Abstract
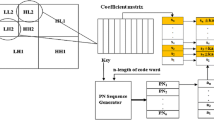
This paper presents a secure multilevel watermarking scheme in which the encrypted text acts as a watermark. The algorithm is based on secure spread-spectrum technique for digital images in discrete wavelet transform (DWT) domain. Potential application of the proposed watermarking scheme is successfully demonstrated for embedding various medical watermarks in text format at different subband decomposition levels depending upon their performance requirements. In the embedding process, the cover CT Scan image is decomposed up to third level of DWT coefficients. Different text watermarks such as personal and medical record of the patient, diagnostic/image codes and doctor code/signature are embedded into the selective coefficients of the second and third level DWT for potential telemedicine applications. Selection of DWT coefficients for embedding is done by column wise thresholding of coefficients values. Also, encryption is applied to the ASCII representation of the text and the encoded text watermark is embedded. The algorithm correctly extracts the embedded watermarks without error and is robust against numerous known attacks without much degradation of the medical image quality of the watermarked image.



Similar content being viewed by others
References
Mostafa, S. A. K., El- sheimy, N., Tolba, A. S., Abdelkader, F. M., & Elhindy, H. M. (2010). Wavelet packets-based blind watermarking for medical image management. The Open Biomedical Engineering Journal, 4, 93–98.
Chao, H. M., Hsu, C. M., & Miaou, S. G. (2002). A data-hiding technique with authentication, integration, and confidentiality for electronic patient records. IEEE Transactions on Information Technology in Biomedicine, 6(1), 46–53.
Acharya, U. R., Anand, D., Bhat, P. S., & Niranjan, U. C. (2001). Compact storage of medical images with patient information. IEEE Transactions on Information Technology in Biomedicine, 5(4), 320–323.
Coatrieux, G., Lecornu, L., Roux, Ch., & Sankur, B. (2006). A review of image watermarking applications in healthcare. IEEE Engineering in Medicine and Biology Society, 1, 4691–4694.
Giakoumaki, A., Pavlopoulos, S., & Koutsouris, D. (2004). A medical image watermarking scheme based on wavelet transform. In Proceedings 25th Annual International Conference of IEEE-EMBS, San Francisco (pp. 1541–1544).
Giakoumaki, A., Pavlopoulos, S., & Koutsouris, D. (2006). Secure and efficient health data management through multiple watermarking on medical images. Medical & Biological Engineering & Computing, 44, 619–631.
Giakoumaki, A., Pavlopoulos, S., & Koutsouris, D. (2006). Multiple image watermarking applied to health information management. IEEE Transactions on Information Technology in Biomedicine, 10(4), 722–732.
Kumar, B., Singh, H. V., Singh, S. P., & Mohan, A. (2011). Secure spread-spectrum watermarking for telemedicine applications. Journal of Information Security, 2, 91–98.
Mohanty, S. P. (1999). Watermarking of digital images. In M.S. Thesis, Indian Institute of Science, India.
Wolak, M. C. (2000). Digital watermarking. United States: Preliminary Proposal, Nova Southeastern University.
Nikolaidis, N., & Pitas, I. (1999). Digital image watermarking: An overview. In IEEE International Conference on Multimedia Computing and Systems (Vol. 1, pp. 1–6).
Cox, I. J., & Miller, M. L. (2002). The first 50 years of electronic watermarking (EURASIP). Journal on Applied Signal Processing, 2, 126–132.
Meerwald, P., & Uhl, A. (2001). A survey of wavelet-domain watermarking algorithms. In Proceedings of the SPIE Security and Watermarking of Multimedia Contents, San Jose (pp. 516–505).
Hajjara, S., Abdallah, M., & Hudaib, A. (2009). Digital image watermarking using localized biorthogonal wavelets. European Journal of Scientific Research, 26(4), 594–608.
Paquet, A. H., & Ward, R. K. (2002). Wavelet-based digital watermarking for image authentication. In Proceedings of the IEEE Canadian Conference on Electrical and Computer Engineering, Winnipeg 2002 (Vol. 2, pp. 884–879).
Feng, J. B., Lin, I. C., Tsai, C. S., & Chu, Y. P. (2006). Reversible watermarking: Current and key issues. International Journal of Network Security, 2(3), 161–170.
Lee, S., Chang, C. D., & Kalker, T. (2007). Reversible image watermarking based on integer-to-integer wavelet transform. IEEE Transaction on Information Forensics and Security, 2(3), 321–330.
Youngberry, K. (2004). Telemedicine research. Journal of Telemedicine and Telecare, 10(2), 121–123.
Terry, M. (2009). Medical identity theft and telemedicine security. Telemedicine and e-Health, 15(10), 928–932.
Bowman, D. (2012). http://www.fiercehealthit.com/story/researchers-use-digital-watermarks-protect-medical-images.
Ollove, M. (2014). www.usatoday.com/story/…/stateline-identity-thefts-medical…/5279351.
Kumar, B., Anand, A., Singh, S. P., & Mohan, A. (2011). High capacity spread-spectrum watermarking for telemedicine applications. World Academy of Science, Engineering and Technology, 5, 62–66.
Umaamaheshvari, A., & Thanushkodi, K. (2012). High performance and effective watermarking scheme for medical images. European Journal of Scientific Research, 67, 283–293.
Soliman, M. M., Hassanien, A. E., Ghali, N. I., & Onsi, H. M. (2012). An adaptive watermarking approach for medical imaging using swarm intelligence. International Journal of Smart Home, 6, 37–50.
Kannamma, A., Pavithra, K., & Subha Rani, S. (2012). Double watermarking of DICOM medical images using wavelet decomposition technique. European Journal of Scientific Research, 70, 46–55.
Pal, K., Ghosh, G., & Bhattacharya, M. (2012). Biomedical image watermarking in wavelet domain for data integrity using bit majority algorithm and multiple copies of hidden information. American Journal of Biomedical Engineering, 2, 29–37.
Zhang, L., & Zhou, P.-P. (2010). Localized affine transform resistant watermarking in region-of-interest. Telecommunication Systems, 44, 205–220.
Zain, J., & Clarke, M. (2005). Security in telemedicine: Issue in watermarking medical images. In International Conference: Science of Electronic, Technologies of Information and Telecommunications.
Memon, N. A., & Gilani, S. A. M. (2008). NROI watermarking of medical images for content authentication. In Proceedings of 12th IEEE International Multitopic Conference, Karachi, Pakistan (pp. 106–110).
Singh, A. K., Dave, M., & Mohan, A. (2014). Wavelet based image watermarking: Futuristic concepts in information security. Proceedings of the National Academy of Sciences, India Section A: Physical Sciences, 84(3), 345–359. doi:10.1007/s40010-014-0140-x.
Cox, I. J., Kilian, J., Thomson, L. F., & Talal, Shamoon. (1997). Secure spread spectrum watermarking for multimedia. IEEE Transactions on Image Processing, 6(12), 1673–1687.
Malvar, H. S., & Florencio, D. A. F. (2003). Improved spread spectrum: A new modilation technique for robust watermarking. IEEE Transactions on Signal Processing, 51(4), 898–905.
Perez-Freire, L., & Perez-Gonzalez, F. (2009). Spread-spectrum watermarking security. IEEE Transactions on Information Forensics and Security, 4(1), 2–24.
Xuan, G., Yang, C., Zheng, Y., Shi, Y. Q., & Ni, Z. (2004). Reversible data hiding based on wavelet spread spectrum. In IEEE International workshop on multimedia signal processing (MMSP2004), Siena, Italy (pp. 211–214).
Domingo-Ferrer, J., & Sebé, F. (2002). Invertible spread-spectrum watermarking for image authentication and multilevel access to precision-critical watermarked images. In Proceedings of the International Conference on Information Technology: Coding and Computing (pp. 1–6).
Das, T. S., Mankar, V. H., & Sarkar, S. K. (2007). Spread spectrum based robust image watermark authentication. In International Conference, Madurai, India (pp. 673–676).
Kumar, B., Kumar, S. B., & Chauhan, D. S. (2014). Wavelet based imperceptible medical image watermarking using spread-spectrum. In 37th International Conference on telecommunications and signal processing, Berlin Germany (pp. 660–664).
Singh, A. K., Kumar, B., Dave, M., & Mohan, A. (2015). Robust and imperceptible spread-spectrum watermarking for telemedicine applications. Proceedings of the National Academy of Sciences, India, Section A: Physical Sciences,. doi:10.1007/s40010-014-0197-6.
Singh, A. K., Dave, M., & Mohan, A. (2013). A hybrid algorithm for image watermarking against signal processing attack. In S. Ramanna et al. (Eds.), Proceedings of 7th Multi-Disciplinary International Workshop in Artificial Intelligence, Krabi-Thailand, Lecture Notes in Computer Science (LNCS) (Vol. 8271, pp. 235–246).
Singh, A. K., Dave, M., & Mohan, A. (2013). Hybrid technique for robust and imperceptible image watermarking in DWT-DCT-SVD domain. National Academy Science Letters,. doi:10.1007/s40009-014-0241-8.
Wójtowicz, W. (2013). Biometric watermarking for medical images-example of iris code (pp. 409–416). Technical Transactions. doi:10.4467/2353737XCT.14.051.1977.
Mangaiyarkarasi, P., & Arulselvi, S. (2013). Medical image watermarking based on DWT and ICA for copyright protection. In R. Malathi & J. Krishnan (Eds.), Recent Advancements in System Modelling Applications, Lecture Notes in Electrical Engineering (Vol. 188, pp. 21–33).
Priya, S., Santhi, B., & Swaminathan, P. (2014). Study on medical image watermarking techniques. Journal of applied science, 14(14), 1638–1642.
Hajjaji, M. A., El-Bay, Bourennane, Abdelali, A. B., & Mtibaa, A. (2014). Combining Haar wavelet and Karhunen loeve transforms for medical images watermarking. BioMed Research International, 2014, 1–15.
Kannammal, A., & Subha Rani, S. (2014). Two level security for medical images using watermarking/encryption algorithms. International Journal of Imaging Systems and Technology, 24(1), 111–120.
Ali, Al-Haj, & Amer, A. (2014). Secured telemedicine using region-based watermarking with tamper localization. Journal of Digital Imaging,. doi:10.1007/s10278-014-9709-9.
Wang, S., Zheng, D., & Zhao, J. (2014). Adaptive watermarking and tree structure based image quality estimation. IEEE Transactions on Multimedia, 16(2), 311–325.
Gao, L., Gao, T., Sheng, G., & Zhang, S. (2014). Robust medical image watermarking scheme with rotation correction. In J. -S. Pan et al. (Eds.), Intelligent Data Analysis and Its Applications, Volume 2, Advances in Intelligent Systems and Computing (Vol. 298, pp. 283–292).
Yu, Y. C., & Hou, T. W. (2014). An efficient forward-secure group certificate digital signature scheme to enhance EMR authentication process. Medical & Biological Engineering & Computing, 52, 449–457.
Singh, A. K., Kumar, B., Dave, M., & Mohan, A. (2015). Multiple watermarking on medical images using selective DWT coefficients. Journal of Medical Imaging and Health Informatics, 5, 1–8. doi:10.1166/jmihi.2015.1432.USA.
Khademi April and Krishnan Sridhar. (2007). Shift-invariant discrete wavelet transform analysis for retinal image classification. Medical & Biological Engineering & Computing, 45, 1211–1222.
Zaz, Y., & Fadil, L. E. (2010). Protecting EPR data using cryptography and digital watermarking. In International Conference on Models of Information and Communication Systems, Rabat, November 2010.
Navas, K. A., Nithya, S., Rakhi, R., & Sasikumar, M. (2007). Lossless watermarking in JPEG2000 for EPR data hiding. In Proceedings of IEEE-EIT 2007, Chicago, USA (pp. 697–702).
Shivani Garg and Ranjit Singh. (2012). An efficient method for digital image watermarking based on PN sequences. International Journal on Computer Science and Engineering (IJCSE), 4(09), 1550–1561.
MedPix™ Medical image database http://rad.usuhs.mil/medpix/medpix.html.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Singh, A.K., Dave, M. & Mohan, A. Multilevel Encrypted Text Watermarking on Medical Images Using Spread-Spectrum in DWT Domain. Wireless Pers Commun 83, 2133–2150 (2015). https://doi.org/10.1007/s11277-015-2505-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2505-0