Abstract
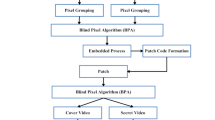
Video steganography is the method of hiding the presence of data within the cover video. In this paper, a novel video steganography technique is revealed, where with the help of Sudoku puzzle of order 9 × 9, extracted image frames of a cover video are utilized to hide encrypted data. The novelties of the work imply that as the input information is first encrypted into cipher text using a new modified substitution and permutation network (SPN)-type block cipher, then, that cipher text is embedded in the video using Sudoku puzzle as a key. This new and robust encryption model is like a block cipher in comparison with Advanced Encryption Standard (AES) that provides enhanced resistance in case of fault attack. This new SPN-type architecture differs with AES architecture in the step of round key mixing function. Its computation complexity is much higher compared to original AES to find 128 bits of tenth round key. Therefore, our proposed work combines both cryptographic and steganographic technique and Sudoku puzzle to enhance the security in maximum level with optimal computational complexity and good embedding capacity rate.








Similar content being viewed by others
References
Ali S, Guo X, Karri R, Mukhopadhyay D (2016) Fault attacks on AES and their countermeasures. In: Secure system design and trustable computing, book part: part I, pp 163–208
Bhaumik J, Roy Chowdhury D (2009) NMIX: an ideal candidate for key mixing. In: Proceedings of the international conference on security and cryptography, pp 285–288
Chang C-C, Lin P-Y, Wang ZH, Li MC (2010) A Sudoku based secret image sharing scheme with reversibility. J Commun 5(1):5–12
Choudry KN, Wanjari A (2015) A survey paper on video steganography. Int J Comput Sci Inf Technol 6(3):2335–2338
Cox IJ, Kilian J, Leighton T, Shamoon T (1997) Secure spread spectrum watermarking for multimedia. In: Proceedings of IEEE image processing, pp 135–149
Daemen J, Rijmen V (2002) The design of Rijndael. Springer, Heidelberg
Das S, Bhaumik J (2014) A Fault based Attack on MDS-AES. International Journal of Network Security 16(3):193–198
Dey D, Bandyopadhyay A, Jana S, Maji AK, Pal RK (2017) A novel image steganographic scheme using 8 × 8 Sudoku puzzle. In: Advanced computing and systems for security. Springer, Singapore, pp 85–100
Erlich Y, Chang K, Gordon A, Ronen R, Navon O, Rooks M, Hannon GJ (2009) DNA Sudoku: harnessing high-throughput sequencing for multiplexed specimen analysis. Genome Res J 19(7):1243–1253
Ginni ES, Pushpinder E (2016) A review on secure video steganography technique using LSB and MSB. Int J Adv Res Comput Commun Eng 5(3):635–639
Giraud C, Thiebeauld H (2004) A survey on fault attacks. In: 6th international conference on smart card research and advanced applications (CARDIS) VI, IFIP 18th world computer congress, TC8/WG8.8 & TC11/WG11.2, Toulouse, France, pp 159–176
Gupta S, Saxena J, Singh S (2015) Design of random scan algorithm in video steganography for security purposes. IOSR J Electron Commun Eng 10(5):14–20
Hao B, Zhao L-Y, Zhong W-D (2011) A novel steganography algorithm based on the motion vector and matrix encoding. In: Proceedings of the communication software and networks (ICCSN), pp 406–409
Hong W, Chen T-S, Shiu C-W (2008) Steganography using Sudoku revisited. In: Proceedings of the 2nd international symposium on intelligent information technology application, pp 935–939
Hu SD, Tu K (2011) A novel video steganography based on non-uniform rectangular partition. In: Proceedings of the IEEE International conference on computational science and engineering, pp 57–61
Jana S, Maji AK, Pal RK (2015) A novel Sudoku solving technique using column based permutation. In: Proceedings of the international symposium on advanced computing and communication (ISAAC), pp 71–77
Liu Y, Li Z, Ma X, Liu J (2013) Robust data hiding algorithm for H. 264/AVC video streams. J Syst Softw 7(2):565–572
Maity G, Jana S, Mantri M, Bhaumik J (2018) Improving security of SPN-type block cipher against fault attack. In: Communication, devices, and computing, lecture notes in electrical engineering, vol 470. Springer, Singapore, pp 115–126
Mehmood I, Sajjad M, Rho S, Baik SW (2016) Divide-and-conquer based summarization framework for extracting affective video content. Neurocomputing 174:393–403
Mukhopadhyay D (2009) An improved fault based attack of the advanced encryption standard. In: AFRICACRYPT, LNCS, 5580, pp 421–434
Sherly AP, Amritha PP (2010) A compressed video steganography using TPVD. Int J Database Manag Syst 2(3):314–321
Swathi A, Jilani SAK (2012) Video steganography by LSB substitution using different polynomial equations. Int J Comput Eng Res 2(5):314–325
Swetha V, Prajith V, Kshema V (2015) Data hiding using video steganography—a survey. Int J Sci Eng Comput Technol 5(6):206–213
Vasudev P, Saurabh K (2013) Video steganography using 32 × 32 vector quantization of DCT. Int J Softw Hardw Res Eng 1(3):72–81
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations
Rights and permissions
About this article
Cite this article
Jana, S., Maji, A.K. & Pal, R.K. A novel SPN-based video steganographic scheme using Sudoku puzzle for secured data hiding. Innovations Syst Softw Eng 15, 65–73 (2019). https://doi.org/10.1007/s11334-019-00324-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11334-019-00324-8