Abstract
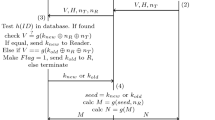
Lightweight and safety are two essential features for large-scale application of radio frequency identification (RFID) tags. Based on the analysis of potential safety problem of RFID and the characteristics of existing typical authentication protocol, a new low-cost RFID tags authentication protocol was proposed. The performance of the new protocol was analyzed. The results show that the protocol can resist replay attacks and concurrent attacks and has nontracking, authenticity, and service availability. In addition, the protocol can also reduce the storage of tags and computation burden to meet the application requirements of low-cost tags.
Similar content being viewed by others
References
Karthikeyan S, Nesterenko M. RFID security without extensive cryptography [C]//itProceedings of the 3rd ACM Workshop on Security of ad hoc and Sensor Networks, SASN 2005. Alexandria: ACM press, 2005: 63–67.
GSI EPC global. EPCTM Radio-frequency Identity Protocols Class-1 Generation-2 UHF RFID Protocol for Communicaition at 860MHz-960MHz Version 1.0.9 [S]. USA: EPC global lnc, 2005.
Zhao Yuehua, Wang Yiwei, Li Xiaocong. New RFID mutual authentication protocol for low-cost tags [J]. Application Research of Computers. 2010, 27(5): 1885–1888.
Duc D C, Park J, Lee H, et al. Enhancing security of EPCglobal Gen-2 RFID tag against traceability and cloning [C] //Symposium on Cryptography and Information Security. Hiroshima: ACM Press, 2006: 269–277.
Chien H, Chen C. Mutual authentication protocol for RFID conforming to EPC class-1 generation-2 standards [J]. Computer Standards & Interfaces, 2007, 29: 254–259.
Han D, Kwon D. Vulnerability of an RFID authentication protocol conforming to EPC Class-1 Generation-2 standards [J]. Computer Standards & Interfaces, 2009, 31: 648–652.
Lopez P P, Castro J C H, Tapiador J M E, et al. Cryptanalysis of a novel authentication protocol conforming to EPC-C1G2 standard [J]. Computer Standards & Interfaces, 2009, 31: 372–380.
Van Le T, Burmester M, De Medeiros B. Universally composable and forward secure RFID authentication and authenticated key exchange [C]//ASIACCS’ 07 Proceedings of the Second ACM Symposium on Information, Computer and Communications Security. New York: ACM Press, 2007: 242–252.
Dang N D, Kwangjo K. Defending RFID authentication protocol against DoS attacks [J]. Computer Communications, 2011, 34: 384–390.
LI Huixian. Design and analysis of the light-weight mutual authentication protocol for RFID [J]. Journal of Xidian University, 2012, 39(1): 172–178.
Cho J S, Yeo S S, Kim S K. Securing against Rrute-force Attack: A hash-based RFID mutual authentication protocol using a secret value [J]. Computer Communications, 2011, 34(3): 391–397.
Author information
Authors and Affiliations
Corresponding author
Additional information
Foundation item: Supported by the Natural Science Foundation of China (60970115,61003268)
Biography: WEI Guoheng, male, Ph.D. candidate, research direction: cryptology and information security.
Rights and permissions
About this article
Cite this article
Wei, G., Zhang, H. A lightweight authentication protocol scheme for RFID security. Wuhan Univ. J. Nat. Sci. 18, 504–510 (2013). https://doi.org/10.1007/s11859-013-0964-2
Received:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11859-013-0964-2