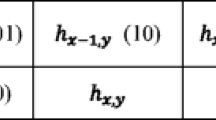Abstract
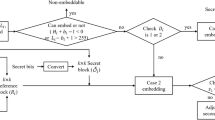
Reversible data hiding has been a hot research topic because it can recover both the host media and hidden data without distortion. Because most digital images are stored and transmitted in compressed forms, such as JPEG, vector quantization, and block truncation coding (BTC), the reversible data hiding schemes in compressed domains have been paid more and more attention. Compared with transform coding, BTC has a significantly low complexity and less memory requirement, it therefore becomes an ideal data hiding domain. Traditional data hiding schemes in the BTC domain modify the BTC encoding stage or BTC-compressed data according to the secret bits, and they have a relatively low efficiency and meanwhile may reduce the image quality. This paper presents a novel reversible data hiding scheme based on the joint neighbor coding technique for BTC-compressed images by further losslessly encoding the BTC-compressed data according to the secret bits. First, BTC is performed on the original image to obtain the BTC-compressed data that can be represented by a high mean table, a low mean table, and a bitplane sequence. Then, the secret data are losslessly embedded in both the high mean and low mean tables. Our hiding scheme is a lossless method based on the relation among the current value and the neighboring ones in mean tables. In addition, it can averagely embed 2 bits in each mean value, which increases the capacity and efficiency. Experimental results show that our scheme outperforms three existing BTC-based data hiding works, in terms of the bit rate, capacity, and efficiency.
Similar content being viewed by others
Abbreviations
- A :
-
The image width
- a :
-
The block width
- B :
-
The image height
- b :
-
The block height
- b i :
-
The initial reference location for encoding I cur, h cur and l cur
- b o :
-
The offset of the reference index used to encode I cur
- \({b_{o}^{(H)}}\) :
-
The offset of the reference high mean for encoding h cur
- \({b_{o}^{(L) }}\) :
-
The offset of the reference low mean for encoding l cur
- BP:
-
The codestream of bitplane
- b r :
-
The final location of the reference index to encode I cur
- \({b_{r}^{(H)}}\) :
-
The final location of the reference high mean for encoding h cur
- \({b_{r}^{(L)}}\) :
-
The final location of the reference low mean for encoding l cur
- CS H :
-
The codestream of the embedded high mean table
- CS L :
-
The codestream of the embedded low mean table
- D :
-
The difference between I cur and I ref
- D H :
-
The difference between h cur and h ref
- D L :
-
The difference between l cur and l ref
- \({(D^{(m)})_{2}}\) :
-
The m bits binary code of D
- H :
-
The high mean table
- h ij , 1 ≤ i ≤ A/a, 1 ≤ j ≤ B/b :
-
The high mean of block x (ij)
- h cur :
-
The current high mean to be encoded
- h ref :
-
The reference high mean used to encode h cur
- I cur :
-
The current index to be encoded
- I ref :
-
The reference index used to encode I cur
- l ij , 1 ≤ i ≤ A/a, 1 ≤ j ≤ B/b :
-
The low mean of block x (ij)
- L :
-
The low mean table
- L :
-
The codestream length
- l cur :
-
The current low mean to be encoded
- l ref :
-
The reference low mean used to encode l cur
- m :
-
The truncation integer used to distinguish the range of D, D H , and D L
- N :
-
The VQ codebook size
- n :
-
The number of neighboring indices considered
- P :
-
The bitplane sequence
- p ij , 1 ≤ i ≤ A/a, 1 ≤ j ≤ B/b :
-
The bitplane of block x (ij)
- t ij , 1 ≤ i ≤ A/a, 1 ≤ j ≤ B/b :
-
The mean value of block x (ij)
- X :
-
The original image
- \({\left\lceil x \right\rceil}\) :
-
The least integer not less than x
- x (ij), 1 ≤ i ≤ A/a, 1 ≤ j ≤ B/b :
-
The image block in the i-th row and j-th column
- \({x_{uv}^{(ij)},\; 1\leq u \leq a, 1 \leq v \leq b}\) :
-
The pixel at the location (u, v) of block x (ij)
References
Barton, J.M.: Method and apparatus for embedding authentication information within digital data. United States Patent, 5,646,997,8 (1997)
Jun, T.: Reversible data embedding using a difference expansion. In: Proceedings of IEEE International Conference on Image Processing Circuits and Systems for Video Technology, pp. 890–896 (2003)
Thodi, D.M., Rodriguez, J.J.: Prediction-error based reversible watermarking. In: Proceedings of IEEE International Conference on Image Processing, pp. 1549–1552 (2004)
Celik, M.U., Sharma, G., Tekalp, A.M., Saber, E.: Reversible data hiding. In: Proceedings of IEEE International Conference on Image Processing, pp. 157–160 (2002)
Alattar, A.M.: Reversible watermark using difference expansion of quads. In: Proceedings of IEEE International Conference on Acoustics, Speech, and Signal Processing, pp. 377–380 (2004)
Fridrich, J., Goljan, M., Du, R.: Invertible authentication watermark for JPEG images. In: Proceedings of IEEE International Conference on Information Technology: Coding and Computing, pp. 223–227 (2001)
Xuan, G.R., Yang, C.Y., Zhen, Y.Z., Shi, Y.Q., Ni, Z.C.: Reversible data hiding using integer wavelet transform and companding technique. In: Proceedings of 3rd International Workshop on Digital Watermarking, pp. 115–124 (2005)
Bausys, R., Kriukovas, A.: Reversible watermarking scheme for image authentication in frequency domain. In: Proceedings of 48th International Symposium ELMAR-2006 focused on Multimedia Signal Processing and Communications, pp. 53–56 (2006)
Yang, B., Lu, Z.M., Sun S.H.: Reversible watermarking in the VQ-compressed domain. In: Proceedings of 5th IASTED International Conference on Visualization, Imaging, and Image Processing, pp. 298–303 (2005)
Chang C.C., Tai W.L., Lin C.C.: A reversible data hiding scheme based on side match vector quantization. IEEE Trans. Circuits Syst. Video Technol. 16(10), 1301–1308 (2006)
Lu Z.M., Wang J.X., Liu B.B.: An improved lossless data hiding scheme based on image VQ-index residual value coding. J. Syst. Softw. 82(6), 1016–1024 (2009)
Chang C.C., Kieu T.D., Wu W.C.: A lossless data embedding technique by joint neighboring coding. Pattern Recognit. 42(7), 1597–1603 (2009)
Delp E.J., Mitchell O.R.: Image compression using block truncation coding. IEEE Trans. Commun. 27(9), 1335–1342 (1979)
Lema M.D., Mitchell O.R.: Absolute moment block truncation coding and its application to color images. IEEE Trans. Commun. 32(10), 1148–1157 (1984)
Arce G.R., Gailagher N.C.: BTC image coding using median filter roots. IEEE Trans. Commun. 31(6), 784–793 (1983)
Wu Y., Coll D.C.: BTC-VQ-DCT hybrid coding of digital images. IEEE Trans. Commun. 39(9), 1283–1287 (1991)
Naciopoulos R.P., Morse D.: Adaptive compression coding. IEEE Trans. Commun. 39(8), 1245–1254 (1991)
Shrrif A.M., Moustafa M.F.: Image compression using VQ-BTC. IEEE Trans. Commun. 43(7), 2177–2182 (1995)
Lu Z.M., Liu C.H., Sun S.H.: Digital image watermarking technique based on block truncation coding with vector quantization. Chin. J. Electron. 11(2), 152–157 (2002)
Lin, M.H., Chang, C.C.: A novel information hiding scheme based on BTC. In: Proceedings of 4th International Conference on Computer and Information Technology, pp. 66–71 (2004)
Chuang J.C., Chang C.C.: Using a simple and fast image compression algorithm to hide secret information. Int. J. Comput. Appl. 28(4), 329–333 (2006)
Hong, W., Chen, T.S., Shiu, C.W.: Lossless steganography for AMBTC compressed images. In: Proceedings of 1st International Congress on Image and Signal Processing, pp. 13–17 (2008)
Chen J., Hong W., Chen T.S., Shiu C.W.: Steganography for BTC compressed images using no distortion technique. Imaging Sci. J. 58(4), 177–185 (2010)
Wang J.X., Lu Z.M.: A path optional lossless data hiding scheme based on VQ joint neighboring coding. Inf. Sci. 179(19), 3332–3348 (2009)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sun, W., Lu, ZM., Wen, YC. et al. High performance reversible data hiding for block truncation coding compressed images. SIViP 7, 297–306 (2013). https://doi.org/10.1007/s11760-011-0238-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11760-011-0238-4