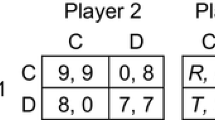
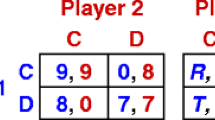
Abstract
Group or collective identity is an individual’s cognitive, moral, and emotional connection with a broader community, category, practice, or institution. There are many different contexts in which collective identity operates, and a host of application domains where collective identity is important. Collective identity is studied across myriad academic disciplines. Consequently, there is interest in understanding the collective identity formation process. In laboratory and other settings, collective identity is fostered through priming a group of human subjects. However, there have been no works in developing agent-based models for simulating collective identity formation processes. Our focus is understanding a game that is designed to produce collective identity within a group. To study this process, we build an online game platform; perform and analyze controlled laboratory experiments involving teams; build, exercise, and evaluate network-based agent-based models; and form and evaluate hypotheses about collective identity. We conduct these steps in multiple abductive iterations of experiments and modeling to improve our understanding of collective identity as this looping process unfolds. Our work serves as an exemplar of using abductive looping in the social sciences. Findings on collective identity include the observation that increased team performance in the game, resulting in increased monetary earnings for all players, did not produce a measured increase in collective identity among them.





















Similar content being viewed by others
Notes
There are other definitions for collective identity (CI). For example, McFarland et al. (2014) state that collective identity means that members become more familiar and equal. Wendt (1994) defines CI as the positive identification with the welfare of another, such that the other is seen as a cognitive extension of the self, rather than independent. See Owens (2006) for a discussion of various definitions of CI.
We use the term model to mean a representation of equations and algorithms to compute some result. In contrast, in the social and some other sciences, model often refers to a qualitative (textual) description of some process that is much more conceptual and not computational. Our models that we present herein are of the first type. We use the term model in the former (quantitative) sense, unless otherwise specified.
References
Abbott A (1995) Sequence analysis: new methods for old ideas. Ann Rev Sociol 21:93–113
Abrams DE, Hogg MA (1990) Social identity theory: constructive and critical advances. Springer, New York
Ackland R, O’Neil M (2011) Online collective identity: the case of the environmental movement. Soc Netw 33:177–190
Agrawal R, Srikant R (1995) Mining sequential patterns. In: Proceedings of the eleventh international conference on data engineering, IEEE Computer Society, ICDE’95, Washington, pp 3–14
Aipperspach R, Cohen E, Canny J (2006) Modeling human behavior from simple sensors in the home. In: Proceedings of the IEEE conference on pervasive computing
Alexander JC, Eyerman R, Giesen B, Smelser NJ, Sztompka P (2004) Cultural trauma and collective identity, 1st edn. University of California Press, Berkeley
Andrews EAM, Bonner AJ (2011) Explaining genetic knock-out effects using cost-based abduction. In: Proceedings of the 22nd international joint conference on artificial intelligence (IJCAI), pp 1635–1640
Atran S, Axelrod R, Davis R (2007) Sacred barriers to conflict resolution. Science 317:1039–1040
Atran S, Sheikh H, Gomez A (2014a) Devoted actors sacrifice for close comrades and sacred cause. Proc Natl Acad Sci 111(50):17702–17703
Atran S, Sheikh H, Gomez A (2014b) For cause and comrade: devoted actors and willingness to fight. Cyclodynamics 5:41–57
Attema T, van Maanen PP, Meeuwissen E (2015) Development and evaluation of multi-agent models predicting twitter trends in multiple domains. In: 2015 IEEE/ACM international conference on advances in social networks analysis and mining (ASONAM), pp 1133–1140
Bach A (1990) Boltzmann’s probability distribution of 1877. Arch Hist Exact Sci 41:1–40
Becker GS (1974) A theory of social interaction. J Political Econ 82:1063–1093
Benjamin DJ, Choi JJ, Fisher G (2016) Religious identity and economic behavior. Rev Econ Stat 98(4):617–637
Bergmann JHM, Langdon PM, Mayagoitia RE, Howard N (2014) Exploring the use of sensors to measure behavioral interactions: An experimental evaluation of using hand trajectories. PLoS One 9(2):1–10
Bornstein G, Yaniv I (1998) Individual and group behavior in the ultimatum game: Are groups more rational players? Exp Econ 1:101–108
Brewer MB (1991) The social self: on being the same and different at the same time. Personal Soc Psychol Bull 17:475–482
Brewer MB, Gardner W (1996) Who is this “we”? Levels of collective identity and self representations. J Personal Soc Psychol 71:83–93
Brewer MB, Silver M (1978) Ingroup bias as a function of task characteristics. Eur J Soc Psychol 8(3):393–400
Brody H (2000) The other side of Eden: hunters, farmers, and the shaping of the world. Farrar, Straus and Giroux, New York
Brunsdon AR (2017) #MisconstruedidentitiesMustFall collective: identity formation in the current South African context: a practical theological perspective. HTS Theol Stud 73:1–7
Butler J (1988) Performative acts and gender constitution: an essay in phenomenology and feminist theory. Theatre J 40(4):519–531
Cadsby CB, Song F, Tapon F (2007) Sorting and incentive effects of pay for performance: an experimental investigation. Acad Manag J 50:387–405
Cadsby CB, Song F, Tapon F (2010) Are you paying your employees to cheat? An experimental investigation. BE J Econ Anal Pol 10:1–30
Cameron D (1997) Performing gender identity: Young men’s talk and the construction of heterosexual masculinity. In: Johnson S, Hanna U (eds) Language and masculinity. Blackwell, Oxford, pp 47–64
Capraro V (2013) A model of human cooperation in social dilemmas. PLoS One 8:e72427–1–e72427–6
Cedeno VI (2019) Pipelines for computational social science experiments and model building. Ph.D. dissertation, Virginia Polytechnic Institute and State University, https://vtechworks.lib.vt.edu/bitstream/handle/10919/91445/Cedeno_VI_D_2019.pdf. Accessed 8 Jan 2019
Chamiak E, Santos E (1992) Dynamic map calculations for abduction. In: Proceedings AAAI conference on artificial intelligence, pp 552–557
Charness G, Rigotti L, Rustichini A (2007) Individual behavior and group membership. Am Econ Rev 97:1340–1352
Charness G, Cobo-Reyes R, Jimenez N (2014) Identities, selection, and contributions in a public-goods game. Games Econ Behav 87:322–338
Chen DL, Yeh S (2014) The construction of morals. J Econ Behav Organ 104:84–105
Chen R, Chen Y (2011) The potential of social identity for equilibrium selection. Am Econ Rev 101(6):2562–89
Chen Y, Li S (2009) Group identity and social preferences. Am Econ Rev 99:431–457
Chen Y, Li SX, Liu TX, Shih M (2014) Which hat to wear? Impact of natural identities on coordination and cooperation. Games Econ Behav 84:58–86
Chen DL, Schonger M, Wickens C (2016) otree-an open-source platform for laboratory, online and field experiments. J Behav Exp Financ 9:88–97
Chierichetti F, Kleinberg J, Kumar R, Mahdian M, Pandey S (2014) Event detection via communication pattern analysis. In: Proceedings of the 8th international conference on weblogs and social media, ICWSM, pp 51–60
Choup AM (2008) The formation and manipulation of collective identity: a framework for analysis. Soc Mov Stud 7(2):191–207
Cohn A, Fehr E, Maréchal MA (2014) Business culture and dishonesty in the banking industry. Nature 516:86–89
Cohn A, Marechal MA, Noll T (2015) Bad boys: how criminal identity salience affects rule violation. Rev Econ Stud 82(4):1289–1308
Cover TM, Thomas J (1991) Elements of information theory. Wiley, Hoboken
Contractor N (2019) How can computational social science motivate the development of theories, data, and methods to advance our understanding of communication and organizational dynamics? In: Foucault Welles B, González-Bailón S (eds) The Oxford Handbook of Networked Communication. Oxford University Press. https://doi.org/10.1093/oxfordhb/9780190460518.013.7
Currarini S, Jackson M, Pin P (2009) An economic model of friendship: homophily, minorities and segregation. Econometrica 77:1003–1045
Davis WL, Davis DE (1972) Internal-external control and attribution of responsibility for success and failure. J Personal 40:123–136
de Oliveira M (1992) Isotropic majority-vote model on a square lattice. J Stat Phys 66:273–281
DeChurch LA, Mesmer-Magnus JR (2010) The cognitive underpinnings of effective teamwork: a meta-analysis. J Appl Psychol 95(1):32–53
Dominowski RL (1969) The effect of pronunciation practice on anagram difficulty. Psychon Sci 16(2):99–100
Drouvelis M, Metcalfe R, Powdthavee N (2010) Priming cooperation in social dilemma games. In: IZA Discussion Papers 4963, Institute for the Study of Labor (IZA)
Durkheim E (1951) Suicide. Free Press, Mumbai
Echenim M, Peltier N, Tourret S (2013) An approach to abductive reasoning in equational logic. In: Proceedings of the 23rd international joint conference on artificial intelligence (IJCAI), pp 531–537
Eckel C, Grossman P (2005) Managing diversity by creating team identity. J Econ Behav Organ 58:371–392
Epstein JM (2007) Generative social science: studies in agent-based computational modeling. Princeton University Press, Princeton
Eriksen TH (2010) Ethnicity and nationalism: anthropological perspectives, 3rd edn. Pluto Press, London
Erikson EH (1980) Identity and the life cycle. W. W. Norton & Company, New York
Feather NT (1969) Attribution of responsibility and valence of success and failure in relation to initial confidence and task performance. J Personal Soc Psychol 13:129–144
Feather NT, Simon JG (1971a) Attribution of responsibility and valence of outcome in relation to initial confidence and success and failure of self and other. J Personal Soc Psychol 18:173–188
Feather NT, Simon JG (1971b) Causal attributions for success and failure in relation to expectation of success based upon selective or manipulative control. J Personal Soc Psychol 39:527–541
Feher O, Wonnacott E, Smith K (2016) Structural priming in artificial languages and the regularisation of unpredictable variation. J Mem Lang 91:158–180
Fiske ST, Gilbert DT, Lindzey G (2010) Handbook of social psychology, 5th edn. Wiley, Hoboken
Flach PA, Kakas AC (2010) Abduction and induction: essays on their relation and integration. Springer, New York
Fominaya CF (2010) Collective identity in social movements: central concepts and debates. Sociol Compass 4:393–404
Gates MA, Suchow JW, Griffiths TL (2017) Empirical tests of large-scale collaborative recall. In: CogSci
Gibbs AL, Su FE (2002) On choosing and bounding probability metrics. Int Stat Rev 70:419–435
Gilhooly KJ, Johnson CE (1978) Effects of solution word attributes on anagram difficulty: a regression analysis. Q J Exp Psychol 30(1):57–70
Gilwhite FJ (2001) Are ethnic groups biological species to the human brain? Essentialism in our cognition of some social categories. Curr Anthropol 42(4):515–553
Ginges J, Atran S (2013) Sacred values and cultural conflict. In: Advances in culture and psychology, pp 273–305
Goldberg CA (2003) Haunted by the specter of communism: collective identity and resource mobilization in the demise of the Workers Alliance of America. Theory Soc 32(5/6):725–773
Goldman M, Stockbauer JW, McAuliffe TG (1977) Intergroup and intragroup competition and cooperation. J Exp Soc Psychol 13:81–88
Gomez A, Brooks ML, Buhrmester MD, Vazquez A, Jetten J, Swann WB (2011a) On the nature of identity fusion: Insights into the construct and a new measure. J Personal Soc Psychol 100:918–933
Gomez A, Morales J, Hart S, Vazquez A, Jetten J, Swann WB (2011b) Rejected and excluded forevermore, but even more devoted: irrevocable ostracism intensifies loyalty to the group among identity-fused persons. Personal Soc Psychol Bull 37:1574–1586
Granovetter M (1978) Threshold models of collective behavior. Am J Sociol 83(6):1420–1443
Greene B (2000) Letters to a young poet. New World Library, Novato
Greenhill B (2008) Recognition and collective identity formation in international politics. Eur J Int Relat 14(2):343–368
Guralnik V, Haigh KZ (2002) Learning models of human behaviour with sequential patterns. In: Proceedings of the AAAI-02 workshop “Automation as Caregiver”, aAAI Technical Report WS-02-02, pp 24–30
Haig BD (2005) An abductive theory of scientific method. Psychol Methods 10:371–388
Hand DJ, Smyth P, Mannila H (2001) Principles of data mining. MIT Press, Cambridge
Hawkes AG (1971) Spectra of some self-exciting and mutually exciting point processes. Biometrika 58(1):83–90
Heller N (2019) The philosopher redefining equality: Elizabeth Anderson thinks we’ve misunderstood the basis of a free and fair society. The New Yorker 07 January. https://www.newyorker.com/magazine/2019/01/07/the-philosopher-redefining-equality. Accessed 2 Feb 2019
Hoff K, Pandey P (2006) Discrimination, social identity, and durable inequalities. Am Econ Rev 96(2):206–211
Hoff K, Pandey P (2014) Making up people-the effect of identity on performance in a modernizing society. J Dev Econ 106(C):118–131
Hogg MA, Abrams D (2007) Intergroup behavior and social identity. In: Hogg MA, Cooper J (eds) The sage handbook of social psychology. Sage, New York, pp 335–360
Homans G (1961) Social behavior: its elementary forms. Harcourt Brace, San Diego
Hu J, Liu M, Zhang J (2014) A semantic model for academic social network analysis. In: 2014 IEEE/ACM international conference on advances in social networks analysis and mining (ASONAM 2014), pp 310–313
Jiménez J, Gomez A, Buhrmester MD et al (2016) The dynamic identity fusion index: a new continuous measure of identity fusion for web-based questionnaires. Soc Sci Comput Rev 34:215–228
Juba B (2016) Learning abductive reasoning using random examples. In: Proceedings of the thirtieth AAAI conference on artificial intelligence
Judd S, Kearns M, Vorobeychik Y (2010) Behavioral dynamics and influence in networked coloring and consensus. PNAS 107:14978–14982
Juergensmeyer M (2003) Terror in the mind of god: the global rise of religious violence, 3rd edn. University of California Press, Berkeley
Kahn A, Ryen AH (1972) Factors influencing the bias towards one’s own group. Int J Group Tens 2:33–50
Kearns M, Judd S, Tan J, Wortman J (2009) Behavioral experiments on biased voting in networks. PNAS 106:1347–1352
Kearns M, Judd S, Vorobeychik Y (2012) Behavioral experiments on a network formation game. In: Economics and computation (EC), pp 690–704
Kendler H, Kendler ST (1962) Vertical and horizontal processes in problem solving. Psychol Rev 69:1–16
Kinnebrew JS, Loretz KM, Biswas G (2013) A contextualized, differential sequence mining method to derive students’ learning behavior patterns. J Educ Data Min 5(1):190–219
Korolov R, Lu D, Wang J, Zhou G, Bonial C, Voss C, Kaplan L, Wallace W, Han J, Ji H (2016) On predicting social unrest using social media. In: Proceedings of the 2016 IEEE/ACM international conference on advances in social networks analysis and mining, ASONAM 2016, Institute of Electrical and Electronics Engineers Inc., pp 89–95
Korolov R, Peabody J, Lavoie A, Das S, Magdon-Ismail M, Wallace W (2015) Actions are louder than words in social media. In: 2015 IEEE/ACM international conference on advances in social networks analysis and mining (ASONAM), pp 292–297
Kozegi B (2006) Ego utility, overconfidence, and task choice. J Eur Econ Assoc 4:673–707
Kozlowski SW, Ilgen DR (2006) Enhancing the effectiveness of work groups and teams. Psychol Sci Publ Interest 7(3):77–124
Kullback S (1959) Information theory and statistics. Wiley, New York
Kullback S, Leibler RA (1951) On information and sufficiency. Ann Math Stat 22(1):79–86
Kurashima T, Althoff T, Leskovec J (2018) Modeling interdependent and periodic real-world action sequences. In: World Wide Web Conference WWW, ACM, pp 803–812
Latham GP, Locke EA (1991) Self-regulation through goal setting. Organ Behav Hum Decisi Process 50:212–247
Ledyard JO (1994) Public goods: a survey of experimental research. Public economics, University Library of Munich, Germany
Lee JY, Oh JC (2013) A model for recursive propagations of reputations in social networks. In: Proceedings of the 2013 IEEE/ACM international conference on advances in social networks analysis and mining, ASONAM ’13, ACM, New York, pp 666–670
Li B, Sun D, Lin Z, Ou C (2014) Agent-based simulation research on group emotion evolution of public emergency. In: ASONAM
Locke EA, Latham GP (1990) A theory of goal setting and task performance. Prentice-Hall, Englewood Cliffs
Luhmann CC, Rajaram S (2015) Memory transmission in small groups and large networks: an agent-based model. Psychol Sci 26(12):1909–17
Lustick I (2000) Agent-based modelling of collective identity: testing constructivist theory. Journal of Artificial Societies and Social Simulation, vol 3. no. 1. http://jasss.soc.surrey.ac.uk/JASSS.html
MacGregor N (2018) Living with the gods: on beliefs and peoples, 1st edn. Knopf, New York
Manchester W (1993) A world lit only by fire: the medieval mind and the renaissance: portrait of an age. Little, Brown and Company, Boston
Mason W, Watts DJ (2012) Collaborative learning in networks. Proc Natl Acad Sci 109(3):764–769
Mayzner MS, Tresselt ME (1958) Anagram solution times: a function of letter order and word frequency. J Exp Psychol 56(4):376
McAuliffe K, Dunham Y (2015) Group bias in cooperative norm enforcement. Philos Trans R Soc B 371:20150073-1–20150073-9
McFarland DA, Moody J, Diehl D, Smith JA, Thomas RJ (2014) Network ecology and adolescent social structure. Am Sociol Rev 79:1–34
Melucci A (1989) Nomads of the present: social movement and identity needs in contemporary society. Temple University Press, Philadelphia
Melucci A (1995) The process of collective identity. In: Klandermans B, Johnston H (eds) Social movements and culture. University of Minnesota Press, Minneapolis, pp 104–130
Miller DT, Ross M (1975) Self-serving biases in the attribution of causality: fact or fiction? Psychol Bull 82:213–225
Muller W (1996) How then, shall we live? Four simple questions that reveal the beauty and meaning of our lives. Bantam Books, New York
Nagel J (1996) American Indian ethnic renewal: red power and the resurgence of identity and culture. Oxford University Press, New York
Nguyen DA, Tan S, Ramanathan R, Yan X (2016) Analyzing information sharing strategies of users in online social networks. In: 2016 IEEE/ACM international conference on advances in social networks analysis and mining (ASONAM), pp 247–254
Nguyen C, Schlesinger KJ, Carlson JM (2017) Data-driven models for individual and group decision making. In: ASONAM, pp 852–859
Oldenquist A (1982) Loyalties. J Philos 79:173–193
Olson M (1965) The logic of collective action: public goods and the theory of groups. Harvard Univ. Press, Cambridge
Owens TJ (2006) Self and identity. In: Delamater J (ed) Handbook of social psychology. Springer, New York, pp 205–232
Paris WD, Budapest GC, Konstanz HDD, Bristol CG, Oregon KL, Stirling AO (1972) An experimental investigation into the formation of intergroup representations. Eur J Soc Psychol 2(2):202–204
Paxton A, Morgan TJH, Suchow JW, Griffiths T (2018) Interpersonal coordination of perception and memoryin real-time online social experiments. In: Proceedings of the 40th annual meeting of the cognitive science society, Austin
Peek L (2005) Becoming Muslim: the development of a religious identity. Sociol Relig 66(3):215–242
Perdue C, Dovidio JF, Gurtman MB, Tyler RB (1990) Us and them: social categorization and the process of intergroup bias. J Personal Soc Psychol 59:475–486
Pereira L, Moreira F (2005) Majority-vote model on random graphs. Phys Rev E Stat Nonlinear Soft Matter Phys 71:016123
Pfandler A, Rümmele S, Szeider S (2013) Backdoors to abduction. In: Proceedings of the 23rd international joint conference on artificial intelligence (IJCAI), pp 1046–1052
Pierce CS (1931) Elements of logic. In: Hartshorn C et al (eds) Collected papers of Charles sanders pierce. Harvard University Press, Harvard
Pilny A, Poole MS, Reichelmann A, Klein B (2017) A structurational group decision-making perspective on the commons dilemma: results from an online public goods game. J Appl Commun Res 45(4):413–428
Plutzer E, Zipp J (1996) Identity politics, partisanship, and voting for women candidates. Publ Opin Q 60(1):30–57. https://doi.org/10.1086/297738
Polletta F, Jasper JM (2001) Collective identity and social movements. Ann Rev Sociol 27:283–305
Qin M, Jin D, He D, Gabrys B, Musial K (2017) Adaptive community detection incorporating topology and content in social networks. In: Proceedings of the 2017 IEEE/ACM international conference on advances in social networks analysis and mining 2017, ASONAM ’17, ACM, New York, pp 675–682
Ren Y, Cedeno-Mieles V, Hu Z, Deng X, Adiga A, Barrett C, Ekanayake S, Goode BJ, Korkmaz G, Kuhlman CJ, Machi D, Marathe MV, Ramakrishnan N, Ravi SS, Saraf P, Self N (2018) Generative modeling of human behavior and social interactions using abductive analysis. In: 2018 IEEE/ACM international conference on advances in social networks analysis and mining (ASONAM), pp 413–420
Rousseau D, van der Veen AM (2005) The emergence of a shared identity: an agent-based computer simulation of idea diffusion. J Confl Resolut 49(5):686–712
Russell DG, Sarason IG (1965) Test anxiety, sex, and experimental conditions in relation to anagram solution. J Personal Soc Psychol 1:493–496
Salganik MJ, Watts DJ (2009) Web-based experiments for the study of collective social dynamics in cultural markets. topiCS 1(3):439–468
Sarason IG (1973a) Test anxiety and cognitive modeling. J Personal Soc Psychol 28:58–61
Sarason IG (1973b) Test anxiety and social influence. J Personal 41:261–271
Schelling TC (2006) Micromotives and macrobehavio, revised edn. W. W. Norton & Company, New York
Schubert TW, Otten S (2002) Overlap of self, ingroup, and outgroup: pictorial measures of self-categorization. Self Identity 1(4):353–376
Schweitzer M, Ordonez L, Dumaz B (2004) Goal-setting as a motivator of unethical behavior. Acad Manag J 47:422–433
Sethi R, Somanathan E (2006) A simple model of collective action. Econ Dev Cultural Change 54(3):725–747
Shanahan M (2005) Perception as abduction: turning sensor data into meaningful representation. Cognit Sci 29:103–134
Shank DB, Kashima Y, Saber S, Gale T, Kirley M (2015) Dilemma of dilemmas: how collective and individual perspectives can clarify the size dilemma in voluntary linear public goods dilemmas. PLoS One 10:1–19
Shannon CE (1948) A mathematical theory of communication. Bell Syst Tech J 27(3):379–423
Silke A (2008) Holy warriors: exploring the psychological processes of jihadi radicalization. Eur J Criminol 5(1):99–123
Singla P, Mooney RJ (2011) Abductive markov logic for plan recognition. In: Proceedings of the twenty-fifth AAAI conference on artificial intelligence
Smith K, Feher O, Culbertson J (2017) The influence of word-order harmony on structural priming in artificial languages. In: Proceedings of the 39th annual meeting of the cognitive science society, CogSci 2017, London, 16–29 July 2017
Snow D (2001) Collective identity and expressive forms. In: Smelser NJ, Baltes PB (eds) International encyclopedia of the social and behavioral sciences. Elsevier, Amsterdam, pp 2212–2219
Snow D, McAdams D (2000) Identity work processes in the context of social movements: clarifying the identity/movement nexus. In: Stryker S, Owens T, White RW (eds) Self, identity and social movements. University of Minneapolis Press, Minneapolis, pp 2212–2219
Stones CR (1983) Self-determination and attribution of responsibility: another look. Psychol Rep 53:391–394
Stout CT, Kretschmer K, Ruppanner L (2017) Gender linked fate, race/ethnicity, and the marriage gap in American politics. Polit Res Q 70(3):509–522
Stryker S (1980) Symbolic interactionism: a social structural version. Benjamin/Cummings, San Francisco
Suri S, Watts DJ (2011) Cooperation and contagion in web-based, networked public goods experiments. PLoS One 6:1–18
Sutton C, McCallum A (2011) An introduction to conditional random fields. Found Trends Mach Learn 4(4):267–373
Swann WB, Gomez A, Seyle DC, Morales JF, Huici C (2009) Identity fusion: the interplay of personal and social identities in extreme group behavior. J Personal Soc Psychol 96:955–1011
Swann WB, Gomez A, Dovidio JF, Hart S, Jetten J (2010a) Dying and killing for one’s group: Identity fusion moderates responses to intergroup versions of the trolley problem. Psychol Sci 21:1176–1183
Swann WB, Gomez A, Huici C, Morales JF (2010b) Identity fusion and self-sacrifice: Arousal as a catalyst of pro-group fighting, dying, and helping behavior. J Personal Soc Psychol 99:824–841
Swann WB, Gomez A, Buhrmester MD, Lopez-Rodriguez L, Jimenez J, Vazquez A (2014) Contemplating the ultimate sacrifice: identity fusion channels pro-group affect, cognition, and moral decision making. J Personal Soc Psychol 106:713–727
Swanson MS (2015) Composing democracy: Collective identity formation in small group composition. Ph.D. thesis, University of Washington, Washington
Tajfel H (1974) Social identity and intergroup behavior. Soc Sci Inf 13:65–93
Tanaka Y, Iwata T, Kurashima T, Toda H, Ueda N (2018) Estimating latent people flow without tracking individuals. In: Proceedings of the twenty-seventh international joint conference on artificial intelligence, IJCAI-18, international joint conferences on artificial intelligence organization, pp 3556–3563
Tarrow S (2010) Mentalities, political cultures, and collective action frames: constructing meanings through action. Sociol Compass 4:174–202
Tatum BD (2003) Why are all the black kids sitting together in the cafeteria? And other conversations about race, 2nd edn. Basic Books, New York
Taylor V, Whittier NE (1992) Collective identity in social movement communities: lesbian feminist mobilization. In: Morris AD, Mueller CM (eds) Frontiers of social movement theory. Yale University Press, New Haven, pp 104–130
Thagard P (1989) Explanatory coherence. Behav Brain Sci 12:435–502
Timmermans S (1999) Social death as a self-fulfilling prophecy: David Sudnow’s ‘passing on’ revisited. Sociol Q 39:453–472
Timmermans S, Tavory I (2012) Theory construction in qualitative research: from grounded theory to abductive analysis. Sociol Theory 30:167–186
Tran T, Lee K (2016) Understanding citizen reactions and ebola-related information propagation on social media. In: Proceedings of the 2016 IEEE/ACM international conference on advances in social networks analysis and mining, ASONAM ’16, IEEE Press, Piscataway, pp 106–111
Tresselt ME (1968) Reexamination of anagram problem solving. Trans N Y Acad Sci 30:1112–1119
van Dijk TA (2000) Ideology: a multidisciplinary approach. Sage, Thousand Oaks
van Maanen PP, van der Vecht B (2013) An agent-based approach to modeling online social influence. In: Proceedings of the 2013 IEEE/ACM international conference on advances in social networks analysis and mining, ASONAM ’13, ACM, New York, pp 600–607
van Zomeren M, Postmes T, Spears R (2008) Toward an integrative social identity model of collective action: a quantitative research synthesis of three socio-psychological perspectives. Psychol Bull 134(4):504
Vance RJ, Colella A (1990) Effects of two types of feedback on goal acceptance. J Appl Psychol 75:68–77
Vanderhaegen F, Caulier P (2011) A multi-viewpoint system to support abductive reasoning. Inf Sci 181:5349–5363
Verkuyten M, Yildiz AA (2007) National (dis)identification and ethnic and religious identity: a study among Turkish-Dutch Muslims. Personal Soc Psychol Bull 33(10):1448–1462
Vryan KD, Adler EA, Adler P (2003) Identity. In: Reynolds LT, Herman-Kinney NJ (eds) Handbook of symbolic interactionism. Altamira Press, Lanham, pp 367–390
Warren MW, Thomson WJ (1969) Anagram solution as a function of transition probabilities and solution word frequency. Psychon Sci 17(6):333–334
Wei-Kleiner F, Dragisic Z, Lambrix P (2014) Abduction framework for repairing incomplete el ontologies: complexity results and algorithms (extended version). In: Proceedings of the 28th AAAI conference on artificial intelligence
Wendt A (1994) Collective identity formation and the international state. Am Polit Sci Rev 88(2):384–396
Worchel S, Andreoli VA, Folger R (1977) Intergroup cooperation and intergroup attraction: the effect of previous interaction and outcome of combined effort. J Exp Soc Psychol 13:131–140
Zhang H, Vorobeychik Y, Letchford J, Lakkaraju K (2016) Data-driven agent-based modeling, with application to rooftop solar adoption. Auton Agents Multi-Agent Syst 30:1023–1049
Zhang H, Vorobeychik Y (2019) Empirically grounded agent-based models of innovation diffusion: a critical review. Artif Intell Rev 52:707–741
Acknowledgements
We thank the anonymous reviewers for their helpful feedback. We thank our colleagues at NSSAC and computer system administrators: Dominik Borkowski, Jason Decker, Miles Gentry, Jeremy Johnson, William Marmagas, Douglas McMaster, and Kevin Shinpaugh. This work has been partially supported by NSF CRISP 2.0 (Grant No. 1832587), DARPA Cooperative Agreement D17AC00003 (NGS2), DTRA CNIMS (Contract HDTRA1-11-D-0016-0001), DTRA Comprehensive National Incident Management System Contract HDTRA1-17-D-0023, NIH 1R01GM112938-01. The U.S. Government is authorized to reproduce and distribute reprints for Governmental purposes notwithstanding any copyright annotation thereon.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
A Supplemental related work
Related work topics that augment those in Sect. 3 are provided here. See Table 2 for a listing of all related work topics.
1.1 A.1 Individual anagram games: modeling
In Tresselt (1968), problem solving and verbal cues are analyzed with an anagram game. Tresselt (1968) modifies the H. Kendler and S. Kendler (1962) mediational model of problem-solving behavior (introducing word length and letter position), to understand anagram problem solving. This is a theoretical model of individual anagram games.
1.2 A.2 Individual anagram games: experiments and modeling
These works combine experiments and modeling. In Feather (1969), it was found that subjects who were initially confident of passing an anagram game test tended to attribute success to ability and failure to bad luck. However, subjects who were initially not confident tended to attribute success to good luck and failure to lack of ability. Results are discussed in terms of Heiderian theory and a valence-difficulty model. In Feather and Simon (1971a, b), two individuals played anagram games simultaneously but independently to test whether a person attributed her success (if she performed better) to skill versus good fortune, and failure to inferior skill or bad luck. Attributions were found to be dependent on expectations of players. Results are discussed in terms of models involving Heider’s principle of balance and his analysis of the causes of action, in terms of positivity biases in social perception, and as indicating effects of the social context of performance upon attribution and valence.
1.3 A.3 Modeling of CI
Lustick (2000), Rousseau and van der Veen (2005) use ABMs to study identity diffusion. An agent adopts (changes) her type of identity to that of a neighbor with a stronger (higher valued) type of identity. Hence, these are contagion processes and are implemented much like voter models (de Oliveira 1992; Pereira and Moreira 2005). Other works modeling collective identity (van Zomeren et al. 2008; Chen and Li 2009; Benjamin et al. 2016; Ackland and O’Neil 2011) are presented in Sect. 3.3.
1.4 A.4 Agent-based models of anagram games and formation of CI
The Charness et al. (2014) work in Sect. 3.6 has no modeling for the group anagram game. This motivated the online experiments and ABMs in Ren et al. (2018). This article is an expansion of Ren et al. (2018). In this work, we model the priming process of producing CI, which is the group anagram game. There are no ABMs (or models of any kind) of group anagram games, to our knowledge, other than ours.
1.5 A.5 Studies of phenomena related to CI
Many phenomena, such as in-group and out-group effects are related to CI. In Brewer and Silver (1978), Perdue et al. (1990), laboratory experiments with no interactions between subjects are performed. In Brewer and Silver (1978), it was found that bias in favor of the in-group on a reward allocation task was unaffected by the arbitrariness of classification into groups. An effort was made to assure that subjects in the arbitrary condition would not perceive the out-group as dissimilar. They found that similarity-dissimilarity of the out-group did not affect allocation bias as long as the in-group was perceived as similar to the subject. Subjects were divided clearly into groups labeled “dark” and “light”. Subjects then were asked to indicate their ratings first of “the other members of my group” and then of “the members of the other group” on a series of six-point bipolar scales (friendly-unfriendly; trustworthy-untrustworthy; cooperative-competitive; intelligent-stupid; weak-strong; generous-stingy; likeable-unlikeable). In Perdue et al. (1990), classical conditioning in-group and out-group descriptors (e.g., “us” and “them”) are used to establish evaluative responses to novel, unfamiliar targets. Nonsense syllables unobtrusively paired with in-group designating pronouns (e.g., “we”) were rated as more pleasant than syllables paired with out-group designators (e.g., “they”).
Paris et al. (1972) study how the anticipated interaction between groups determines the representations that groups have of each other. When students are categorized into groups, discrimination occurs such that the in-group is more favorably represented than the out-group before interaction takes place and also when no interaction is anticipated. Such discrimination is stronger when competitive interaction is anticipated in an important situation. In this condition, intergroup differences are also more easily projected on physical traits. Categorization is shown to be not only an independent variable but also a dependent variable in intergroup relations.
In Kahn and Ryen (1972), Own Group Bias (OGB) was measured by differences in pre and postgame scores on the evaluative scales of the Semantic Differential (SD).
In Shank et al. (2015), an experiment on Amazon Mechanical Turk was used to develop an agent-based simulation to understand how people’s motivations and behaviors within public goods dilemmas interact with the properties of the dilemma to lead to collective outcomes. They predict how the public good’s benefit and size, combined with controlling individual versus group properties, produce different levels of cooperation in public goods dilemmas.
In Sethi and Somanathan (2006), a simple model of collective action is presented as a framework for empirical research into the issue of when collective action in the commons will be successful.
In van Zomeren et al. (2008), an integrative social identity model of collective action (SIMCA) is developed that incorporates three socio-psychological perspectives on collective action. Instructions for coders were to answer different questions like “Does the measure of identification (used in this study) refer to a disadvantaged group or a social movement?”, “Is this group incidentally disadvantaged or structurally disadvantaged?”. Coders also rated the extent to which collective disadvantage was structural on a 5-point Likert-type scale ranging from 1 (not at all) to 5 (very much).
In Salganik and Watts (2009), new insights into the role of individual behavior on collective outcomes are obtained using a multiple-worlds experimental design in a web-based experiment in which 2930 participants listened to, rated, and download 48 songs by up-and-coming bands.
In Suri and Watts (2011), laboratory experiments with interactions between subjects are performed. Web-based experiments are conducted where 24 individuals played a local public goods game arranged on one of five network topologies that varied between disconnected cliques and a random regular graphs. It was found that although players did generally behave like conditional cooperators, they were as likely to decrease their contributions in response to low contributing neighbors as they were to increase their contributions in response to high contributing neighbors. They also found that positive effects of cooperation were contagious only to direct neighbors in the network.
In Capraro (2013), online experiments using Amazon Mechanical Turk were used to develop a predictive model of human cooperation able to organize a number of different experimental findings that are not explained by the standard model.
In Rousseau and van der Veen (2005), an agent-based computer simulation of identity change explores how changes in the attributes of the individual and/or elements of the environment influence the dependent variable: the degree of shared identity in a population.
There is a host of other studies that investigate phenomena such as cooperation and a person’s affinity for a group that are closely related to CI. In Worchel et al. (1977), Charness et al. (2007) laboratory experiments with interactions between subjects are performed. They study concepts such as group attraction and salience, respectively, which are related to CI. In Worchel et al. (1977), study groups worked cooperatively on two tasks and results were interpreted as showing that both previous interaction and success of combined effort are important variables in determining when intergroup cooperation will increase intergroup attraction. In Charness et al. (2007), groups perform two stage games as priming tasks, the Battle of the Sexes and Prisoner’s Dilemma. Results show that the salience of the group affects behavior of members, as well as the behavior of people in another group, and that participants anticipate these effects.
1.6 A.6 Data-driven: combining experiments and data-driven modeling
This section reports on works that combine experiments with data-driven modeling. These works cover explore-exploit networked experiments with limited modeling (Mason and Watts 2012); individual models of single-choice (i.e., one-shot) evacuation decisions (Nguyen et al. 2017); ABM of emotion and information contagions spreading on a network and comparisons with a single event (Li et al. 2014); and ABM of solar panel adoption and comparisons with data in San Diego county (Zhang et al. 2016). See Zhang and Vorobeychik (2019) for a review of innovation diffusion models. None of these works use ABMs to model networked experiments where individuals take a series of actions (that may be repeated) over time, to study CI, as we do.
In Luhmann and Rajaram (2015), small-scale laboratory experiments and an ABM were used to analyze the dynamics of collaborative inhibition. In Gates et al. (2017), the model in Luhmann and Rajaram (2015) was tested against human data collected in a large-scale experiment to find that participants demonstrate non-monotonicities not evident in the predictions. These unexpected results motivate more recent work in elucidating the algorithms underlying collaborative memory. In Paxton et al. (2018), using real-time online social experiments data, a statistical model is used to study interpersonal coordination in a “minimally interactive context” to explore how people become coupled in their perceptual and memory systems while performing a task together.
In contrast to the above works, where controlled experiments are used to produce data that are then used for modeling, there are many models based on observational data. We survey some of these works here.
In Korolov et al. (2016), the possibility of predicting a social protest (planned, or unplanned) based on social media messaging is studied. In Nguyen et al. (2016), to help increase the performance of retweet prediction, a flexible model under the framework of Random Forest classifier captures a number of behavior signals affecting user’s retweet decision. In Hu et al. (2014), a semantic model that can naturally represent various academic social networks, especially various complex semantic relationships among social actors, is presented. In Qin et al. (2017), the proposed method integrates topology and content of networks, and introduces a novel adaptive parameter for controlling the contribution of content with respect to the identified mismatch degree between the topological and content information. In Attema et al. (2015), data-driven multi-agent models predict Twitter trends. In van Maanen and van der Vecht (2013), a method that implements, validates, and improves an individual behavior model is proposed. The multi-agent model contains the social network structure, individual behavior parameters, and the scenario that are obtained from empirical data. In Lee and Oh (2013), emergence and propagation of reputations in social networks is modeled with a distributed algorithm. In Chierichetti et al. (2014), using several Twitter data sets, focusing in particular on the tweets sent during the soccer World Cup of 2010, a model of how users switch between producing information or sentiments and sharing others news or sentiments is developed. In Korolov et al. (2015), a theoretical analysis is developed for how social-chatter quantitatively relates to action via a superlinear scaling law.
Other works include using data from geotagged social media messages and data from mobile health applications (Tran and Lee 2016; Kurashima et al. 2018) In Tran and Lee (2016), to understand citizen reactions regarding Ebola, a large-scale data-driven analysis of geotagged social media messages is performed. In Kurashima et al. (2018), data from mobile health applications is used to develop a statistical model, called TIPAS (Time-varying, Interdependent, and Periodic Action Sequences). This approach is based on personalized, multivariate temporal point processes that model time-varying action propensities through a mixture of Gaussian intensities. Their model captures short-term and long-term periodic interdependencies between actions through Hawkes process-based self-excitations.
Clearly, much of the modeling of observational data is motivated by social media.
B Experimental data
This Appendix describes data from the game experiments of Sect. 4. In this section we present an analysis of the experimental data that illustrates how players interact in the anagram games. We focus on experimental data that are useful in modeling. We identify four main actions \(a_i \in A\), \(1 \le i \le 4\), in the set A of actions for a player during the game: (1) request letter from neighbor, (2) reply with letter to a request from a neighbor, (3) form and submit valid word, and (4) think (i.e., a no-op).
We define the following variables for the actions in the game:
-
When \(v_i\) sends a requests for a letter to \(v_j\), a request sent occurs.
-
When \(v_j\) receives the letter request from \(v_i\), a request received occurs.
-
When \(v_j\) replies with the letter requested from \(v_i\), a reply sent occurs.
-
When \(v_i\) receives the letter reply from \(v_j\), a reply received occurs.
-
When \(v_i\) uses its own letters to form a word, a word formed occurs.
Table 14 shows a summary of the section plots and the questions we answer with the analyses.
1.1 B.1 Timestamp for letter request
The number of letters a player can request through a game depends on the number of its neighbors. Each neighbor can share up to three letters (the initial three letters), so if a player has \(k=2\) neighbors, then six letters can be requested throughout the game. If a player has \(k=8\) neighbors, then 24 letters can be requested. We want to analyze the behavior of players with reference to the letter request action and answer the following questions. When do players request letters during the game? How does the number of neighbors affects the behavior of a player to request a letter in the game?
Figure 22 shows a histogram with 10 bins of 30-s each of timestamps for request sent, for 47 experiments with \(k= 2, 3, 4, 5, 6, 8\). A kernel-density estimation with Gaussian kernels is used to estimate the probability density function. It indicates that more letters are being requested during the first half of the 300-second anagram game. To analyze whether the number of neighbors affects the letter request, Figure B.1 in Appendix B.1.1 from Cedeno (2019) shows histograms with 10 bins of 30-s each for request sent for experiments with \(\hbox {k}= 2\), 3, 4, 5, 6, 8. The same trends exist for each value of k. However, if there are few neighbors (\(\hbox {k}=2\)) and consequently fewer available letters (3 letters per neighbor), there are fewer letter requests and letter replies near the end of the game.
Probability density distribution for time of request sent over the 300-s anagram game. Each of the bins on the x-axis corresponds to 30-s intervals. It shows experiments with \(k= 2, 3, 4, 5, 6, 8\). A kernel-density estimation with Gaussian kernels is used to estimate the probability density function. Letter requests are made throughout the game, rather than solely at the outset
1.2 B.2 Timestamp for letter reply sent
The number of letters a player can reply with, in response to letter requests, through a game depends on the number of its neighbors. Each neighbor can share up to 3 letters, so if a player has \(k=2\) neighbors, then 6 letters can be replied (when requested) at any time through the game, since the number of letters assigned initially is three. We want to analyze the behavior of players with reference to the letter reply action and answer the following questions. When do players reply letters during the game? How do the number of neighbors affects the behavior of a player to reply a letter in the game?
Figure 23 shows a histogram with 10 bins of 30 s each, for reply sent, for 47 experiments with \(k= 2, 3, 4, 5, 6, 8\). A kernel-density estimation with Gaussian kernels is used to estimate the probability density function. It indicates that letter requests are being replied to throughout the game, but more so at the earlier stages of the game. To analyze whether the number of neighbors affects the letter request, Figure B.2 in Appendix B.1.2 in Cedeno (2019) shows histograms with 10 bins of timestamp for reply sent for experiments with \(k= 2, 3, 4, 5, 6, 8\). Similar trends are obtained when data are broken down by k. We find that letter reply are made throughout the game, rather than solely at the outset.
Probability density distribution for time of reply sent over the 300-s anagram game. Each of the bins on the x-axis corresponds to 30-s intervals. It shows experiments with \(k= 2, 3, 4, 5, 6, 8\). A kernel-density estimation with Gaussian kernels is used to estimate the probability density function. Letter replies are made throughout the game, rather than solely at the outset
1.3 B.3 Time duration from sending a letter request to receiving the requested letter
When \(v_i\) requests a letter of \(v_j\), it has to wait for \(v_j\) to respond. Once \(v_j\) replies with the letter, then \(v_i\) is allowed to use the received letter and form words to contribute to the team. This time duration between request sent and reply received reveals how long players take to reply to their neighbors’ requests. A player only has to request a letter (and receive it) on one occasion to use it as any number of times in forming words. Remember that these rules were designed to foster word construction, to increase earnings potential, and to foster team cohesion. We want to analyze the behavior of players with reference to the time duration between the timestamps of the letter reply action and the letter request action, to answer the following questions. How long does it take for players to reply to a letter request? How does the number of neighbors affect the difference between the timestamps of the letter reply action and the letter request action?
Figure 24 shows a histogram with 10 bins of 30-s each, for the time difference between reply received and request sent, for 47 experiments with \(k=2, 3, 4, 5, 6, 8\). A kernel-density estimation with Gaussian kernels is used estimate the probability density function. Players generally respond relatively quickly to their neighbors letter requests with replies typically made within 30 s of the request.
Probability density distribution for time duration between requesting a letter and replying to the request, over the 300-s anagram game. Each of the bins on the x-axis corresponds to 30-s intervals. It shows experiments with \(k=2, 3, 4, 5, 6, 8\). A kernel-density estimation with Gaussian kernels is used to estimate the probability density function. Players generally respond relatively quickly to their neighbors letter requests, with replies typically made within 30 s of the request
To analyze whether this behavior is common while increasing the number of k neighbors in a game, Figure B.3 in Appendix B.1.3 in Cedeno (2019) shows histograms with 10 bins of 30-s each of timestamp change between reply received and request sent for experiments with \(k= 2, 3, 4, 5, 6, 8\). The number of neighbors doesn’t affect this type of action, players generally respond relatively quickly to their neighbors letter requests with replies typically made within 30 s of the request.
1.4 B.4 Timestamp for word formed
At any time during a game, a player can form a word and submit it for validation to our web application. If a player possesses letters to form a valid word, then she forms and submits a word, the application validates it, and the word is added to the game screen. We want to analyze the behavior of players with reference to the action of word formed and answer the following questions. When do players submit words during the game? How does the number of neighbors and the number of available letters affects the number of words formed by a player?
Figure 25 shows a histogram with 10 bins of 30-s each for word formed, for 47 experiments with \(k= 2, 3, 4, 5, 6, 8\). A kernel-density estimation with Gaussian kernels is used estimate the probability density function. It suggests that words are being formed throughout the game, and even up through the end of the game. This justifies a 5-min anagram game duration. To analyze whether the number of neighbors affects the word formation, Figure B.4 in Appendix B.1.4 in Cedeno (2019) shows histograms with 10 bins of 30-s each for timestamp of word formed for experiments with \(k= 2, 3, 4, 5, 6, 8\). Word submissions are made throughout the game, and the number of neighbors and available letters does not affect this behavior.
Probability density distribution for time of forming words over the 300-s anagram game. Each of the bins on the x-axis corresponds to 30-s intervals. It shows experiments with \(k= 2, 3, 4, 5, 6, 8\). A kernel-density estimation with Gaussian kernels is used to estimate the probability density function. Word submissions are made throughout the game, and the numbers of neighbors and available letters do not affect this type of action
C Modeling supplement
This Appendix contains several figures that support the modeling of Sect. 5. See Figs. 26 and 27.
Within each subfigure we show KL-divergence values for Baseline Model M0 across the five parameters of x at 1-min intervals: lower values are better. Each plot contains data over a time window: a 0–1 min, b 1–2 min, c 2–3 min, d 3–4 min and e 4–5 min, of the 5-min anagram game. The data are for conditions \((n=10, k=2)\). These plots show that request-related predictions are better than reply-related predictions over all time intervals. The reply-related predictions are better in the second half of the 5-min anagram games, but Fig. 23 shows that in experiments, there are fewer replies in the second half of the games
Within each subfigure we show KL-divergence values for the Baseline Model M0 (in green) and Model M1 (in red) across the five parameters of x: lower values are better. The modeling conditions are experiment with \(k=2\). Each plot contains data over a time window: a 0–1 min, b 1–2 min, c 2–3 min, d 3–4 min and e 4–5 min, of the 5-min anagram game. While Model M0 has good predictions for minute 3 and minute 5 (with the exception of the words formed), Model M1 has better predictions for minute 3 and minute 5 for all five x variables (color figure online)
Rights and permissions
About this article
Cite this article
Cedeno-Mieles, V., Hu, Z., Ren, Y. et al. Networked experiments and modeling for producing collective identity in a group of human subjects using an iterative abduction framework. Soc. Netw. Anal. Min. 10, 11 (2020). https://doi.org/10.1007/s13278-019-0620-8
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s13278-019-0620-8