Abstract
Robust watermarking is an effective method and a promising solution for securing and protecting the copyright of digital images. Moments and moment invariants have become popular tools for robust watermarking due to their geometric invariance and favorable capability of image description. Many moments-based robust watermarking schemes have been proposed. However, there is a challenging problem of these schemes that should be addressed. One of these problems is to improve both imperceptibility and robustness. In contrast, the other problem, most of these schemes used inefficient, traditional computation methods of the moments, resulting in an inaccurate and inefficient performance of the watermarking schemes. To overcome these challenges, in this paper, we propose a novel robust color image-watermarking algorithm based on new multiple fractional multi-channel orthogonal moments, fractional-order exponent moments (MFrEMs), fractional-order polar harmonic transforms (MFrPHTs), and fractional-order radial harmonic Fourier moments (MFrRHFMs). Firstly, highly accurate fractional new multi-channel orthogonal moments are computed for the host color images. Then, more stable and accurate coefficients of fractional new multi-channel orthogonal moments are selected. Finally, a robust color image watermarking approach for multiple watermarks images is proposed based on MFrEMs, MFrPHTs, and MFrRHFMs using a 1D Sine chaotic map. The experimental results demonstrate that the proposed approach provides robustness against various attacks and better imperceptibility than the existing methods.
Similar content being viewed by others
1 Introduction
Nowadays, digital data transmission (images, documents, audios) has become increasingly and more manageable and faster because of the popularization of high-definition photography technology and the considerable development of communication technologies. Thanks to these technologies, a large volume of digital data is stored and shared on open platforms such as LinkedIn. Along with the rapid development of internet technology, image data have been widely used in various social networks, Facebook, Twitter, and Flickr [38]. Digital images are the most frequently used, shared/communicated on these platforms and it has been used widely in all aspects of life and work. It has played an increasingly important role in modern society in recent years [5, 12, 21, 22, 40].
Furthermore, in the age of big data, many digital images, particularly color images, are widespread in people’s lives, making them significantly convenient for storage applications and information processing. However, many digital images can be stored, copied, and distributed without distortion, falsification, or arbitrary spread without the copyright owner’s permission, posing a severe threat to the healthy development of the information industry.
Moreover, digital images can be reprinted indiscriminately on the Internet, resulting in many piracy cases and infringement of copyright owners’ legitimate rights and interests of digital images.
Therefore, the problem with copyright protection of digital color images is also becoming increasingly severe at the same time and has become an urgent problem to be solved. Digital watermarking has emerged as an effective technology and a potential solution for digital images’ copyright protection and content authentication. Digital watermarking technology can effectively prevent illegal copying, tampering, and digital content distribution [57].
Digital watermarking, based on its purposes, is categorized into three types- Semi-fragile [32], Fragile [28], and Robust watermarking [1]. A semi-fragile watermarking is suited for content authentication, while a fragile watermark is detectable and can be altered or erased; thus, it is used for integrity authentication. On the other side, a robust watermark is detectable and not erasable, and it is most suitable for copyright protection.
In recent years, significant progress has been made in robust image watermarking technology, and consequently, many outstanding research achievements have been made. Robust image watermarking technology is the leading way to protect digital image content copyrights [30, 39]. The main challenges [23] in watermarking schemes are to provide robustness against modification, compression, scaling, filtering, etc. Nowadays, the most robust image watermarking algorithms can effectively resist common attacks. Still, the effect of watermark extraction becomes unideal after a watermarked image is subjected to geometric attacks such as rotation, scaling, and flipping. Currently, geometric invariant methods are effective in resisting geometric attacks [58]. Constructing stable geometric invariants to resist global geometric attacks and improving the robustness of watermarking algorithms has become a key issue in robust image watermarking. Many researchers have focused on moment invariants-based watermarking in recent years. Alghoniemy et al. [2] introduced the first robust watermarking algorithm using the geometric moment invariants (i.e., Hu moments) in the digital watermarking technology. Since then, numerous research efforts have designed and introduced robust watermarking schemes using image moments and invariants [6, 20, 25, 48, 56]. A few of the abovementioned works have performed well in resisting various attacks, especially in resisting geometric attacks. However, these invariant watermarking methods have been developed for grayscale images. Color images, as compared to grayscale images, contain more information and are thus more attractive. Therefore, color image watermarking becomes one of the active research topics. Color image watermarking has become more critical than the watermarking of grayscale images. Due to their image representation capacity and geometric invariance, several watermarking schemes for color images based on quaternion moments have been proposed. Many invariant robust watermarks for color images have been presented [26, 29, 41, 44, 50, 53, 54]. However, these methods have some limitations:
-
(1)
The inaccurate traditional method, zero-order approximation (ZOA), is used to compute the quaternion moments.
-
(2)
There are instabilities and numerical errors, especially at big moment orders.
-
(3)
Because of inaccurate quaternion moments, there is low robustness and poor imperceptibility.
-
(4)
Some methods have weak resistance to geometric distortion.
-
(5)
The basis orthogonal functions are restricted to integer orders.
-
(6)
It isn’t easy to obtain the favorable trade-off between robustness and imperceptibility.
These moment-based methods for image watermarking were limited to the use of orthogonal moments of integer orders. These limitations motivated Hosny et al. to introduce quaternion Legendre–Fourier moments (QLFMs) [7] and quaternion radial-substituted Chebyshev moments (QRSCMs) [8] based watermarking methods for color images. Recently, moment-based watermarking algorithms with different chaotic maps were presented to increase security [3, 27, 34, 45,46,47]. Ma et al. [5] proposed a robust watermarking of gray-level images by combining a chaotic map with invariant accurate polar harmonic Fourier moments. Recent studies [13,14,15,16,17] have proved that polynomials with fractional orders better represent functions than their corresponding integer orders. Yamni et al. [51] used fractional-order Charlier moments for reconstructing and watermarking gray-level images. Yamni et al. [52] proposed a zero-watermarking scheme based on a new set of quaternion moments called Quaternion Radial Fractional Charlier Moments (QRFrCMs) for copyright protection color medical images. Recently, Hosny et al. [11] proposed a novel robust watermarking scheme of color images based on new accurate fractional-order multi-channel fractional polar harmonic transforms and a chaotic map.
With the remarkable characteristics of the new fractional-order orthogonal moments [11, 13,14,15,16,17], in this paper, we propose a robust watermarking algorithm to embed multiple watermark images in the host color image simultaneously. Firstly, basis functions of three types of fractional new multi-channel orthogonal moments are derived. Then an accurate three types of fractional new multi-channel orthogonal moments, namely, fractional-order exponent moments (MFrEMs), fractional-order polar harmonic transforms (MFrPHTs), and fractional-order radial harmonic Fourier moments (MFrRHFMs), are constructed using an exact integration and Gaussian numerical integration methods to compute the angular and radial kernels, respectively. Finally, a color image robust watermarking algorithm based on the multiple fractional multi-channel orthogonal moments, MFrEMs, MFrPHTs, and MFrRHFMs, and chaotic sine map is proposed, which has good robustness to various attacks and has high security. Experimental results show that the proposed algorithm can effectively resist geometric attacks and common image processing attacks. Compared with other existing robust watermarking algorithms, the proposed algorithm performs better and outperforms the existing algorithms.
The main contributions of this paper are as follows:
-
We proposed accurate multiple multi-channel orthogonal moments, MFrEMs, MFrPHTs, and MFrRHFMs.
-
We utilized the accurate multiple multi-channel orthogonal moments to develop a multiple-robust watermarking approach for color images.
-
We used 1D Sine chaotic map for scrambling the multiple watermarks to improve the security of the proposed scheme.
-
Solving the contradiction between robustness and imperceptibility, which improves the robustness of the watermarking
-
Experimental results show that the proposed scheme has a better trade-off between robustness and imperceptibility and superior robustness to image processing and geometric and attacks.
-
The proposed algorithm has superiority in terms of imperceptibility and robustness.
The remainder of this paper is organized as follows. Section 2 presents the proposed fractional-order multi-channel orthogonal moments and their geometric invariance. Section 3 describes the detailed process of the proposed watermarking algorithm. In Section 4, the experimental results are discussed in detail. Section 5 concludes this paper.
2 Fractional-order orthogonal moments
2.1 The definition of MFrEMs for RGB color images
The Exponent moments of integer-order are circular orthogonal moments [18]:
where Mpq is the EMs of order p (| p | ≥ 0) with repetition q (| q | ≥ 0), \( \hat{\mathrm{i}}=\sqrt{-1} \); [∙]∗ the complex conjugate; and basis function Epq(r, θ) is
with
The integer-order EMs are extended to FrEMs. The key to the construction of FrEMs is to construct the fractional-order radial polynomials; \( {T}_P^{FrEM}\left(r,\alpha \right) \), therefore, the extension of the orthogonal radial polynomial \( {T}_P^{EM}(r) \), is considered. The integer-order EMs are extended to FrEMs. Such extension mainly involves the modification of radial basis functions, \( {T}_P^{EM}(r) \). The radial basis functions of FrEMs are defined as [17]:
Then the basis function \( {H}_{pq}^{FrEM}\left(r,\theta \right) \) of the FrEMs is:
with a real-values parameter α ϵ R+.
The basis functions of fractional-order, \( {H}_{pq}^{FrEM}\left(r,\theta \right) \), are orthogonal within the range of [0, 1] × [0, 2π]:
Assuming that gc(r, θ) is an RGB color image in polar coordinates, which is represented according to the multi-channel approach [9, 35], where the R−, G− & B−channels expressed using gR(r, θ), gG(r, θ) & gB(r, θ) respectively. The definition of the multi-channel orthogonal fractional-order exponent moments MFrEMs are:
The image function, gC(r, θ), reconstructed as:
The reconstructed color image \( {g}_C^{recons.}\left(r,\theta \right) \) obtained using \( {g}_R^{recons.}\left(r,\theta \right),\kern0.5em {g}_G^{recons.}\left(r,\theta \right), \) and \( {g}_B^{recons.}\left(r,\theta \right) \). The quality of the reconstructed image improved as pmax & qmax increased.
2.2 The definition of MFrPHTs for RGB color images
Polar Complex Exponential Transform (PCET) of integer-order are circular orthogonal moments [55]:
where Dpq is the PCET of order p (| p | ≥ 0) with repetition q (| q | ≥ 0), \( \hat{\mathrm{i}}=\sqrt{-1} \); [∙]∗ the complex conjugate; and basis function Lpq(r, θ) is
With
The integer-order PCETs are extended to FrPCETs where the fractional-order radial polynomials; \( {T}_P^{FrPCET}\left(r,\alpha \right) \), is the extension of the orthogonal radial polynomial \( {T}_P^{PCET}(r) \). The radial basis functions of FrPCETs, \( {T}_P^{FrPCET}\left(r,\alpha \right) \) are defined as [13]:
Then the basis function \( {H}_{pq}^{FrPCET}\left(r,\theta \right) \) of the FrEMs is:
The basis functions of fractional-order, \( {H}_{pq}^{FrPCET}\left(r,\theta \right) \), are orthogonal within the range of [0, 1] × [0, 2π]:
The MFrPCET of gc(r, θ) are:
The image function, gC(r, θ), reconstructed as:
The reconstructed color image \( {g}_C^{recons.}\left(r,\theta \right) \) obtained using \( {g}_R^{recons.}\left(r,\theta \right),\kern0.5em {g}_G^{recons.}\left(r,\theta \right), \) and \( {g}_B^{recons.}\left(r,\theta \right) \). The quality of the reconstructed image improved as pmax & qmax increased.
2.3 The definition of MFrRHFMs for RGB color images
Radial harmonic Fourier moments (RHFMs) of integer-order are circular orthogonal moments is as follows [31]:
where Fpq is the RHFM of order p (p ≥ 0) with repetition q (| q | ≥0), \( \hat{\mathrm{i}}=\sqrt{-1} \); [∙]∗ the complex conjugate; and basis function Gpq(r, θ) is
With
The integer-order RHFMs are extended to FrRHFMs where the fractional-order radial polynomials; \( {T}_P^{FrRHFM}\left(r,\alpha \right) \), is the extension of the orthogonal radial polynomial \( {T}_P^{RHFM}(r) \). The radial basis functions of FrRHFMs, \( {T}_P^{FrRHFM}\left(r,\alpha \right) \) are defined as [14]:
Then the basis function \( {H}_{pq}^{FrRHFM}\left(r,\theta \right) \) of the FrRHFMs is:
The basis functions of fractional-order, \( {H}_{pq}^{FrRHFM}\left(r,\theta \right) \), are orthogonal within the range of [0, 1] × [0, 2π]:
The multi-channel orthogonal fractional-order radial harmonic Fourier moments are:
The image function, gC(r, θ), reconstructed as:
The reconstructed color image \( {g}_C^{recons.}\left(r,\theta \right) \) obtained using \( {g}_R^{recons.}\left(r,\theta \right),\kern0.5em {g}_G^{recons.}\left(r,\theta \right), \) and \( {g}_B^{recons.}\left(r,\theta \right) \). The quality of the reconstructed image improved as pmax & qmax increased.
2.4 Rotation, scale, and translation (RST) invariants
2.4.1 Rotation invariance
For the original color image, gC(r, θ), the rotated image with an angle β is while \( {g}_C^{\beta}\left(r,\theta \right) \), where:
The MFrEMs of \( {g}_C^{\beta}\left(r,\theta \right) \) is [17]:
Simply, we could write:
where \( {FM}_{pq}^{FrEM}\left({g}_C\right) \) and \( {FM}_{pq}^{FrEM}\left({g}_C^{\beta}\right) \) are the MFrEMs of, gC(r, θ)and \( {g}_C^{\beta}\left(r,\theta \right) \), respectively.
Since, |e−iqβ| = 1, for any value of q and β; therefore:
Then:
Equation (28) proves the MFrEMs are rotation invariant.
Similarly, the MFrPCET and MFrRHFM moments of the two images \( {g}_C^{\beta}\left(r,\theta \right) \) and gC(r, θ), are rotation invariant.
2.4.2 Scaling invariance
The scaling invariance of the multi-channels orthogonal circular moments is valid if these circular moments are computed in polar coordinates [43]. In the proposed method, the MFrEMs, the MFrPCETs, and MFrRHFMs are defined and calculated on the unit circle where input RGB color images are mapped. (See Fig. 1).
2.4.3 Translation invariance
Invariance to translation means shifting the coordinate origin to coincides with image centroid (xc, yc) [37] where xc & yc defined using geometric moments as:
The central MFrEMs are:
Similarly, the central MFrPCETs and MFrRHFMs are invariant to translation and defined as follows:
2.5 Accurate computation of fractional-order orthogonal moments
The proposed watermarking algorithm’s cornerstone is to compute accurate fractional-order orthogonal moments, MFrEMs, MFrPCETs, and MFrRHFMs using the highly accurate kernel-based approach [10], where the color images interpolated [49]. The MFrEMs computed as follows:
With:
The angular and radial kernels are defined as:
With:
The limits, Vi, j + 1, Vi, j, Ui + 1 & Ui are:
Based on the principles of Calculus, Jq(θij) computed in the exact form:
Unlike Jq(θij), calculating \( {I}_p^{FrEM}\left({r}_i\right); \) requires numerical integration. Accurate Gaussian integration [4] is our choice. The \( {I}_p^{FrEM}\left({r}_i\right) \) computed using as:
The symbols, wl & tl, refer to weights and the location l = 0, 1, 2, …. . c − 1 of sampling points; c is the order of the numerical integration. The values of wl are fixed and \( \sum \limits_{l=0}^{c-1}{w}_l=2 \). The values of tl can be expressed in terms of the limits of the integration Ui and Ui + 1.
Similar computational steps are derived to compute the MFrPCETs and MFrRHFMs of order p and repetition q as follow:
With:
Where:
The definite integral in eqs. (46) and (47) is evaluated by using the eq. (41) as follows:
3 Proposed watermarking scheme
The proposed watermarking algorithm will be described in two main stages in this section. The first stage describes the procedure of multiple watermark embedding, which will be described in detail. The second stage describes the procedure of multiple watermark extraction, which will be explained.
For the color image, gc, and multiple binary watermark images, the MFrEMs, MFrPCETs, and MFrRHFMs of the original image, respectively, are combined with a 1D Sine map to design new color images watermarking algorithm. This algorithm selected MFrEMs, MFrPCETs, and MFrRHFMs magnitudes, which are TSR invariants used to construct multiple robust watermarks. In contrast, the sine map is used in scrambling the multiple watermark images. Through the following subsection, we consider the host color image, gc, of size N × N while the multiple binary watermark images, W1, W2, and W3 of size P × Q where W1 = {w1(i, j) ∈ {0, 1}, 0 ≤ i < P, 0 ≤ j < Q}, W2 = {w2(i, j) ∈ {0, 1}, 0 ≤ i < P, 0 ≤ j < Q} and W3 = {w3(i, j) ∈ {0, 1}, 0 ≤ i < P, 0 ≤ j < Q}.
3.1 Multiple watermark embedding
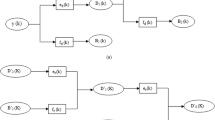
The process of multiple embedding is achieved through three steps. First, for the original image, the MFrEMs, MFrPCETs, and MFrRHFMs are computed, respectively. Second, the most significant TSR MFrEMs, MFrPCETs, and MFrRHFMs invariant are selected. Third, the multiple watermarks are embedded in the Red, Green, and Blue channels, gR, gG, and gB of the original image by using the selected moment invariants, MFrEMs, MFrPCETs, and MFrRHFMs. Figure 2 shows an illustrated flowchart of the embedding process, which can be summarized as the following steps:
-
1)
The multiple watermark images, W1, W2, and W3, converted to a one-dimensional vector, OW1 = {ow1(i) : 0 ≤ i < P × Q}, OW2 = {ow2(i) : 0 ≤ i < P × Q} and OW3 = {ow3(i) : 0 ≤ i < P × Q}, respectively. Then a chaotic sequence C of the length P × Q generated by using the Sine chaotic map [19] with the initial value of x0. This map is defined as follows:
The variable r is the control parameter of the Sine map, r ∈ [0, 1]. The chaotic sequence C = {c(i) : 0 ≤ i < P × Q} can be obtained using key K1 as the initial value of the Sine chaotic mapping, where the initial value of the Sine chaotic mapping multiple watermark sequence scrambled using Sine chaotic mapping [11] and a binarized chaotic sequence \( \hat{C}=\left\{\hat{c}(i),0\le i<P\times Q\right\} \) is obtained by binarizing C as follows:
Where T refers to the threshold, which is defined as the mean of C. Then, XOR operation is performed on OW1, OW2 and OW3 respectively with the binarized chaotic sequence \( \hat{\mathrm{C}} \) to obtain a chaotic scrambled multiple watermark sequence, \( {\hat{W}}_1 \), \( {\hat{\mathrm{W}}}_2 \) and \( {\hat{W}}_3 \):
-
2)
For each Red, Green, and Blue channel of the host image, the MFrEMs, MFrPCETs, and MFrRHFMs are computed according to a maximum moment order equals to P × Q [6].
-
3)
The magnitude values of MFrEMs, MFrPCETs, and MFrRHFMs are computed to assure the invariances. The MFrEMs, MFrPCETs, and MFrRHFMs with positive repetitions, q = 4m, m ∈ Z, are removed. The selected MFrEMs, MFrPCETs, and MFrRHFMs, SFrEM, SFrPCET, SFrRHFM, respectively are:
A P × Q number of MFrEMs, MFrPCETs, and MFrRHFMs coefficients, are randomly selected from the accurate coefficients MFrEMs, MFrPCETs, and MFrRHFMs set SFrEM, SFrPCET, SFrRHFM and their amplitudes are respectively MFrEM, MFrPCET and MFrRHFM.
-
4)
The multiple watermark bits embedded in the Red, Green, and Blue channels of the host color image using modulate selected MFrEMs, MFrPCETs, and MFrRHFMs, using the dither modulation function [48].
where mFrEM(i), mFrPCET(i) and mFrRHFM(i) refers to a vector that contains these magnitude values of selected MFrEMs, MFrPCETs, and MFrRHFMs, respectively. The vector length is equal to the number of multiple watermark bits; mFrEM′(i), mFrPCET′(i) and mFrRHFM′(i) refer to the modulated one; the [·] is the rounding operator; Δ refer to watermark quantization step; di(.) refers to the dither function where the elements of the dither vector are uniformly distributed over [0, ∆] and randomly generated.
-
5)
The inverse operation of MFrEMs, MFrPCETs, and MFrRHFMs applied to obtain the watermarked color image, \( {g}_c^w\left(r,\theta \right) \), as:
where gc(r, θ) denotes the original image, \( {g}_c^M\left(r,\theta \right) \) and \( {g}_c^{M^{\prime }}\left(r,\theta \right). \) The image components contributed by using unmodified and modified MFrEMs, MFrPCETs, and MFrRHFMs.
Based on the above steps, the pseudo-code of the embedding of the multiple watermarks can be described as follows.

3.2 Multiple watermark extraction
The process of multiple watermark extraction is an inverse process of the embedding one, where the multiple binary watermarks are extracted. First, the MFrEMs, MFrPCETs, and MFrRHFMs were computed for the watermarked image Red, Green, and Blue channels using the same accurate method. Second, a similar selection process was applied. Third, the same secret keys are employed. Finally, the multiple binary watermarks were extracted. Figure 3 shows a flowchart for the extraction process, which the detailed process of watermark extraction is described below.
-
1)
The MFrEMs, MFrPCETs, and MFrRHFMs of this attacked watermarked image were calculated using the same accurate method as described in sec. 2.5.
-
2)
The P × Q feature vector of MFrEMs, MFrPCETs, and MFrRHFMs,\( {M}_{FrEM}^{\ast }=\left\{{m}_{FrEM}^{\ast }(i),\kern0.5em 0\le i<P\times Q\right\} \), \( {M}_{FrPCET}^{\ast }=\left\{{m}_{FrPCET}^{\ast }(i),\kern0.5em 0\le i<P\times Q\right\} \) and \( {M}_{FrRHFM}^{\ast }=\left\{{m}_{FrRHFM}^{\ast }(i),\kern0.5em 0\le i<P\times Q\right\} \) respectively are selected by using the same secret key, K2, which is a symmetric key for the embedding and extraction processes.
-
3)
The selected MFrEMs, MFrPCETs, and MFrRHFMs magnitudes were extracted using the same quantization process as:
A bit \( {\hat{\mathrm{w}}}_1^{\ast}\left(\mathrm{i}\right) \), \( {\hat{\mathrm{w}}}_2^{\ast}\left(\mathrm{i}\right) \) and \( {\hat{\mathrm{w}}}_3^{\ast}\left(\mathrm{i}\right) \) are either 0 or 1 based on the value \( {\mathrm{m}}_{FrEM}^{\ast}\left(\mathrm{i}\right) \), \( {\mathrm{m}}_{FrPCET}^{\ast}\left(\mathrm{i}\right) \) and \( {\mathrm{m}}_{FrRHFM}^{\ast}\left(\mathrm{i}\right) \) where:
The \( {\hat{\mathrm{w}}}_1^{\ast}\left(\mathrm{i}\right) \), \( {\hat{\mathrm{w}}}_2^{\ast}\left(\mathrm{i}\right) \) and \( {\hat{\mathrm{w}}}_3^{\ast}\left(\mathrm{i}\right) \) called a minimum distance decoder.
-
4)
The multiple one-dimensional watermarks, \( {OW}_1^{\ast } \), \( O{W}_2^{\ast } \) and \( {OW}_3^{\ast } \) obtained by performing reverse Sine mapping and scrambling of \( {\hat{W}}_1^{\ast }=\left\{{\hat{w}}_1^{\ast }(i),0\le i<P\times Q\right\} \) using key K1. Then, \( {OW}_1^{\ast }=\left\{{ow}_1^{\ast }(i),0\le i<P\times Q\right\} \), \( O{W}_2^{\ast }=\left\{\mathrm{o}{w}_2^{\ast }(i),0\le i<P\times Q\right\} \) and \( {OW}_3^{\ast }=\left\{{ow}_3^{\ast }(i),0\le i<P\times Q\right\} \) are transformed into a two-dimensional binary multiple watermarks \( {W}_1^{\ast }=\left\{{w}_1^{\ast}\left(i,j\right)\in \left\{0,1\right\},0\le i<P,0\le j<Q\right\} \), \( {W}_2^{\ast }=\left\{{w}_2^{\ast}\left(i,j\right)\in \left\{0,1\right\},0\le i<P,0\le j<Q\right\} \) and \( {W}_3^{\ast }=\left\{{w}_3^{\ast}\left(i,j\right)\in \left\{0,1\right\},0\le i<P,0\le j<Q\right\} \).
Based on the above steps, the pseudo-code of the extraction of the multiple watermarks can be described as follows:

4 Experiments
This section performs various experiments to evaluate the proposed watermarking algorithm regarding visual imperceptibility and the robustness analysis against potential attacks. We conducted all experiments on selected color images from the dataset of birds [24] which contains 600 images (100 samples each) of six different classes of birds (Egret, Mandarin, owl, puffin, toucan, and wood duck). The images are RGB color JPEG with different dimensions (e.g., 539 × 570, 400 × 600).
All selected color images are resized with unified dimensions, 512 × 512, as shown in Fig. 4a–e. Besides, we selected five standard color images from the USC-SIP image database [42] with the size 512 × 512 as host images, as shown in Fig. 4f–j. Binary images as watermark images with the size 64 × 64 as shown in Fig. 5. All experiments are implemented in MATLAB (R2015a) on a personal computer with 1.9 GHz Core (™) i7 and 8 GB RAM.
4.1 Watermark imperceptibility
The peak signal-to-noise ratio (PSNR) is a standard quantitative measure used to evaluate visual imperceptibility.
The PSNR of the watermarked image, \( {g}_c^w \), and the original image, gc, is [33]:
where
For a fair comparison, the compared methods [7, 8, 44, 50] are used to embed a single watermark in the host color images. Therefore, the imperceptibility of the proposed watermark algorithm is evaluated by embedding a 128-bit watermark sequence into the ten standard color images with Δ ∈ [0.2,0.4,0.6,0.8,1.0]. In which, we compute the proposed, MFrEMs, MFrPHTs and MFrRHFMs with α = 1.7 and the existing compared methods [7, 8, 44, 50] then, we used the amplitude of MFrEMs, MFrPHTs and MFrRHFMs and the existing compared methods [7, 8, 44, 50] in the embedding a 128-bit watermark sequence in host color images. For each generated watermarked image, the average PSNR values are calculated for the proposed algorithm.
The compared algorithms [7, 8, 44, 50] and the relationship between the average PSNR of watermarked images and the quantization step are shown in Fig. 6. Table 1 reports the average PSNR for different quantization steps.
As shown in Fig. 6 and Table 1, the average PSNR decreases as the watermark quantization step increases. As we know, when the PSNR is>38 dB, the watermarking algorithms can achieve superb imperceptibility. The watermarking algorithm achieved the highest values of PSNR, where all PSNR values PSNR >38 dB, which means that the proposed algorithm achieves outstanding watermark imperceptibility and the proposed watermark algorithm outperformed those in [7, 8, 44, 50].
4.2 Watermark robustness analysis
The most used performance evaluation metrics to test the robustness of digital watermarking against attacks are the bit error rate (BER) and the normalized correlation (NC). The BER and NC describe the similarity of two images, the original and extracted watermark. The larger NC and the smaller BER denote that the original and extracted watermark is more similar. When the original and extracted watermark is the same, the watermarking algorithms have an NC and BER are 1 and 0, respectively, and the watermark is more robust. The BER and NC, respectively defined as [36]:
Where W & W∗ refer to original and extracted watermarks.
4.2.1 Multiple watermark extraction
In this subsection, we perform various experiments to evaluate the robustness of the proposed watermarking algorithm to various attacks, including JPEG compression, Salt and Peppers noise, Gaussian noise, filtering, and median filtering, Rotation, Scaling, and Flipping. As the proposed algorithm embeds multiple watermarks in the Red, Green, and Blue channels, gR, gG, and gB, of an original color image using the MFrEMs, MFrPCETs, MFrRHFMs, BER, and NC defined by Eqs. (60) and (61), respectively, are used to measure the robustness of the algorithm where the multiple watermarks are extracted from the Red, Green, and Blue channels, gR, gG, and gB, of the original color image.
-
1.
JPEG compression attack
To test the robustness of the proposed algorithm against the JPEG compression attack, we use compression quality factors, QF = 50, 70, and 90, on the color image. Figure 7 shows represent color images after JPEG compression attacks of different compression quality factors. Table 2 reports the obtained results of BER and NC values under the JPEG compression attacks for the multiple extracted watermarks from the three channels, Red, Green, and Blue of the color image, simultaneously. It can be seen from Table 2 that the extracted watermarks have a higher quality with lower BER and higher NC values.
The results of this experiment prove that the proposed algorithm can effectively resist JPEG compression attacks.
-
2.
Noise attack
To test the robustness of the proposed algorithm against the noise attacks, Matlab statements, C = imnoise(C, ‘gaussian’, m, v), is used to add Gaussian white noise of mean m and variance v to the image C and B = imnoise (B, ‘salt & pepper”, d), is used to add salt and pepper noise to the image B, where d is the noise density. In this experiment, Gaussian noise with (m = 0, v = 0.02), (m = 0, v = 0.04) for mean and variance value, pepper & salt noise with (d = 0.02) and (d = 0.04) are added to the original color image. Figure 8 shows the color image after adding different noises. Table 3 shows the obtained results of BER and NC values under the noise attacks for the extracted watermarks from the three channels, Red, Green, and Blue, of the color image, simultaneously. It can be seen from Table 3 that the extracted watermarks are closer to the original ones with lower BER and higher NC values. The results of this experiment ensure that the proposed algorithm is highly robust to noise attacks.
-
3.
Filtering attack
Here, three kinds of filtering are used to test the robustness of the proposed algorithm to filtering attacks. We perform median filtering, Gaussian filtering, and average filtering on the original color image with a filtering window of 3 × 3, respectively. The color images after the filtering attacks are displayed in Fig. 9. The obtained results of extraction watermarks with their corresponding BER and NC values are shown in Table 4. It can be seen from the results that the proposed algorithm has good robustness to filtering attacks.
-
4.
Rotation attack
As one of the geometric attacks, rotation attacks are used to test the robustness of the proposed algorithm. We rotate the original color image by the rotation angles, θ = 15o, 30o, 45o. Figure 10 shows the color images after being subjected to rotation attacks; the BER and NC values for each extracted watermark are reported in Table 5.
It can be seen from the results in Table 5 that extracted watermarks are recognizable with values of BER and NC approaches to the optimum values 0 and 1, respectively. These results ensure the robustness of the proposed algorithm against rotation.
-
5.
Scaling attack
Here, a scaling attack, a common one of the geometric attacks, is used to test the robustness of the proposed algorithm. We scaled the color images by scaling factors S = 0.75, 1.5, 2.0. Figure 11 shows the scaled color images. Table 6 presents the obtained results of BER and NC values for each extracted watermark under scaling attacks. As shown from Table 6, the extracted watermarks are closer to the original one in Fig. 5. The results confirm the proposed algorithm has good robustness against scaling attacks with reduction and magnification scaling factors.
-
6.
Flipping attack
To test the robustness of the proposed algorithm toward the flipping attacks. We perform flipping horizontally and vertically to the original color image. Figure 12 shows the color images after flipping attacks. Table 7 shows the values of BER and NC for the extracted watermarks. As shown in Table 7, the proposed algorithm can effectively extract multiple watermarks even with flipping attacks. It can be shown from the results in Table 7 that extracted watermarks are recognizable with values of lower BER, and higher NC values approach to the optimum values 0 and 1, respectively. These results ensure the robustness of the proposed algorithm against flipping attacks.
4.3 Comparison of robustness with similar algorithms
In this section, the experiment was performed to verify the superiority of the proposed algorithm; the proposed algorithm was compared with other robust watermarking algorithms [7, 8, 26, 44, 50]. The existing algorithms [7, 8, 26, 44, 50] are used to embed a single watermark in the host color images, while the proposed algorithm can be used for single and multiple watermarks.
We perform all comparisons to embed a single watermark in the host color images for a fair comparison. Ten binary watermarks of 32 × 32 pixels are embedded in the ten host images using the proposed scheme and another quaternion moment-based watermarking algorithm [7, 8, 26, 44, 50]. Then, a total of 10 × 10 = 100 watermarked color images are generated. For each watermarked color image, the average values of BER and NC are computed for extracted watermark under geometric distortions and different common attacks. Tables 8 and 9 reports the average values of BER and NC, respectively.
It can be seen from the results in Tables 8 and 9 that the robust watermarking scheme based on fractional multi-channels orthogonal moments proposed in this paper has significantly better performance in resisting standard image processing and geometric attacks than the compared methods in [7, 8, 26, 44, 50]. The better performance of the proposed algorithm occurs because of the highly accurate computation method used to compute the new fractional multi-channels orthogonal moments, which has numerical stability and better accuracy. Besides, the new fractional multi-channels orthogonal moments have a remarkable characteristic in image description and representation compared to the others with integer orders in [7, 8, 26, 44, 50].
As a result, the proposed robust method is more robust and resistant to various attacks. On the other side, most quaternion moments-based watermarking algorithms utilize the zeroth-order approximation (ZOA) method in Cartesian coordinate. This traditional method has poor accuracy and produces two standard errors, numerical integration and geometric errors. Therefore, the watermarking schemes have a result in poor robustness of the extracted watermark. The experimental results and the above analysis show that the proposed robust watermarking scheme has better robustness towards typical geometric and image processing attacks. The proposed algorithm is better than other compared watermarking schemes in terms of robustness and imperceptibility.
5 Conclusion
In this paper, a novel robust watermarking algorithm for color image based on multiple accurate MFrEMs, MFrPHTs, and MFrRHFMs and a 1D Sine mapping has been proposed. The proposed scheme uses a 1D Sine chaotic map for enhancing the security by scrambling the multiple watermarks images where these scrambled multiple watermarks bits are embedded into original color images by adapting the magnitudes of MFrEMs, MFrPHTs, and MFrRHFMs. Experimental results have shown that the performance of the proposed scheme is superior to existing methods in terms of imperceptibility and watermark robustness.
Additionally, it is demonstrated by experimental results that the robust watermarking scheme provides resistance against the different common geometric and image processing attacks. Moreover, it proved that the proposed scheme achieves a good trade-off between robustness and imperceptibility. We will improve the proposed algorithm to deal with dual and multiple color images simultaneously in future work.
Extension of this approach to robust zero watermarking to solve the problem of conflicting between discriminability and robustness. Moreover, in our plan, we will extend the proposal to medical applications.
References
Agarwal N, Singh AK, Singh PK (2019) Survey of robust and imperceptible watermarking. Multimed Tools Appl 78(7):8603–8633. https://doi.org/10.1007/s11042-018-7128-5
Alghoniemy M, Tewfik AH (2000) Geometric distortion correction through image normalization. In: Proceedings of IEEE international conference on multimedia and expo. IEEE, New York, pp 1291–1294
Darwish MM, Kamal ST, Hosny KM (2020) Improved color image watermarking using logistic maps and quaternion Legendre-Fourier moments. Studies in computational intelligence. Springer, 884, p. 137–158. https://doi.org/10.1007/978-3-030-38700-6_6).
Faires JD, Burden RL (2002) Numerical methods, third edn. Brooks Cole Publication
Fang D, Sun S (March 2018) A new scheme for image steganography based on Hyperchaotic map and DNA sequence. J Inf Hiding Multimed Signal Process 9(2):392–399
Hosny KM, Darwish MM (2017) Invariant image watermarking using accurate polar harmonic transforms. Comput Electr Eng 62:429–447
Hosny KM, Darwish MM (2018) Robust color image watermarking using invariant quaternion Legendre-Fourier moments. Multimed Tools Appl 77(19):24727–24750
Hosny KM, Darwish MM (2019) Resilient color image watermarking using accurate quaternion radial substituted Chebyshev moments. ACM Trans Multimed Comput Commun Appl 15(2):24727–24750
Hosny KM, Darwish MM (2019) New set of multi-channel orthogonal moments for color image representation and recognition. Pattern Recogn 88:153–173
Hosny KM, Darwish MM (2019) A kernel-based method for fast and accurate computation of PHT in polar coordinates. J Real Time Image Processing 16(4):1235–1247
Hosny KM, Darwish MM (2021) Reversible color image watermarking using fractional-order polar harmonic transforms and a chaotic sine map. Circuits Syst Signal Process 40:6121–6145
Hosny KM, Darwish MM, Li K, Salah A (Dec. 2018) Parallel multi-core CPU and GPU for fast and robust medical image watermarking. IEEE Access 6:77212–77225
Hosny KM, Darwish MM, Aboelenen T (2020) Novel fractional-order polar harmonic transforms for gray-scale and color image analysis. J Franklin Institute 357(4):2533–2560
Hosny KM, Darwish MM, Eltoukhy MM (2020) Novel multi-channel fractional-order radial harmonic Fourier moments for color image analysis. IEEE Access 8:40732–40743
Hosny KM, Darwish MM, Aboelenan T (2020) Novel fractional-order generic Jacobi-Fourier moments for image analysis. Signal Process 172:107545
K. M. Hosny, M. M. Darwish, and T. Aboelenan, "New fractional-order Legendre-Fourier moments for pattern recognition applications," Pattern Recogn, Volume 103, 107324, p.1–19, 2020.
Hosny KM, Abd Elaziz M, Darwish MM (2021) Color face recognition using novel fractional-order multi-channel exponent moments. Neural Comput Appl Neural Comput Appl 33:5419–5435
Hu H-t, Zhang Y-d, Shao C, Ju Q (2014) Orthogonal moments based on exponent functions: exponent-Fourier moments. Pattern Recogn 47:2596–2606
Hua Z, Zhou Y, Huang H (2019) Cosine-transform-based chaotic system for image encryption. Inf Sci 480:403–419
Ismail IA, Shuman MA, Hosny KM, Abdel Salam HM (2010) Invariant image watermarking using accurate Zernike moments. J Comput Sci 6(1):52–59
Kahlessenane F, Khaldi A, Kafi R, Euschi S (2021) A robust blind medical image watermarking approach for telemedicine applications. Clust Comput 24:1–14
Kamili A, Hurrah NN, Parah SA, Bhat GM, Muhammad K (2020) DWFCAT: dual watermarking framework for industrial image authentication and tamper localization. IEEE Trans Industr Inform 17(7):5108–5117
Kumar S, Singh BK, Yadav M (2020) A recent survey on multimedia and database watermarking. Multimed Tools Appl 79(27):20149–20197
Lazebnik S, Schmid C, Ponce J (2005) A maximum entropy framework for part-based texture and object recognition. Proc IEEE Int Conf Comput Vis Beijing China 1:832–838
Li L, S. Li, A. Abraham, and J. Pan, "Geometrically invariant image watermarking using polar harmonic transforms," Inform Sci, Vol. 199, pp.1–19, 2012.
Liu Y, Zhang S, Yang J (2020) Color image watermark decoder by modeling quaternion polar harmonic transform with BKF distribution. Signal Process Image Commun 88:115946
Ma B, Chang L, Wang C, Li J, Wang X, Shi Y-Q (2020) Robust image watermarking using invariant accurate polar harmonic Fourier moments and chaotic mapping. Signal Process 172:107544. https://doi.org/10.1016/j.sigpro.2020.107544
Nguyen T-S (2021) Fragile watermarking for image authentication based on DWT-SVD-DCT techniques. Multimed Tools Appl 80:1–13
Niu P, Wang P, Liu Y, Yang H, Wang X (2015) Invariant color image watermarking approach using quaternion radial harmonic Fourier moments. Multimed Tools Appl
Ray A, Roy S (2020) Recent trends in image watermarking techniques for copyright protection: a survey. Int J Multimed Inf Retr:1–22
Ren HP, Ping ZL, Bo WRG, Wu WK, Sheng YL (2003) Multidistortion-invariant image recognition with radial harmonic Fourier moments. J Opt Soc Am A 20:631–637
Rhayma H, Makhloufi A, Hamam H, Hamida AB (2021) Semi-fragile watermarking scheme based on perceptual hash function (PHF) for image tampering detection. Multimed Tools Appl:1–20
Salomon D (2007). Data compression: The complete reference (4 ed.). Springer. ISBN 978-1846286025
Shao Z, Shang YY, Zhang Y, Liu X, Guo G (2016) Robust watermarking using orthogonal Fourier–Mellin moments and chaotic map for double images. Signal Process 120:522–531
Singh C, Singh J (2018) Multi-channel versus quaternion orthogonal rotation invariant moments for color image representation. Digital Signal Process 78:376–392
Singh AK, Kumar B, Singh G, Mohan A (eds) (2017) Medical image watermarking: techniques and applications. Springer, ISBN: 978-3-319-86227-9).
Suk T, Flusser J (2009) Affine moment invariants of color images. In: International Conference on Computer Analysis of Images and Patterns, pp 334–341
Sun W, Zhou J, Li Y, Cheung M, She J (2020) Robust high-capacity watermarking over online social network shared images. IEEE Trans Circuits Syst Video Technol 31(3):1208–1221
Tarhouni N, Charfeddine M, Amar CB (2020) Novel and robust image watermarking for copyright protection and integrity control. Circuits Syst Signal Process 39(10):5059–5103
Thanki R, Kothari A, Borra S (2021) Hybrid, blind and robust image watermarking: RDWT–NSCT based secure approach for telemedicine applications. Multimed Tools Appl 80:1–21
Tsougenis E, Papakostas G, Koulouriotis D, Karakasis E (2014) Adaptive color image watermarking by the use of quaternion image moments. Expert Syst Appl 41(14):6408–6418
USC-SIPI image database, http://sipi.usc.edu/database, 2015
Wang X-y, Li W-y, Yang H-y, Wang P, Li Y-w (2015) Quaternion polar complex exponential transform for invariant color image description. Appl Math Comput 256:951–967
Wang XY, Yang HY, Niu PP, Wang CP (2016) Quaternion exponent moments based robust color image watermarking. J Comput Res Dev 53:651–665
Wang C-p, Wang X-y, Chen X-j, Zhang C (2017) Robust zero-watermarking algorithm based on polar complex exponential transform and logistic mapping. Multimed Tools Appl 76(24):26355–26376. https://doi.org/10.1007/s11042-016-4130-7
Xia Z, Wang X, Zhou W, Li R, Wang C, Zhang C (2019) Color medical image lossless watermarking using chaotic system and accurate quaternion polar harmonic transforms. Signal Process 157:108–118
Xia Z, Xingyuan W, Xiaoxiao L, Chunpeng W, Unar S, Mingxu W, Tingting Z (2019) Efficient copyright protection for three CT images based on quaternion polar harmonic Fourier moments. Signal Process 164:368–379
Xin Y, Liao S, Pawlak M (2007) Circularly orthogonal moments for geometrically robust image watermarking. Pattern Recogn 40:3740–3752
Xin Y, Pawlak M, Liao S (2007) Accurate computation of Zernike moments in polar coordinates. IEEE Trans Image Process 16(2):581–587
Xu H, Kang X, Chen Y, Wang Y (Apr. 2019) Rotation and scale invariant image watermarking based on polar harmonic transforms. Optik 183:401–414
M. Yamni, A. Daoui, O. El Ogri, H. Karmouni, M. Sayyouri, H. Qjidaa, and J. Flusser, "Fractional Charlier moments for image reconstruction and image watermarking," Signal Process, Volume 171, 107509, 2020.
Yamni M, Karmouni H, Sayyouri M, Qjidaa H (2021) Robust zero-watermarking scheme based on novel quaternion radial fractional Charlier moments. Multimed Tools Appl 80(14):21679–21708
Yang H, Zhang Y, Wang P, Wang X, Wang C (2014) A geometric correction based robust color image watermarking scheme using quaternion exponent moments. Optik 125:4456–4469
Yang HY, Wang XY, Niu PP, Wang AL (2015) Robust color image watermarking using geometric invariant quaternion polar harmonic transform. ACM Trans Multimed Comput Commun Appl 11(3):1–26
Yap P, Jiang X, Kot AC (2010) Two dimensional polar harmonic transforms for invariant image representation. IEEE Trans Pattern Anal Mach Intell 32:1259–1270
Yuan X-C, Pun C-M, Chen C-LP (2013) Geometric invariant watermarking by local Zernike moments of binary image patches. Signal Process 93(7):2087–2095
Zear A, Singh PK (2021) Secure and robust color image dual watermarking based on LWT-DCT-SVD. Multimed Tools Appl:1–18
Zheng D, Liu Y, Zhao J, Saddik AE (2007) A survey of RST invariant image watermarking algorithms. ACM Comput. Surv 39
Funding
Open access funding provided by The Science, Technology & Innovation Funding Authority (STDF) in cooperation with The Egyptian Knowledge Bank (EKB).
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors have no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Hosny, K.M., Darwish, M.M. Robust color image watermarking using multiple fractional-order moments and chaotic map. Multimed Tools Appl 81, 24347–24375 (2022). https://doi.org/10.1007/s11042-022-12282-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-022-12282-8