Abstract
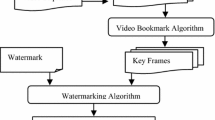
Video copyright is the technique for hiding sensitive data in digital video. This paper aims to introduce a new technique for video copyright namely Fibonacci based keyframe selection and scrambling for video watermarking in DWT–SVD. In this methodology, scene change detection technique is employed for identifying frequent changes in the scenes. In a specific frame, each scene is selected by using keyframes, which are generated by Fibonacci sequence. The initial seeds of the Fibonacci sequence are used as authentication key for generating keyframes. Based on the limitations of the scene changes the authentication keys are generated. The watermark is embedded only in specific frame of the changed scene in LH sub band. The secret image is scrambled using Fibonacci–Lucas transform. In embedding process, singular values (SVs) of the scrambled watermark block are added to the SVs of specific frames, produce the watermarked video collectively. In extraction phase, SVD is performed on the watermarked video to extract the scrambled watermark block from key frames. After that the extracted watermark blocks are collected together to yield the complete scrambled watermark. Later it is descrambled by using the secret keys to generate the original watermark. This method is blind since the host video is not required to extract the watermark. The experimental results show that the proposed methodology resists different image and video processing attacks. In addition, the proposed methodology improves the robustness and quality of both host video and watermark.











Similar content being viewed by others
References
Langelaar, G. C., Setyawan, I., & Lagendijk, R. L. (2000). Watermarking digital image and video data. A state-of-the-art overview. IEEE Signal Processing Magazine, 17(5), 20–46.
Chang, X., Wang, W., Zhao, J., & Zhang, L. (2011). A survey of digital video watermarking. In 2011 Seventh international conference on natural computation (ICNC) (Vol. 1, pp. 61–65). IEEE.
Paul, R. T. (2011). Review of robust video watermarking techniques. IJCA Special Issue on Computational Science, 3, 90–95.
Hernandez-Guzman, V., Cruz-Ramos, C., Nakano-Miyatake, M., & Perez-Meana, H. (2006). Watermarking algorithm based on the DWT. IEEE Latin America Transactions, 4(4), 257–267.
Ejima, M., & Miyazaki, A. (2000). A wavelet-based watermarking for digital images and video. IEICE Transactions on Fundamentals of Electronics, Communications and Computer Sciences, 83(3), 532–540.
Xu, D. W. (2007). A blind video watermarking algorithm based on 3D wavelet transform. In 2007 International conference on computational intelligence and security (pp. 945–949). IEEE.
Al-Taweel, S. A., & Sumari, P. (2009). Robust video watermarking based on 3D-DWT domain. In TENCON 2009–2009 IEEE region 10 conference (pp. 1–6). IEEE.
Reyes, R., Cruz, C., Nakano-Miyatake, M., & Perez-Meana, H. (2010). Digital video watermarking in DWT domain using chaotic mixtures. IEEE Latin America Transactions, 8(3), 304–310.
Chetan, K. R., & Raghavendra, K. (2010). DWT based blind digital video watermarking scheme for video authentication. International Journal of Computer Applications, 4(10), 19–26.
Preda, R. O., & Vizireanu, D. N. (2010). A robust digital watermarking scheme for video copyright protection in the wavelet domain. Measurement, 43(10), 1720–1726.
Cruz-Ramos, C., Reyes-Reyes, R., Nakano-Miyatake, M., & Pérez-Meana, H. (2010). A blind video watermarking scheme robust to frame attacks combined with MPEG2 compression. Journal of Applied Research and Technology, 8(3), 323–337.
Preda, R. O., & Vizireanu, D. N. (2011). Robust wavelet-based video watermarking scheme for copyright protection using the human visual system. Journal of Electronic Imaging, 20(1), 013022.
Faragallah, O. S. (2013). Efficient video watermarking based on singular value decomposition in the discrete wavelet transform domain. AEU-International Journal of Electronics and Communications, 67(3), 189–196.
Naved, A., Rajesh, Y. (2013). Dual band watermarking using 2-D DWT and 2-level SVD for robust watermarking. In Video. International Journal of Science and Research (IJSR), India Online ISSN: 2319-7064.
Thind, D. K., & Jindal, S. (2015). A semi blind DWT–SVD video watermarking. Procedia Computer Science, 46, 1661–1667.
Rajab, L., Al-Khatib, T., & Al-Haj, A. (2015). A blind DWT-SCHUR based digital video watermarking technique. Journal of Software Engineering and Applications, 8(04), 224–233.
Masoumi, M., & Amiri, S. (2013). A blind scene-based watermarking for video copyright protection. AEU-International Journal of Electronics and Communications, 67(6), 528–535.
Zong, T., Xiang, Y., Natgunanathan, I., Guo, S., Zhou, W., & Beliakov, G. (2015). Robust histogram shape-based method for image watermarking. IEEE Transactions on Circuits and Systems for Video Technology, 25(5), 717–729.
Singh, T. R., Singh, K. M., & Roy, S. (2013). Video watermarking scheme based on visual cryptography and scene change detection. AEU-International Journal of Electronics and Communications, 67(8), 645–665.
Mishra, M., Mishra, P., Adhikary, M. C., & Kumar, S. (2012). Image encryption using Fibonacci–Lucas transformation. International Journal of Cryptography and Network Security, 2, 131–141.
Mallat, S. (1999). A wavelet tour of signal processing. Cambridge: Academic press.
Zou, J., Ward, R. K., & Qi, D. (2004). The generalized Fibonacci transformations and application to image scrambling. In IEEE international conference on acoustics, speech, and signal processing, 2004. Proceedings. (ICASSP’04) (Vol. 3, pp. iii-385). IEEE.
Diffie, W., Van Oorschot, P. C., & Wiener, M. J. (1992). Authentication and authenticated key exchanges. Designs, Codes and Cryptography, 2(2), 107–125.
Burmester, M., & Desmedt, Y. (2005). A secure and scalable group key exchange system. Information Processing Letters, 94(3), 137–143.
Lu, R., & Cao, Z. (2007). Simple three-party key exchange protocol. Computers & Security, 26(1), 94–97.
Bull, D. R. (2014). Communicating pictures: A course in image and video coding. Cambridge: Academic Press.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ponni alias Sathya, S., Ramakrishnan, S. Fibonacci Based Key Frame Selection and Scrambling for Video Watermarking in DWT–SVD Domain. Wireless Pers Commun 102, 2011–2031 (2018). https://doi.org/10.1007/s11277-018-5252-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-018-5252-1