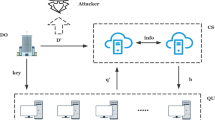
Abstract
To utilize the cost-saving advantages of the cloud computing paradigm, individuals and enterprises increasingly resort to outsource their databases and data operations to cloud servers. However such solutions come with the risk of violating the privacy of users. To protect privacy, the outsourced databases are usually encrypted, making it difficult to run queries and other data mining tasks without decrypting the data first. Conventional encryption methods are either incapable of supporting such operations or computationally expensive to do so. In this paper, we aim to efficiently support computations over encrypted cloud databases, particularly focusing on privacy preserving k-nearest neighbor classification. The proposed scheme efficiently protects database security, key confidentiality of the data owner, query privacy and data access patterns. We analyze the cost of our proposed scheme and evaluate the performance through extensive experiments using both synthetic and real databases.








Similar content being viewed by others
References
Aggarwal, C.C., Philip. S.Y.: A general survey of privacy-preserving data mining models and algorithms. In: Privacy-preserving data mining, pp. 11–52. Springer, Berlin (2008)
Agrawal, R., Kiernan, J., Srikant, R., Xu, Y.: Order preserving encryption for numeric data. In: Proceedings of the ACM SIGMOD international conference on management of data, p 2004. ACM, New York (2004)
Bugiel, S., Nurnberger, S., Sadeghi, A., Schneider, T.: Twin clouds: an architecture for secure cloud computing. In: Workshop on cryptography and security in clouds (WCSC 2011) (2011)
Cao, N., Wang, C., Li, Ming, Ren, K., Lou, W.: Privacy-preserving multi-keyword ranked search over encrypted cloud data. In: INFOCOM, 2011 Proceedings IEEE, pp. 829–837. IEEE, Piscataway (2011)
Cao, N., Yang, Z., Wang, C., Ren, K., Lou, W.: Privacy-preserving query over encrypted graph-structured data in cloud computing. In: 2011 31st international conference on distributed computing systems (ICDCS), pp. 393–402. IEEE, Piscataway (2011)
Choi, S., Ghinita, G., Lim, H.-S., Bertino, E.: Secure knn query processing in untrusted cloud environments. IEEE Trans. Knowl. Data Eng. 26(11), 2818–2831 (2014)
Delfs, H., Knebl, H., Knebl, H.: Introduction to cryptography, vol. 2. Springer, Berlin (2002)
Elmehdwi, Y., Samanthula, B.K., Jiang, W.: Secure k-nearest neighbor query over encrypted data in outsourced environments. In: 2014 IEEE 30th international conference on data engineering (ICDE) , pp. 664–675. IEEE, Piscataway (2014)
Evfimievski, A., Srikant, R., Agrawal, R., Gehrke, J.: Privacy preserving mining of association rules. Inf. Syst. 29(4), 343–364 (2004)
Huang, J., Peng, M., Wang, H., Cao, J., Gao, W., Zhang, X.: A probabilistic method for emerging topic tracking in microblog stream. World Wide Web 20(2), 325–350 (2017)
Ji, Z., Tao, X., Wang, H.: Outlier detection from large distributed databases. World Wide Web 17(4), 539–568 (2014)
Kabir, Md.E., Wang, H., Bertino, E.: Efficient systematic clustering method for k-anonymization. Acta Informatica 48(1), 51–66 (2011)
Kabir, Md.E., Wang, H., Bertino, E.: A role-involved purpose-based access control model. Inf. Syst. Front. 14(3), 809–822 (2012)
Kamara, S., Papamanthou, C., Roeder, T.: Dynamic searchable symmetric encryption. In: Proceedings of the ACM conference on computer and communications security, p 2012. ACM, New York (2012)
LeCun, Y., Cortes, C., Burges, C.J.C.: Mnist handwritten digit database. AT&T Labs [Online]. Available: http://yann.lecun.com/exdb/mnist, 2 (2010)
Li, M., Sun, X., Wang, H., Zhang, Y., Ji, Z.: Privacy-aware access control with trust management in Web service. World Wide Web 14(4), 407–430 (2011)
Li, H., Ye, W., Wang, H., Zhou, B.: Multi-window based ensemble learning for classification of imbalanced streaming data. World Wide Web, 1–19 (2017)
Li, X., Zhu, Y., Wang, J., Liu, Z., Liu, Y., Zhang, M.: On the soundness and security of privacy-preserving svm for outsourcing data classification. IEEE Trans. Dependable Secure Comput. PP(99), 1–1 (2017)
Liu, K., Giannella, C., Kargupta, H.: An attacker’s view of distance preserving maps for privacy preserving data mining. Knowl. Discov. Data: PKDD 2006, 297–308 (2006)
Mell, P., Grance, T., et al.: The nist definition of cloud computing (2011)
Oliveira, S.R.M., Zaiane, O.R.: Privacy preserving clustering by data transformation. In: Proceedings of the 18th Brazilian symposium on databases, Citeseer, pp. 304–318 (2003)
Peng, M., Zeng, G., Sun, Z., Huang, J., Wang, H., Tian, G.: Personalized app. recommendation based on app. permissions. World Wide Web, 1–16 (2017)
Popa, R.A., Li, F.H., Zeldovich, N.: An ideal-security protocol for order-preserving encoding. In: 2013 IEEE symposium on security and privacy (SP), pp. 463–477. IEEE, Piscataway (2013)
Rahulamathavan, Y., Phan, R.C.-W., Veluru, S., Cumanan, K., Rajarajan, M.: Privacy-preserving multi-class support vector machine for outsourcing the data classification in cloud. IEEE Trans. Dependable Secure Comput. 11(5), 467–479 (2014)
Rong, H., Wang, H.-M., Liu, J., Xian, M.: Privacy-preserving k-nearest neighbor computation in multiple cloud environments. IEEE Access 4, 9589–9603 (2016)
Samanthula, B.K., Elmehdwi, Y., Jiang, W.: K-nearest neighbor classification over semantically secure encrypted relational data. IEEE Trans. Knowl. Data Eng. 27(5), 1261–1273 (2015)
Su, M.-Y., Chang, K.-C., Wei, H.-F., Lin, C.-Y.: Feature weighting and selection for a real-time network intrusion detection system based on ga with knn. In: International Conference on Intelligence and Security Informatics, pp. 195–204. Springer, Berlin (2008)
Sun, W., Wang, B., Cao, N., Li, M., Lou, W., Hou, T.Y., Li, H.: Privacy-preserving multi-keyword text search in the cloud supporting similarity-based ranking. In: Proceedings of the 8th ACM SIGSAC symposium on information, computer and communications security, pp. 71–82. ACM, New York (2013)
Wang, H., Cao, J., Zhang, Y.: A flexible payment scheme and its role-based access control. IEEE Trans. Knowl. Data Eng. 17(3), 425–436 (2005)
Wang, H., Zhang, Y., Cao, J.: Effective collaboration with information sharing in virtual universities. IEEE Trans. Knowl. Data Eng. 21(6), 840–853 (2009)
Wang, C., Cao, N., Ren, K., Lou, W.: Enabling secure and efficient ranked keyword search over outsourced cloud data. IEEE Trans. Parallel Distrib. Syst. 23(8), 1467–1479 (2012)
Wang, B., Liao, Q., Zhang, C.: Weight based knn recommender system. In: 2013 5th international conference on intelligent human-machine systems and cybernetics (IHMSC), vol. 2, pp. 449–452. IEEE, Piscataway (2013)
Wang, H., Zhang, Z., Taleb, T.: Editorial: special issue on security and privacy of IoT. World Wide Web-internet & Web Information Systems (2), 1–6 (2017)
Wong, W.K., Cheung, D.W.-l., Kao, B., Mamoulis, N.: Secure knn computation on encrypted databases. In: Proceedings of the 2009 ACM SIGMOD international conference on management of data, pp. 139–152. ACM, New York (2009)
Xia, Z., Wang, X., Sun, X., Wang, Q.: A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE Trans Parallel Distrib Syst 27 (2), 340–352 (2016)
Xu, H., Guo, S., Chen, K.: Building confidential and efficient query services in the cloud with rasp data perturbation. IEEE Trans. Knowl. Data Eng. 26(2), 322–335 (2014)
Yao, B., Li, F., Xiao, X.: Secure nearest neighbor revisited. In: 2013 IEEE 29th international conference on data engineering (ICDE), pp. 733–744. IEEE, Piscataway (2013)
Yiu, M.L., Assent, I., Jensen, C.S., Kalnis, P.: Outsourced similarity search on metric data assets. IEEE Trans. Knowl. Data Eng. 24(2), 338–352 (2012)
Youwen, Z.H.U., Takagi, T., Rong, H.U.: Security analysis of collusion-resistant nearest neighbor query scheme on encrypted cloud data. IEICE TRANSACTIONS on Information and Systems 97(2), 326–330 (2014)
Yuan, J., Yu, S.: Efficient privacy-preserving biometric identification in cloud computing. In: INFOCOM, 2013 Proceedings IEEE, pp. 2652–2660. IEEE, Piscataway (2013)
Zhou, L., Zhu, Y., Castiglione, A.: Efficient k-NN query over encrypted data in cloud with limited key-disclosure and offline data owner. Comput. Secur. 69, 84–96 (2017)
Zhu, Y., Xu, R., Takagi, T.: Secure k-nn computation on encrypted cloud data without sharing key with query users. In: Proceedings of the 2013 international workshop on security in cloud computing, pp. 55–60. ACM, New York (2013)
Zhu, Y., Rui, X., Takagi, T.: Secure k-nn query on encrypted cloud database without key-sharing. Int. J. Electron. Secur. Digit. Forensics 5(3-4), 201–217 (2013)
Zhu, Y., Huang, Z., Takagi, T.: Secure and controllable k-nn query over encrypted cloud data with key confidentiality. J. Parallel Distrib. Comput. 89, 1–12 (2016)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wu, W., Parampalli, U., Liu, J. et al. Privacy preserving k-nearest neighbor classification over encrypted database in outsourced cloud environments. World Wide Web 22, 101–123 (2019). https://doi.org/10.1007/s11280-018-0539-4
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11280-018-0539-4