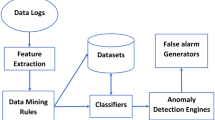
Abstract
The objective of any anomaly detection system is to efficiently detect several types of malicious traffic patterns that cannot be detected by conventional firewall systems. Designing an efficient intrusion detection system has three primary challenges that include addressing high dimensionality problem, choice of learning algorithm, and distance or similarity measure used to find the similarity value between any two traffic patterns or input observations. Feature representation and dimensionality reduction have been studied and addressed widely in the literature and have also been applied for the design of intrusion detection systems (IDS). The choice of classifiers is also studied and applied widely in the design of IDS. However, at the heart of IDS lies the choice of distance measure that is required for an IDS to judge an incoming observation as normal or abnormal. This challenge has been understudied and relatively less addressed in the research literature both from academia and from industry. This research aims at introducing a novel distance measure that can be used to perform feature clustering and feature representation for efficient intrusion detection. Recent studies such as CANN proposed feature reduction techniques for improving detection and accuracy rates of IDS that used Euclidean distance. However, accuracies of attack classes such as U2R and R2L are not significantly promising. Our approach GARUDA is based on clustering feature patterns incrementally and then representing features in different transformation space through using a novel fuzzy Gaussian dissimilarity measure. Experiments are conducted on both KDD and NSL-KDD datasets. The accuracy and detection rates of proposed approach are compared for classifiers such as kNN, J48, naïve Bayes, along with CANN and CLAPP approaches. Experiment results proved that proposed approach resulted in the improved accuracy and detection rates for U2R and R2L attack classes when compared to other approaches.
























Similar content being viewed by others
References
Weller-Fahy DJ, Borghetti BJ, Sodemann AA (2015) A survey of distance and similarity measures used within network intrusion anomaly detection. IEEE Commun Surv Tutor 17(1):70–91
Lin YS, Jiang JY, Lee SJ (2014) A similarity measure for text classification and clustering. IEEE Trans Knowl Data Eng 26(7):1575–1590
Jiang JY, Cheng WH, Chiou YS, Lee SJ (2011) A similarity measure for text processing. In: 2011 International Conference on Machine Learning and Cybernetics, Guilin, pp 1460–1465
Yoo JS, Shekhar S (2009) Similarity-profiled temporal association mining. IEEE Trans Knowl Data Eng 21(8):1147–1161
Radhakrishna V, Kumar PV, Janaki V (2016) A novel similar temporal system call pattern mining for efficient intrusion detection. J Univers Comput Sci 22(4):475–493. https://doi.org/10.3217/jucs-022-04-0475
Radhakrishna V, Aljawarneh SA, Veereswara Kumar P et al (2017) ASTRA—a novel interest measure for unearthing latent temporal associations and trends through extending basic Gaussian membership function. Multimed Tools Appl. https://doi.org/10.1007/s11042-017-5280-y
Radhakrishna V, Veereswara Kumar P, Janaki V (2017) SRIHASS—a similarity measure for discovery of hidden time profiled temporal associations. Multimed Tools Appl. https://doi.org/10.1007/s11042-017-5185-9
Radhakrishna V, Aljawarneh SA, Kumar PV, Janaki V (2017) A novel fuzzy similarity measure and prevalence estimation approach for similarity profiled temporal association pattern mining. Future Gener Comput Syst. https://doi.org/10.1016/j.future.2017.03.016(ISSN 0167-739X)
Radhakrishna V, Aljawarneh SA, Kumar PV et al (2016) A novel fuzzy Gaussian-based dissimilarity measure for discovering similarity temporal association patterns. Soft Comput. https://doi.org/10.1007/s00500-016-2445-y
Deza M, Deza E (2009) Encyclopedia of distances. Springer, Berlin
Zarpelao BB, Miani RS, Kawakani CT, de Alvarenga SC (2017) A survey of intrusion detection in Internet of Things. J Netw Comput Appl 84:25–37
Aljawarneh SA, Vangipuram R, Puligadda VK, Vinjamuri J (2017) G-SPAMINE: an approach to discover temporal association patterns and trends in internet of things. Future Gener Comput Syst 74:430–443
Sindhu SSS, Geetha S, Kannan A (2012) Decision tree based light weight intrusion detection using a wrapper approach. Exp Syst Appl 39(1):129–141
Lima CFL, de Assis FM, de Souza CP (2012) A comparative study of use of shannon, rényi and tsallis entropy for attribute selecting in network intrusion detection. In: Yin H, Costa JAF, Barreto G (eds) Intelligent Data Engineering and Automated Learning-IDEAL 2012. Lecture Notes in Computer Science, vol 7435. Springer, Berlin, Heidelberg
Singh S, Silakari S (2009) An ensemble approach for feature selection of cyber attack dataset. Int J Comput Sci Inf Secur 6(2):297–302
Chen RC, Cheng KF, Chen YH, Hsieh CF (2009) Using rough set and support vector machine for network intrusion detection system. In: 2009 First Asian Conference on Intelligent Information and Database Systems, Dong Hoi, pp 465–470
Devarakonda N, Pamidi S, Valli Kumari V, Govardhan A (2011) Outliers detection as network intrusion detection system using multi layered framework. In Advances in computer science and information technology, vol 131. Springer, Berlin, pp 101–111
Mabu S, Chen C, Lu N, Shimada K, Hirasawa K (2011) An intrusion-detection model based on fuzzy class-association-rule mining using genetic network programming. IEEE Trans Syst Man Cybern Part C (Appl Rev) 41(1):130–139
Shyu M-L, Sainani V (2009) A multiagent-based intrusion detection system with the support of multi-class supervised classification. In: Data mining and multiagent integration. Springer, Berlin, pp 127–142
Su M-Y, Yu G-J, Lin C-Y (2009) A real-time network intrusion detection system for large-scale attacks based on an incremental mining approach. Comput Secur 28(5):301–309. https://doi.org/10.1016/j.cose.2008.12.001
He X, Parameswaran S (2008) MCAD: multiple connection based anomaly detection. In: 11th IEEE Singapore International Conference on Communication Systems, Guangzhou, 2008, pp 999–1004
Gunupudi RK, Nimmala M, Gugulothu N, Gali SR (2017) CLAPP: a self-constructing feature clustering approach for anomaly detection. Future Gener Comput Syst 74:417–429
Kumar GR, Mangathayaru N, Narasimha G (2015) An improved k-means clustering algorithm for intrusion detection using Gaussian function. In: Proceedings of the International Conference on Engineering and MIS 2015 (ICEMIS’15). ACM, New York, Article 69. http://dx.doi.org/10.1145/2832987.2833082
Zhang C, Jiang J, Kamel M (2005) Intrusion detection using hierarchical neural networks. Pattern Recognit Lett 26(6):779–791
Peddabachigari S, Abraham A, Grosan C, Thomas J (2007) Modeling intrusion detection system using hybrid intelligent systems. J Netw Comput Appl 30(1):114–132
Özyer T, Alhajj R, Barker K (2007) Intrusion detection by integrating boosting genetic fuzzy classifier and data mining criteria for rule pre-screening. J Netw Comput Appl 30(1):99–113
Li Y, Guo L (2007) An active learning based TCM-KNN algorithm for supervised network intrusion detection. Comput Secur 26(7):459–467
Hansen JV, Lowry PB, Meservy RD, McDonald DM (2007) Genetic programming for prevention of cyberterrorism through dynamic and evolving intrusion detection. Decis Support Syst 43(4):1362–1374
Giacinto G, Perdisci R, Del Rio M, Roli F (2008) Intrusion detection in computer networks by a modular ensemble of one-class classifiers. Inf Fusion 9(1):69–82
Hu W, Hu W, Maybank S (2008) AdaBoost-based algorithm for network intrusion detection. IEEE Trans Syst Man Cybern Part B (Cybern) 38(2):577–583
Tajbakhsh A, Rahmati M, Mirzaei A (2009) Intrusion detection using fuzzy association rules. Appl Soft Comput 9(2):462–469
Wang G, Hao J, Ma J, Huang L (2010) A new approach to intrusion detection using artificial neural networks and fuzzy clustering. Expert Syst Appl 37(9):6225–6232
Lin S-W, Ying K-C, Lee C-Y, Lee Z-J (2012) An intelligent algorithm with feature selection and decision rules applied to anomaly intrusion detection. Appl Soft Comput 12(10):3285–3290
Baig ZA, Sait SM, Shaeen A (2013) GMDH-based networks for intelligent intrusion detection. Eng Appl Artif Intell 26(7):1731–1740
Lin W-C, Ke S-W, Tsai C-F (2015) CANN: an intrusion detection system based on combining cluster centers and nearest neighbors. Knowl-Based Syst 78:13–21
Kumar GR, Mangathayaru N, Narasimha G (2017) A feature clustering based dimensionality reduction for intrusion detection (FCBDR). IADIS Int J Comput Sci Inf Syst 12(1):26–44
Kumar GR, Mangathayaru N, Narasimha G (2015) Intrusion detection using text processing techniques: a recent survey. In: Proceedings of the International Conference on Engineering and MIS 2015 (ICEMIS ‘15). ACM, New York, Article 55
Kumar GR, Mangathayaru N, Narasimha G (2015) An approach for intrusion detection using text mining techniques. In: Proceedings of the International Conference on Engineering and MIS 2015 (ICEMIS ‘15). ACM, New York, Article 63
Feng W, Zhang Q, Hu G, Huang JX (2014) Mining network data for intrusion detection through combining SVMs with ant colony networks. Future Gener Comput Syst 37(2014):127–140
Aljawarneh S, Aldwairi M, Yassein MB (2017) Anomaly-based intrusion detection system through feature selection analysis and building hybrid efficient model. J Comput Sci. https://doi.org/10.1016/j.jocs.2017.03.006(ISSN 1877-7503)
Kabir E, Hu J, Wang H, Zhuo G (2018) A novel statistical technique for intrusion detection systems. Future Gener Comput Syst 79(1):303–318. https://doi.org/10.1016/j.future.2017.01.029(ISSN 0167-739X)
Wang H, Gu J, Wang S (2017) An effective intrusion detection framework based on SVM with feature augmentation. Knowl-Based Syst 136:130–139. https://doi.org/10.1016/j.knosys.2017.09.014(ISSN 0950-7051)
Hamed T, Dara R, Kremer SC (2018) Network intrusion detection system based on recursive feature addition and bigram technique. Comput Secur 73:137–155. https://doi.org/10.1016/j.cose.2017.10.011(ISSN 0167-4048)
Manzoor I, Kumar N (2017) A feature reduced intrusion detection system using ANN classifier. Expert Syst Appl 88(C):249–257. https://doi.org/10.1016/j.eswa.2017.07.005
Thaseen IS, Kumar CA (2017) Intrusion detection model using fusion of Chi square feature selection and multi class SVM. J King Saud Univ Comput Inf Sci 29(4):462–472. https://doi.org/10.1016/j.jksuci.2015.12.004(ISSN 1319-1578)
Yang Y, Pedersen JO (1997) A comparative study on feature selection in text categorization. In: Fisher DH (ed) Proceedings of the Fourteenth International Conference on Machine Learning (ICML '97), Morgan Kaufmann Publishers Inc., San Francisco, CA, USA, pp 412–420
Portnoy L, Eskin E, Stolfo SJ (2001) Intrusion detection with unlabeled data using clustering. In: Proceedings of ACM CSS Workshop on Data Mining Applied to Security (DMSA-2001), Philadelphia, PA, USA
Eskin E, Arnold A, Prerau M, Portnoy L, Stolfo SJ (2002) A geometric framework for unsupervised anomaly detection: detecting intrusions in unlabeled data. In: Data mining for security applications. Kluwer, Boston
Tavallaee M, Bagheri E, Lu W, Ghorbani AA (2009) A detailed analysis of the KDD CUP 99 data set. In: Proceedings of the 2009 IEEE Symposium on Computational Intelligence in Security and Defense Applications (CISDA 2009), pp 1–6
McHugh J (2000) Testing intrusion detection systems: a critique of the 1998 and 1999 DARPA intrusion detection system evaluations as performed by Lincoln Laboratory. ACM Trans Inf Syst Secur 3(4):262–294
Hall M, Frank E, Holmes G, Pfahringer B, Reutemann P, Witten IH (2009) The WEKA data mining software: an update. SIGKDD Explor Newslett 11(1):10–18. https://doi.org/10.1145/1656274.1656278
Xue-qin Z, Chun-hua G, Jia-jun L (2006) Intrusion detection system based on feature selection and support vector machine. In: 2006 First International Conference on Communications and Networking in China, Beijing, pp 1–5
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Aljawarneh, S.A., Vangipuram, R. GARUDA: Gaussian dissimilarity measure for feature representation and anomaly detection in Internet of things. J Supercomput 76, 4376–4413 (2020). https://doi.org/10.1007/s11227-018-2397-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-018-2397-3