Abstract
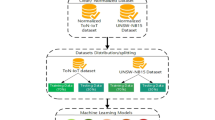
In recent decades, the internet of things (IoT) is a growing technology in smart applications, where it is highly susceptible to security breaches, due to the resource constrained nature of IoT. Among the available security breaches in IoT, Mirai, denial of service, user to root attack, remote to local attack, and probe attack renounce the networks in several ways such as saturating link bandwidth, consumption of server resources, etc. Hence, the installation of antivirus software cannot be guaranteed, because the IoT devices are equipped only with light weighted operating systems. So, intrusion detection systems are developed for the detection of IoT attacks. In this research, a new model is proposed based on random forest and synthetic minority over-sampling technique (RF-SMOTE) to detect the attacks in an IoT network. In this research, the experimental analysis is performed for IoT attack detection, where the evaluation is done on NSL-KDD dataset and network-based detection of IoT (N-BaIoT) dataset, which are the well-known datasets for IoT attack detection. In the experimental phase, the proposed RF-SMOTE model showed minimum of 0.14% and maximum of 14.25% improvement in accuracy on NSL-KDD dataset for binary class. In addition, the proposed model averagely showed minimum of 0.04% and maximum of 7.35% improvement in accuracy on NSL-KDD dataset for four classes. Additionally, the proposed RF-SMOTE model showed minimum of 0.01% and maximum of 0.04% improvement in accuracy on N-BaIoT dataset related to the existing model’s decision tree, shallow model, etc.







Similar content being viewed by others
References
Al-Duwairi B, Al-Kahla W, AlRefai MA, Abdelqader Y, Rawash A, Fahmawi R (2020) SIEM-based detection and mitigation of IoT-botnet DDoS attacks. Int J Electr Comput Eng 10:2088–8708
Alharbi A, Alhaidari S, Zohdy M (2018) Denial-of-service, probing, user to root (U2R) & remote to user (R2L) attack detection using hidden Markov models. Int J Comput Inf Technol
Almiani M, AbuGhazleh A, Al-Rahayfeh A, Atiewi S, Razaque A (2020) Deep recurrent neural network for IoT intrusion detection system. Simul Model Pract Theory 101:102031
Chawla NV, Bowyer KW, Hall LO, Kegelmeyer WP (2002) SMOTE: synthetic minority over-sampling technique. J Artif Intell Res 16:321–357
Cvitic I, Peraković D, Periša M, Botica M (2019) Novel approach for detection of IoT generated DDoS traffic. Wirel Netw 1–14. https://doi.org/10.1007/s11276-019-02043-1
Davahli A, Shamsi M, Abaei G (2020) Hybridizing genetic algorithm and grey wolf optimizer to advance an intelligent and lightweight intrusion detection system for IoT wireless networks. J Ambient Intell Humaniz Comput 11(11):5581–5609.
De Donno M, Dragoni N, Giaretta A, Mazzara M (2016) AntibIoTic: protecting IoT devices against DDoS attacks. In: International conference in software engineering for defence applications, Springer, Cham, pp 59–72
Diro AA, Chilamkurti N (2018) Distributed attack detection scheme using deep learning approach for Internet of Things. Future Gener Comput Syst 82:761–768
Hassan NY, Gomaa WH, Khoriba GA, Haggag MH (2018) Supervised learning approach for twitter credibility detection. In: 2018 13th International conference on computer engineering and systems (ICCES), pp 196–201
Hu JW, Yeh LY, Liao SW, Yang CS (2019) Autonomous and malware-proof blockchain-based firmware update platform with efficient batch verification for Internet of Things devices. Comput Secur 86:238–252
Kumar U, Navaneet S, Kumar N, Pandey SC (2020) Isolation of DDoS attack in IoT: A New Perspective. Wirel Pers Commun 114:2493–2510
Li J, Liu M, Xue Z, Fan X, He X (2020) RTVD: a real-time volumetric detection scheme for DDoS in the Internet of Things. IEEE Access 8:36191–36201
Liu G, Quan W, Cheng N, Zhang H, Yu S (2019) Efficient DDoS attacks mitigation for stateful forwarding in Internet of Things. J Netw Comput Appl 30:1–13
Mallikarjunan KN, Bhuvaneshwaran A, Sundarakantham K, Shalinie SM (2019) DDAM: detecting DDoS attacks using machine learning approach. In: Computational intelligence: theories, applications and future directions-volume I. Springer, Singapore, pp 261–273
Mehmood A, Mukherjee M, Ahmed SH, Song H, Malik KM (2018) NBC-MAIDS: Naïve Bayesian classification technique in multi-agent system-enriched IDS for securing IoT against DDoS attacks. J Supercomput 74:5156–5170
Meidan Y, Bohadana M, Mathov Y, Mirsky Y, Shabtai A, Breitenbacher D, Elovici Y (2018) N-baiot—network-based detection of iot botnet attacks using deep autoencoders. IEEE Pervasive Comput 17:12–22
Osanaiye O, Cai H, Choo KKR, Dehghantanha A, Xu Z, Dlodlo M (2016) Ensemble-based multi-filter feature selection method for DDoS detection in cloud computing. EURASIP J Wirel Commun Netw 2016:130
Panda S, Panda G (2020) Intelligent classification of IoT traffic in healthcare using machine learning techniques. In: International conference on control, automation and robotics (ICCAR), pp 581–585
Park ST, Li G, Hong JC (2020) A study on smart factory-based ambient intelligence context-aware intrusion detection system using machine learning. J Ambient Intell Humaniz Comput 11(4):1405–1412
Quackenbush J (2002) Microarray data normalization and transformation. Nat Genet 32:496–501
Ravi N, Shalinie SM (2020a) Semi-supervised learning based security to detect and mitigate intrusions in IoT network. IEEE Internet Things J 7(11):11041–11052
Ravi N, Shalinie SM (2020b) Learning-driven detection and mitigation of DDoS attack in IoT via SDN-cloud architecture. IEEE Internet Things J 7:3559–3570
Roopak M, Tian GY, Chambers J (2020) Multi-objective-based feature selection for DDoS attack detection in IoT networks. IET Netw 9:120–127
Sathyaraj P, Devi DR (2020) Designing the routing protocol with secured IoT devices and QoS over Manet using trust-based performance evaluation method. J Ambient Intell Humaniz Comput 1–9. https://doi.org/10.1007/s12652-020-02358-4
Tavallaee M, Bagheri E, Lu W, Ghorbani AA (2009) A detailed analysis of the KDD CUP 99 data set. In: 2009 IEEE symposium on computational intelligence for security and defense applications, IEEE, pp 1–6
Tuan TA, Long HV, Kumar R, Priyadarshini I, Son NTK (2019) Performance evaluation of Botnet DDoS attack detection using machine learning. Evol Intell 1–12. https://doi.org/10.1007/s12065-019-00310-w
Van den Broeck J, Cunningham SA, Eeckels R, Herbst K (2005) Data cleaning: detecting, diagnosing, and editing data abnormalities. PLoS Med 2:e267
Wani A, Revathi S (2020) DDoS detection and alleviation in IoT using SDN (SDIoT-DDoS-DA). J Inst Eng India Ser B 101:117–128
Yin D, Zhang L, Yang K (2018) A DDoS attack detection and mitigation with software-defined Internet of Things framework. IEEE Access 6:24694–24705
Zhang X, Xie L, Yao W (2020) Spatio-temporal heterogeneous bandwidth allocation mechanism against DDoS attack. J Netw Comput Appl 162:102658
Funding
We haven’t received any funding from any sources.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
M. Ganesh Karthik declares that he has no conflict of interest. M. B. Mukesh Krishnan declares that he has no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Karthik, M.G., Krishnan, M.B.M. Hybrid random forest and synthetic minority over sampling technique for detecting internet of things attacks. J Ambient Intell Human Comput (2021). https://doi.org/10.1007/s12652-021-03082-3
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12652-021-03082-3