Abstract
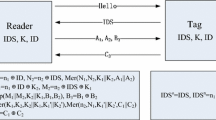
Due to the storage capacity and computational power restrictions of low-cost RFID tags based on the EPC-C1G2 standard, most of the existing authentication protocols seem too complicated to be appropriate for these tags; thus the design of authentication protocols compliant with the EPC-C1G2 standard is a big challenge. Recently, a lightweight mutual authentication protocol for RFID conforming to the EPC-C1G2 standard was proposed by Caballero-Gil et al. aiming to be used in VANETs. This scheme does not rely on RFID readers as they are portable. Instead, it bases security on trust in the server because all shared secrets are stored only by the tag and the server with no possible access by the reader at any time. In this paper, we prove that this scheme is vulnerable to de-synchronization attack and suffers from the information leakage with a complexity of about 216 offline PRNG evaluations which is completely affordable by a conventional adversary. In addition, we present a simple tag impersonation attack against this protocol. To counteract such flaws, we improve the Caballero-Gil et al. scheme to present a new RFID authentication protocol, entitled CG+, so that it provides the claimed security properties.


Similar content being viewed by others
References
Hunt, V. D., Puglia, A., & Puglia, M. (2007). RFID: A guide to radio frequency identification. NY: John Wiley & Sons.
Pang, L., He, L., Pei, Q., & Wang, Y. Secure and efficient mutual authentication protocol for RFID conforming to the EPC C-1 G-2 standard. In Wireless Communications and Networking Conference (WCNC), 2013 IEEE, 2013 (pp. 1870–1875). IEEE.
SA, S. W. (2011). RFID (radio frequency identification): Principles and applications. Retrived from www.eecs.harvard.edu/rfid-article.pdfon,1.
Park, Y., Sur, C., Jung, C. D., & Rhee, K.-H. (2009). Efficient anonymous authentication protocol using key-insulated signature scheme for secure VANET. In Mobile lightweight wireless systems (pp. 35–44). Springer.
Health, U. D. O., & Services, H. (2004). Combating Counterfeit Drugs, A Report of the Food and Drug Administration. Food and Drug Administration. http://www.fda.gov/oc/initiatives/counterfeit/report02_04.pdf.
Choi, E. Y., Lee, D. H., & Lim, J. I. (2009). Anti-cloning protocol suitable to EPCglobal Class-1 Generation-2 RFID systems. Computer Standards & Interfaces, 31(6), 1124–1130.
Duc, D. N., Lee, H., & Kim, K. (2006). Enhancing security of EPCglobal Gen-2 RFID against traceability and cloning. Auto-ID Labs Information and Communication University, White Paper.
Habibi, M. H., Alagheband, M. R., & Aref, M. R. (2011). Attacks on a lightweight mutual authentication protocol under EPC C-1 G-2 standard. In Information security theory and practice. security and privacy of mobile devices in wireless communication (pp. 254–263). Springer.
Burmester, M., De Medeiros, B., Munilla, J., & Peinado, A. (2009). Secure EPC gen2 compliant radio frequency identification. In Ad-Hoc, mobile and wireless networks (pp. 227–240). Springer.
Vajda, I., & Buttyán, L. (2003). Lightweight authentication protocols for low-cost RFID tags. In Second Workshop on security in ubiquitous computing–ubicomp 2003.
Defend, B., Fu, K., & Juels, A. Cryptanalysis of two lightweight RFID authentication schemes. In Pervasive Computing and Communications Workshops, 2007. PerCom Workshops’ 07. Fifth Annual IEEE International Conference on, 2007 (pp. 211–216). IEEE.
Peris-Lopez, P., Hernandez-Castro, J. C., Estevez-Tapiador, J. M., & Ribagorda, A. EMAP: An efficient mutual-authentication protocol for low-cost RFID tags. In On the move to meaningful internet systems 2006: Otm 2006 Workshops, 2006 (pp. 352–361). Springer.
Peris-Lopez, P., Hernandez-Castro, J. C., Estevez-Tapiador, J. M., & Ribagorda, A. (2006). M2AP: A minimalist mutual-authentication protocol for low-cost RFID tags. In Ubiquitous intelligence and computing (pp. 912–923). Springer.
Peris-Lopez, P., Hernandez-Castro, J. C., Estévez-Tapiador, J. M., & Ribagorda, A. (2006). LMAP: A real lightweight mutual authentication protocol for low-cost RFID tags. In Proceedings of 2nd Workshop on RFID security (p. 6).
Li, T., & Deng, R. (2007). Vulnerability analysis of EMAP-an efficient RFID mutual authentication protocol. In Availability, Reliability and Security, 2007. ARES 2007. The Second International Conference on, 2007 (pp. 238–245). IEEE.
Li, T., & Wang, G. (2007). Security analysis of two ultra-lightweight RFID authentication protocols. In New approaches for security, privacy and trust in complex environments (pp. 109–120). Springer.
Chien, H.-Y. (2007). SASI: A new ultralightweight RFID authentication protocol providing strong authentication and strong integrity. Dependable and Secure Computing, IEEE Transactions on, 4(4), 337–340.
Sun, H.-M., Ting, W.-C., & Wang, K.-H. (2011). On the security of Chien’s ultralightweight RFID authentication protocol. IEEE Transactions on Dependable and Secure Computing, 8(2), 315–317.
Chien, H.-Y., & Chen, C.-H. (2007). Mutual authentication protocol for RFID conforming to EPC Class 1 Generation 2 standards. Computer Standards & Interfaces, 29(2), 254–259.
Peris-Lopez, P., Hernandez-Castro, J. C., Tapiador, J. M., & Van der Lubbe, J. C. (2011). Cryptanalysis of an EPC class-1 generation-2 standard compliant authentication protocol. Engineering Applications of Artificial Intelligence, 24(6), 1061–1069.
Konidala, D. M., Kim, Z., & Kim, K. (2007) A simple and cost-effective RFID tag-reader mutual authentication scheme. In Proceedings of Int’l Conference on RFID Security (RFIDSec’07) (pp. 141–152).
Peris-Lopez, P., Li, T., Hernandez-Castro, J. C., & Tapiador, J. M. (2009). Practical attacks on a mutual authentication scheme under the EPC Class-1 Generation-2 standard. Computer Communications, 32(7), 1185–1193.
Huang, Y.-J., Lin, W.-C., & Li, H.-L. (2012). Efficient implementation of RFID mutual authentication protocol. Industrial Electronics, IEEE Transactions on, 59(12), 4784–4791.
Huang, Y.-J., Yuan, C.-C., Chen, M.-K., Lin, W.-C., & Teng, H.-C. (2010). Hardware implementation of RFID mutual authentication protocol. Industrial Electronics, IEEE Transactions on, 57(5), 1573–1582.
Aghili, S. F., Bagheri, N., Gauravaram, P., Safkhani, M., & Sanadhya, S. K. (2013). On the security of two RFID mutual authentication protocols. In Radio frequency identification (pp. 86–99). Springer.
Burmester, M., & De Medeiros, B. The security of EPC Gen2 compliant RFID protocols. In Applied cryptography and network security, 2008 (pp. 490–506). Springer.
Lo, N.-W., & Yeh, K.-H. (2007). An efficient mutual authentication scheme for EPCglobal class-1 generation-2 RFID system. In Emerging directions in embedded and ubiquitous computing (pp. 43–56). Springer.
Yoon, E.-J. (2012). Improvement of the securing RFID systems conforming to EPC class 1 generation 2 standard. Expert Systems with Applications, 39(1), 1589–1594.
Yeh, T.-C., Wang, Y.-J., Kuo, T.-C., & Wang, S.-S. (2010). Securing RFID systems conforming to EPC Class 1 Generation 2 standard. Expert Systems with Applications, 37(12), 7678–7683.
Habibi, M. H., Gardeshi, M., & Alaghband, M. R. (2011). Practical attacks on a RFID authentication protocol conforming to EPC C-1 G-2 standard. arXiv preprint arXiv:1102.0763.
Caballero-Gil, C., Caballero-Gil, P., Peinado-Domínguez, A., & Molina-Gil, J. (2012). Lightweight authentication for RFID used in VANETs. In Computer aided systems theory–EUROCAST 2011 (pp. 493–500). Springer.
Acknowledgments
We like to thank the anonymous reviewer of this paper for their valuable comments.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Moradi, F., Mala, H. & Ladani, B.T. Security Analysis and Strengthening of an RFID Lightweight Authentication Protocol Suitable for VANETs. Wireless Pers Commun 83, 2607–2621 (2015). https://doi.org/10.1007/s11277-015-2558-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2558-0