption algorithm. Applied soft computing 11:514–522
Wang X, Zhang J (2008), An image scrambling encryption using chaos controlled Poker shuffle operation, in: Proceedings of International Symposium on Biometrics and Security Technologies, 23–24 April 2008, pp 1–6
Watson JD, Crick FHC (1953) A structure for DNA. Nature 171:737–738
Wu Y, Noonan J P, Agaian S (2011) Shannon entropy based randomness measurement and test for image encryption, in CoRR abs/1103.5520
Wu Y, Noonan JP, Agaian S (2011) NPCR and UACI randomness tests for image encryption,” in Cyber Journals: Multidisciplinary Journals in Science and Technology, Journal of Selected Areas in Telecommunications (JSAT), pp 31–38 (April 2011)
Xiao GZ, Lu MX, Qin L, Lai XJ (2006) New field of Cryptography, Chinese Science Bulletin 51
Xingyuan W, Canqi J (2012) Image encryption using game of life permutation and PWLCM chaotic system. Opt Commun 285:412–417
Yuan WX, Feng C, Tian W (2010) A new compound mode of confusion and diffusion for block encryption of image based on chaos. Commun Nonlinear Sci Numer Simulat 15:2479–2485
Zhang Q, Guo L, Wei X (2010) Image encryption using DNA addition combining with chaotic maps. Math Comput Model 52:2028–2035
Zhang Q, Guo L, Xue X, Wei X (2009) An image encryption algorithm based on DNA sequence addition operation Fourth International Conference on Bio-Inspired Computing. BIC-TA ‘09
Acknowledgments
Financial support for the work described here was provided by National Natural Science Foundation of China Grant Nos. (61003247 and 61170249), Computer Science and Engineering Department, ChongQing University, People Republic of China
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
ur Rehman, A., Liao, X., Kulsoom, A. et al. Selective encryption for gray images based on chaos and DNA complementary rules. Multimed Tools Appl 74, 4655–4677 (2015). https://doi.org/10.1007/s11042-013-1828-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-013-1828-7