Abstract
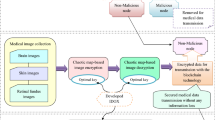
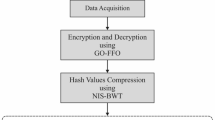
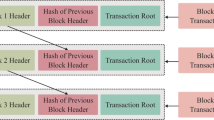
The Internet of Things (IoT) has made significant progress in the dissemination of healthcare data and corresponding mandatory actions in today’s world, where internet methods operate to automate and computerize numerous commercial as well as domestic applications. Data integrity and healthcare data distribution among privacy intermediate nodes are two major issues in the current scenario. Data must be encrypted to safeguard the confidentiality of sensitive data transferred between nodes, particularly healthcare-related data records. With the help of a trust modeling m-health application, these studies propose a novel method for medical image classification using cyber block chain Ccoud module-based image encryption. The medical image has been collected here, processed to remove noise, and the image has been resized. Using a fast convolution neural network (Fa_ConVolNet), this image has been classified. Then, the IoT cyber blockchain module-based Lorenz-Chaotic Encryption was used to encrypt this classified image. Machine learning and security analysis are used in the classification phase of parametric analysis. Accuracy, precision, recall, f-1 score, data security rate, PSNR, MSE, encryption time, and decryption time are the parameters analysed. It is also longer-lasting and more effective. Classification results obtained by proposed methodisexactness of 98%, correctness of 93%, recall of 92%, f-measure of 94% and network security analysis in terms of data security rate of 93%, PSNR of 77%, MSE of 78%, encryption time of 63 ms, decryption timeof 61 ms as.









Similar content being viewed by others
Data availability
Enquiries about data availability should be directed to the authors.
References
Ali A, Pasha MF, Ali J, Fang OH, Masud M, Jurcut AD, Alzain MA (2022) Deep learning based homomorphic secure search-able encryption for keyword search in blockchain healthcare system: a novel approach to cryptography. Sensors 22(2):528
Almaiah MA, Ali A, Hajjej F, Pasha MF, Alohali MA (2022) A lightweight hybrid deep learning privacy preserving model for FC-based industrial internet of medical things. Sensors 22(6):2112
Alqaralleh BA, Vaiyapuri T, Parvathy VS, Gupta D, Khanna A, Shankar K (2021) Blockchain-assisted secure image transmission and diagnosis model on Internet of Medical Things Environment. Personal Ubiquitous Comput. https://doi.org/10.1007/s00779-021-01543-2
Arumugam S, Shandilya SK, Bacanin N (2022) Federated learning-based privacy preservation with blockchain assistance in IoT 5G heterogeneous networks. J Web Eng https://doi.org/10.13052/jwe1540-9589.21414
El-Shafai W, Khallaf F, El-Rabaie ESM, El-Samie A, Fathi E (2022) Proposed neural SAE-based medical image cryptography framework using deep extracted features for smart IoT healthcare applications. Neural Comput Appl 34(13):10629–53
Jambhale T, Sudha M (2021) A privacy preserving hybrid neural-crypto computing-based image steganography for medical images. In: Intelligent data communication technologies and internet of things (pp. 277–290). Springer, Singapore
Joe CV, Raj JS (2021) Deniable authentication encryption for privacy protection using blockchain. J Artif Intell Capsule Netw 3(3):259–271
Kumar R, Wang W, Kumar J, Yang T, Khan A, Ali W, Ali I (2021) An integration of blockchain and AI for secure data sharing and detection of CT images for the hospitals. Comput Med Imaging Graph 87:101812
Liang W, Ji N (2021) Privacy challenges of IoT-based blockchain: a systematic review. Cluster Comput. https://doi.org/10.1007/s10586-021-03260-0
Nasir IM, Khan MA, Armghan A, Javed MY (2020) SCNN: a secure convolutional neural network using blockchain. In: 2020 2nd International Conference on Computer and Information Sciences (ICCIS) (pp. 1–5). IEEE
Neelakandan S, Rene Beulah J, Prathiba L, Murthy GLN, Irudaya Raj EF, Arulkumar N (2022) Blockchain with deep learning-enabled secure healthcare data transmission and diagnostic model. Int J Model Simul Sci Comput 13(04):2241006
Nguyen GN, Le Viet NH, Elhoseny M, Shankar K, Gupta BB, Abd El-Latif AA (2021) Secure blockchain enabled Cyber–physical systems in healthcare using deep belief network with ResNet model. J Parallel Distribut Comput 153:150–160
Rahman MA, Hossain MS, Islam MS, Alrajeh NA, Muhammad G (2020) Secure and provenance enhanced internet of health things framework: a blockchain managed federated learning approach. Ieee Access 8:205071–205087
Ramanan M, Singh L, Kumar AS, Suresh A, Sampathkumar A, Jain V, Bacanin N (2022) Secure blockchain enabled Cyber-Physical health systems using ensemble convolution neural network classification. Comput Electr Eng 101:108058
Rashmi P, Supriya MC, Hua Q (2022) Enhanced lorenz-chaotic encryption method for partial medical image encryption and data hiding in big data healthcare. Security Commun Networks
Udayakumar P, Rajagopalan N (2022) Blockchain enabled secure image transmission and diagnosis scheme in medical cyber-physical systems. J Electron Imaging 31(6):062002
Veeramakali T, Siva R, Sivakumar B, Senthil Mahesh PC, Krishnaraj N (2021) An intelligent internet of things-based secure healthcare framework using blockchain technology with an optimal deep learning model. J Supercomput 77(9):9576–9596
Waheed N, He X, Ikram M, Usman M, Hashmi SS, Usman M (2020) Security and privacy in IoT using machine learning and blockchain: Threats and countermeasures. ACM Comput Surveys 53(6):1–37
Funding
The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University, Abha, Kingdom of Saudi Arabia for funding this work through Large Groups RGP.2/119/43.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
All authors declare We don’t have any conflict of Interest.
Ethical approval
This article does not contain any studies with animals performed by any of the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Qamar, S. Machine learning in cloud-based trust modeling in M-health application using classification with image encryption. Soft Comput (2023). https://doi.org/10.1007/s00500-023-08145-5
Accepted:
Published:
DOI: https://doi.org/10.1007/s00500-023-08145-5