Abstract
Cryptosystems are commonly deployed to secure data transmission over an insecure line of communication. To provide confusion in the data over insecure networks, substitution boxes are the solitary components for delivering a nonlinear mapping between inputs and outputs. A confusion component of a block cipher with high nonlinearity and low differential and linear approximation probabilities is considered secure against cryptanalysis. This study aims to design a highly nonlinear substitution-permutation network using the blotch symmetry of quantum spin states on the Galois field GF (28). To observe the efficiency of the proposed methodology, some common and advanced measures were evaluated for performance, randomness, and cryptanalytics. The outcomes of these analyses validate that the generated nonlinear confusion components are effective for block ciphers and attain better cryptographic strength with a high signal-to-noise ratio in comparison to state-of-the-art techniques.
Similar content being viewed by others
Introduction
The rapid growth of multimedia communication necessitated the requirement for safe and contemporaneous transmission and information exchange. A prominent approach to cope with this is to consider a plain bit stream and apply either modern or traditional cryptographic standards, such as the Data Encryption Standard (DES)1,2, Advanced Encryption Standard (AES)3,4, and International Data Encryption Algorithm (IDEA)5,6. Modern block ciphers (DES and AES) depend on Shannon’s theory of confusion and diffusion7. Confusion refers to the practice of generating the relationship between key and ciphertext as complex as possible, whereas, the influence of a single bit on multiple cipher bits to opaque the statistical redundancies of plaintext refers to diffusion.
The substitution box (S-box) is a vectorial Boolean function that maps \(F_{2}^{n}\) to \(F_{2}^{m}\), where \(F_{2}^{n}\) signifies Galois field \(GF\left( {2^{n} } \right)\)8. It is the solitary component in a block cipher to deliver confusion through nonlinear mapping between the inputs and outputs to perceive the practice of encryption. There have been numerous solicitations of S-boxes available in the literature for image encryption9,10,11, low-profile mobile applications12, multimedia encryption13, watermarking, and steganography14.
Linear and differential cryptanalyses are based on the probabilistic characteristics of the cipher parameters and output. These are considered powerful attacks on block ciphers. These attacks signify the strength of the encryption algorithm by increasing the number of rounds in the structure15. The nonlinearity of S-boxes causes uncertainty in the output, which provides resistance against differential and linear attacks16,17. An S-box with high nonlinearity and low linear and differential probabilities is always favorable for a cryptosystem18. Therefore, the design of such components with good cryptographic properties plays a significant role in cryptographic applications19.
Substitution permutation network (SPN) structures are commonly implemented in AES and Feistel types of networks, such as DES20. AES uses bijective components to assemble the system invertible, whereas the DES approach is not limited to bijectivity. For instance, the proposed PICARO method21 uses non-bijective mapping in Feistel networks. However, the nonlinearity using the PICARO method reached 94, which is far from the Rijndael optimal value of 112 in AES.
True random classifications for cryptography; however, have been validated by researchers since techniques rely on the robustness of naturally arising mechanisms to generate true randomness22,23,24,25. These types of sequences are non-reproducible, unpredictable, and irreversible, all the while their internal assembly and response history are understood by adversaries. Quantum spin states, maps, and chaos exhibit the favorable properties of capriciousness, ergodicity, control parameters, and sensitivity to the initial value(s) that fulfill the requirements of confusion and diffusion properties for the cryptosystem(s)26,27.
Problem statement
With the advent of quantum technology, several traditional security standards and cryptographic solicitations may be easily exploited and mistreated28,29,30. However, except for some attacks such as meet-in-middle and side-channel31,32, no better attacks exist other than brute-force to exploit the weakness in key scheduling and inadequate diffusion features in SQUARE33 and AES4, which entail millions of years for decryption. However, quantum classifications have attracted great attention in scientific and engineering disciplines, especially in the design of new cryptosystems and cryptanalyses, which is a threat to AES and Feistel network-based applications by performing reverse computation or executing brute force using quantum computation. As the confusion component is considered an intense constituent for most of the assemblies to resist attacks, many researchers laid their potential to improve existing as well as proposing new structures either with the traditional or by using quantum practices to generate secure S-boxes34,35,36. To resist classical and quantum attacks, there is a need to design a substitution permutation structure with highly nonlinear confusion components and comparable cryptographic properties for classical standards.
Related work
Numerous structures exist to generate the outcomes for S-boxes with either traditional or modern chaos-based algorithms37,38, and many researchers have applied optimization methods, such as evolutionary algorithms39,40,41, to improve the chaos-based consequences for the confusion component. Although these methodologies to design the structures of S-boxes offer favorable characteristics, researchers have also pointed out the weaknesses of these approaches42. Many statistical attacks are available for the assembly of S-box designs, including linear and differential43,44,45, interpolation46, Grobner basis47, side-channel48, SAT solver49, XL50, and XSL51 attacks. Chaos-based systems have been used extensively in the construction of confusion components52,53, but owing to the inherent algorithmic advancement of control parameters and periodicity in the maps, several weaknesses of these systems also exist in the literature, including discontinuity and non-uniform distribution in chaotic sequences54,55, predictability56,57, finite precision effect and short quantity of randomness58,59, dynamical degradation of chaotic systems and frail chaos60,61, and a small number of control parameters62,63.
The authors in64 generated the outcomes by transforming the binary Gray code into a standard AES S-box. Likewise, the authors in65 offered two boxes for AES, and the authors in66 minimized the computational complexity of AES by modifying the affine transformation matrices. A few recent studies for designing dynamic S-boxes using cellular automata (CA) are highlighted in67,68,69 with comparable cryptographic properties. However, these practices do not provide substantial attributes because of the insignificant differential probability values70.
Among the computational prototypes established in the quantum era, quantum walks71,72, quantum spin states73,74, and quantum chaos75,76 have been employed to develop modern algorithms. The generated confusion components using these procedures still need improvements to compete with standard algorithms, such as AES, in the sense of nonlinearity and balancedness. Although, the physical hardware for quantum computing is not yet available, the inspired frameworks provide platforms for emulating pseudo-quantum algorithms, which can perform various quantum mechanical solicitations endorsed by the influence of quantum computations within the constraints executed by the capability of classical machines77.
Contribution
Inspired by the tremendous nonlinear features of quantum algorithms, the constraints of classical cryptosystems can be enhanced by designing state-of-the-art projections for effective applications in information security78,79,80,81. The main contribution of this research is to explore the assimilation of quantum-inspired algorithms into conventional cryptographic applications. To accentuate the highly nonlinear balanced S-boxes (8, 8) described by the property of having an exceptionally high resistance to linear and differential cryptanalysis, we developed a bit-level quantum dot protocol on the blotch symmetry of quantum spin states to generate the true random sequence. We also designed and used a white-box to map multiple bits within a single state into a singular bit to balance the output of each state. It also resists the reverse engineering process to cope with brute-force attacks performed either in classical or quantum machines.
The confrontation of linear and differential cryptanalysis for the evaluated nonlinear components is superior to some common boxes used in AES, APA82, Gray64, PICARO21, NSA’s Skipjack83, and state-of-the-art block ciphers. The maximum nonlinearity achieved using the Rijndael structure for AES is 112 and 94 in PICARO, whereas our method generates S-boxes with a nonlinearity of 114.
To estimate the efficiency of the projected model, we compared the numerical evaluation of confusion components with well-established criteria of some state-of-the-art mechanisms, such as nonlinearity, balancedness and bijectivity, linear and differential approximation probabilities (LP and DP), strict avalanche and bit independence criteria (SAC and BIC), NIST statistical suite, and cryptanalytic analyses. The results of the proposed methodology validate that the generated S-boxes are feasible for multifaceted solicitations in information security.
Methodology
Collection of Boolean functions \(F\left( {X_{n} } \right) = \left( {f_{1} \left( {X_{n} } \right),...,f_{m} \left( {X_{n} } \right)} \right)\) through mapping of \(F:{\mathbb{F}}_{2}^{n} \,a\,{\mathbb{F}}_{2}^{m}\) over the Galois field \(GF\left( {p^{m} } \right)\)84 to generate confusion component using the blotch symmetry of quantum states is evaluated in this section. The details of Boolean Functions, Galois Field, and the Substitution box are provided in the supplementary information underneath the heading preliminaries. This section provides a brief overview of the mechanism used to construct the confusion components, such as the evaluation of quantum dots from states, the development of balanced Boolean function values, the pseudo algorithm, and the structural flowchart.
Evaluation of Quantum dots
The unitary group of degree \(n\) ‘\(SU(n)\)’ is defined as a set of \(n \times n\) special matrices with entries from complex numbers having determinant one. It can be signified as:
where \(z_{1} ,z_{2} \in C\), and \(\,\left| {z_{1} } \right|^{2} + \left| {z_{2} } \right|^{2} = 1\).
The eigenvalue of the physical observable spin system \(S_{z}\) involves the relationship of \(\pm \hbar /2\), kets \(\left| {\left. \pm \right\rangle } \right.\), and the operators in a system of spin \({\raise0.5ex\hbox{$\scriptstyle 1$} \kern-0.1em/\kern-0.15em \lower0.25ex\hbox{$\scriptstyle 2$}}\) are \(S_{z} \left| {\left. + \right\rangle } \right. = + \frac{\hbar }{2}\left| {\left. + \right\rangle } \right.\) and \(S_{z} \left| {\left. - \right\rangle } \right. = - \frac{\hbar }{2}\left| {\left. - \right\rangle } \right.\).
We consider \(S_{z}\) as the most general form of the \(2 \times 2\) matrix as:
Therefore, the spin \({\raise0.5ex\hbox{$\scriptstyle 1$} \kern-0.1em/\kern-0.15em \lower0.25ex\hbox{$\scriptstyle 2$}}\) system can be engraved as: \(\left( {\begin{array}{*{20}c} p & q \\ r & s \\ \end{array} } \right)\left( {\begin{array}{*{20}c} 1 \\ 0 \\ \end{array} } \right) = + \frac{\hbar }{2}\left( {\begin{array}{*{20}c} 1 \\ 0 \\ \end{array} } \right)\), and \(\left( {\begin{array}{*{20}c} p & q \\ r & s \\ \end{array} } \right)\left( {\begin{array}{*{20}c} 0 \\ 1 \\ \end{array} } \right) = - \frac{\hbar }{2}\left( {\begin{array}{*{20}c} 0 \\ 1 \\ \end{array} } \right)\)
The generated solutions to the above equivalences are: \(p = + \frac{\hbar }{2}\,\,\,,\,\,\,q = 0,\,\,\,r = 0,\,\,{\text{and}}\,\,s = - \frac{\hbar }{2}.\)
The corresponding outcomes for the above solution are: \(S_{z} = \frac{\hbar }{2}\left( {\begin{array}{*{20}c} 1 & 0 \\ 0 & { - 1} \\ \end{array} } \right)\,\,\,\,\,\left| {\left. + \right\rangle } \right. = \left( {\begin{array}{*{20}c} 1 \\ 0 \\ \end{array} } \right)\,\,\,\,\,\left| {\left. - \right\rangle } \right. = \left( {\begin{array}{*{20}c} 0 \\ 1 \\ \end{array} } \right)\).
Therefore, the spin operators in the \(x,\,\,y\) and \(z\) directions with eigenvalues of \(\pm \,\hbar /2\) are evaluated as.
\(S_{x} = \frac{\hbar }{2}\left( {\begin{array}{*{20}c} 0 & 1 \\ 1 & 0 \\ \end{array} } \right)\,\,\,\,\,\,\left. {\left| + \right.} \right\rangle_{x} = \frac{1}{\sqrt 2 }\left( {\begin{array}{*{20}c} 1 \\ 1 \\ \end{array} } \right)\,\,\,\,\,\,\left. {\left| - \right.} \right\rangle_{x} = \frac{1}{\sqrt 2 }\left( {\begin{array}{*{20}c} 1 \\ { - 1} \\ \end{array} } \right)\),
\(S_{y} = \frac{\hbar }{2}\left( {\begin{array}{*{20}c} 0 & { - i} \\ i & 0 \\ \end{array} } \right)\,\,\,\,\,\,\left. {\left| + \right.} \right\rangle_{y} = \frac{1}{\sqrt 2 }\left( {\begin{array}{*{20}c} 1 \\ i \\ \end{array} } \right)\,\,\,\,\,\,\left. {\left| - \right.} \right\rangle_{y} = \frac{1}{\sqrt 2 }\left( {\begin{array}{*{20}c} 1 \\ { - i} \\ \end{array} } \right)\), and.
\(S_{z} = \frac{\hbar }{2}\left( {\begin{array}{*{20}c} 1 & 0 \\ 0 & { - 1} \\ \end{array} } \right)\,\,\,\,\,\,\left| {\left. + \right\rangle_{z} } \right. = \frac{1}{\sqrt 2 }\left( {\begin{array}{*{20}c} 1 \\ 0 \\ \end{array} } \right)\,\,\,\,\,\,\left| {\left. - \right\rangle_{z} } \right. = \frac{1}{\sqrt 2 }\left( {\begin{array}{*{20}c} 0 \\ 1 \\ \end{array} } \right)\).
The constituent of the spin system in a direction along the unit vector \(\hat{n}\) is \({\hat{\mathbf{n}}} = {\hat{\mathbf{i}}}\sin \theta \cos \phi + {\hat{\mathbf{j}}}\sin \theta \sin \phi + {\hat{\mathbf{k}}}\cos \theta\).
Therefore, the spin vector \({\mathbf{S}}\) can be transformed into a new unit vector \(S_{n} = {\mathbf{S}} \cdot {\hat{\mathbf{n}}}\), hence,
\(S_{n} = S_{x} \sin \theta \cos \phi + S_{y} \sin \theta \sin \phi + S_{z} \cos \theta\), or more generally, \(S_{n} = \frac{\hbar }{2}\left( {\begin{array}{*{20}c} {\cos \theta } & {\sin \theta e^{ - i\phi } } \\ {\sin \theta e^{ - i\phi } } & { - \cos \theta } \\ \end{array} } \right)\), and the eigenvectors are \(\left. {\left| + \right.} \right\rangle_{n} = \cos \frac{\theta }{2}\left. {\left| + \right.} \right\rangle + \sin \frac{\theta }{2}e^{i\phi } \left. {\left| - \right.} \right\rangle\) and \(\left. {\left| - \right.} \right\rangle_{n} = \sin \frac{\theta }{2}\left. {\left| + \right.} \right\rangle - \cos \frac{\theta }{2}e^{i\phi } \left. {\left| - \right.} \right\rangle\).
Let us entangle the produced \(2 \times 2\) matrices from \(S_{n}\) in the \(x,\,\,y\) and \(z\) directions by introducing the identity matrix to generate a set \(S\) of \(4 \times 4\) entangled matrices, that is, \(S = \{ S_{k} \in S_{4 \times 4} \,(I,S_{x} ,S_{y} ,S_{z} \,),\,\,k = 1,2,...,24\,.\}\). The points at which the entangled states reflect their symmetry are referred to as quantum dots85, as shown in Fig. 1.
Evaluation of quantum dots at the entangled point of spin states. (a) Extraction of dot points at the 8th entangled state in the phase domain of 0 to 360 with a step size of 90, (b) Extraction of dot points at the 14th entangled state in the phase domain of 0 to 360 with a step size of 90, (c) Extraction of dot points at the 1st entangled state in the phase domain of − 90 to 90 with a step size of 20.
Generation of balanced Boolean function values
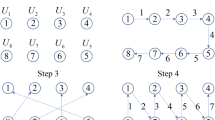
The generation of four bits in each state in Fig. 2 is mapped to a single bit using white-box (WB) with multiple operations that map \({\mathbb{F}}_{2}^{4}\) to \({\mathbb{F}}_{2}\), as demonstrated in Fig. 3, to evaluate the binary sequence(s) to generate S-boxes. The total number of functions in the white-box that correspond to input bits will be \(2^{{2^{n} }}\), implying that there will be 256 Boolean functions in the white-box for four input values.
If the produced 8-bit sequence is similar to the previous state(s) sequence or unable to satisfy the balance criterion, the produced sequence from the same states will again operate with the WB until the condition is fulfilled. The random assortment of each operation in the WB to produce a single bit also resists the reverse engineering threats to cryptographic structures.
Algorithm
The detailed algorithm to design highly nonlinear confusion component(s) is explained as follows:
-
To initialize the setup, we first set the phase domain between − 720° and 720° with a sufficient step size \(i\). A larger phase domain with a smaller step size leads to unbounded or measureless states generation.
-
Each state contains multiple points to produce binary data, where the points in each state(s) will be at different positions and have distinct classifications among other states to produce truly random data.
-
The algorithm of Table 1 takes statistics from the first eight states and produces an 8-bit sequence using the WB. There will be a mapping of multiple points within a state to generate a single bit using WB.
-
For 256 operations with multiple of eight states, the statistics are fetched from 2048 states. If any of the 8-bit outputs using WB are similar to any previous record, the operation will be repeated in the same states until a unique sequence is generated.
-
The algorithm then substantiates the balancedness property of the unique sequence. It repeats the same constraints if the condition is not fulfilled.
-
It generates the S-box after validating the desired nonlinearity, SAC, and linear and differential probability approximations. It will take a designated phase shift in the input domain and perform all the operations again if any of the trials are not satisfied.
Structural flowchart
The protuberant structure used to construct the highly nonlinear balanced S-boxes for block ciphers is shown in Fig. 4. There is no prerequisite of Add-Round-Key to alter or modify the keys or phase information for different rounds in a block cipher. If there is a small phase domain to design the states for quantum dots, then after producing sufficient outcomes for the S-boxes, the states are shifted to 45° and dots are generated at different positions in each state and perform the desired operations.
S-box conditions: If there is a dispute between bits’ repetition(s) or the balancedness is not satisfied, the algorithm repeats itself on the same constraints. It will not move to the next state unless the conditions are fulfilled. The S-box is assembled after scrutinizing the conditions of the desired nonlinearity and strict avalanche quality criteria.
Experimental results
The generated substitution boxes are listed in Tables 2 and 3 after satisfying certain criteria, such as the 0/1 balance test, bits alteration to reach the nearby affine function, sensitivity of avalanche deviations by a single variation in the network's input, minute alteration in the input sequence to observe the variation in the output, and determination of the maximum disparity of the event's outcome by witnessing the imbalance between the input and output bits86. The supplementary information contains a comprehensive description of these analyses underneath the evaluation criteria for s-boxes. The outcomes based on the proposed methodology, as well as their assessments with standard structures and state-of-the-art implications, are discussed in the following subsections.
Generated S-boxes
We evaluated multiple balanced Boolean functions, and the outcomes of the two nonlinear components for block ciphers are demonstrated in Tables 2 and 3.
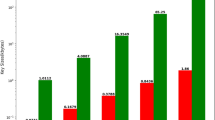
The S-boxes represent a distinct group of \(n\) variable Boolean functions. Therefore, we carried out the following measures to assess the performance of the intended nonlinear components. We validated the randomness in the bit stream generated with blotch symmetry of entangled states over the 2-D plane using the NIST statistical test suite (800-22)87. This suite entails multiple assessments, provided in the supplementary information, to investigate the security of the anticipated design. We conducted cryptanalytic analysis, including algebraic degree, absolute indicator, algebraic immunity, correlation immunity, propagation criteria to ensure the diffusion characteristics in Boolean functions, differential uniformity, differential cryptanalysis, differential power analysis in terms of signal-to-noise ratio, and transparency order to quantify the resistance of the s-boxes against differential attacks.
Nonlinearity comparison
Linear mapping of input vectors to the output renders the cryptosystem breakable. A higher nonlinearity of the confusion component is always desirable to make the cryptosystem strong enough to provide resistance against linear and differential attacks. The nonlinearity of all Boolean function constituents for the evaluated S-boxes S1 and S2 and their comparison with various methodologies are given in Table 4.
The maximum non-linearity for 8-bit balanced Boolean functions achievable with standard AES, APA, or Gray S-box is 112. The confusion components, either with this nonlinearity or nearby, are generally considered to be secure. We reached nonlinearity of 114 for 8-bit balanced Boolean functions with the proposed methodology, which validates superior capacity to state-of-the-art findings in resisting attacks.
SAC and BIC comparison
A cryptographic hash function or block cipher must launch the avalanche effect to a substantial degree for reliable randomization to protect the algorithm from the cryptanalyst breaking partially or entirely by predicting the input at a given output. It is satisfied when each of the output bits flips with a 50% probability by complimenting a single input bit. The pairwise independence between avalanche variables for a specified set of avalanche vectors is evaluated here with the BIC assessment given in Table 5.
By analyzing the outcomes reported in Table 5, the proposed approach produces better outcomes than state-of-the-art attainments. The maximum BIC-NL value obtained in existing methods is 112, however we reached 114 in our trial. The findings of the aforementioned method also satisfy the SAC analysis, yielding a near-optimal value of 0.5.
NIST statistical analyses
To investigate the security of the proposed design, we executed the NIST statistical test suite (800-22) on the generated random sequence by quantum dots for S-boxes. The outcomes of this trial are presented in Table 6.
Based on the findings in Table 6, we discovered that the produced sequence for mono-bits and block frequency assessments meet the intimacy of the ones fraction to about one-half, which exhibited that the number of ones and zeros in a sequence and in m-bit block(s) are approximately the same. To observe the fluctuations between the substrings, run and longest run assessments were performed, whilst the rank of disjoint sub-matrices for the entire sequence is assessed to determine the linear dependency. We evaluated the FFT to detect periodic features in the sequence to identify the divergence from the notion of randomness. Runs of zeros were not analyzed individually for periodic and a-periodic assessments because of concerns about statistical impartiality. Using a feedback register, we conducted a universal statistical test and a linear-complexity test to determine the number of bits between matching patterns and the complexity of the sequence. We also observed the frequency of each overlapping pattern in the sequence using a serial test and used approximate entropy assessment to relate the frequency of overlapping blocks to the expected outcomes for the random sequence. We evaluated the cumulative sum to determine the maximum excursion of the random walk and validated the randomness in sequence based on the findings shown in Table 6.
Balancedness, Bijectivity, LP, and DP comparison
A function with significant disparity can easily be approximated by a constant function, and an S-box is considered balanced if all of its Boolean function constituents are balanced. To analyze the imbalance between the input and output bits and determine the maximum disparity estimation of the event’s outcome, we evaluated its linear probability. The S-boxes are considered secure against linear cryptanalysis if they have a small linear probability. For the variation in output for a minute alteration in the input sequence, we computed the differential probability. The immunity of the S-box to differential cryptanalysis is better if the maximum value of DP is as small as possible. Table 7 comprises analyses of balancedness, bijectivity, number of fixed points, LP, and DP for the assessed S-boxes using the proposed methodology, as well as comparisons with AES, APA, Gray, and state-of-the-art practices.
All Boolean functions involved in the structure of the anticipated methodology to generate the confusion components satisfy the balance criteria, that is, \(W_{f} \left( 0 \right) = 0\). The XOR operation among Boolean functions satisfies the bijection property. The proposed algorithm generates nonlinear components that meet the highest possible valuation for DP of 4/256. Furthermore, the evaluated LP values of the intended and AES, APA, and Gray boxes are equivalent or superior to the state-of-the-art schemes shown in Table 7.
Cryptanalytic analyses comparison
We executed numerous cryptanalytic analyses to measure the resistivity against diverse attacks. The reasoning for these findings are discussed in the supplementary data. Table 8 summarizes the findings of each investigation and their comparison with the available approaches.
By investigating the outcomes in Table 8, the propagation criteria fulfill the assurity of diffusion properties in Boolean functions. The algebraic degree is sufficiently high to resist cryptanalytic attacks and is comparable with state-of-the-art results. Using the consequences of Tables 2, 3, we executed correlation attacks and found perfect correlation immunity. In our proposed model, the largest \(\delta\) uniformity value is as low as in AES and APA structures, and the estimation of differential cryptanalytics for the assessed S-boxes is close to one. The estimated SNR and transparency order for the generated boxes were sufficiently high to provide resistivity against DPA attacks.
Discussion
We demonstrated the integration of quantum states with the classical system for real-time environments by witnessing a point on which the quantum state reflects its symmetry, referred to as a quantum dot, rather than observing a superposition state on quantum machine into a definite state on classical system. We employ a conventional white-box, which has no impact on the quantumness features, to balance the functions. The produced sequence using proposed method for mono-bits and block frequency satisfies the intimacy of the ones fraction to almost one-half while ensuring the diffusion features in Boolean functions.
A multivalued cryptographic Boolean function employing a recurrent neural network was recently developed91. The network generates balanced confusion components with low linear and differential probability and a nonlinearity of 112. They train the net using rigorous limitations of activation function and the initialization of Mackey–Glass time series on the specified parameters, such as the time series' behavior becomes chaotic if τ grows from 17. In the experiment, 3000 learning samples over a specified period were analyzed to balance the parameters by mapping the intermission to itself. Each cycle yields a unique byte, resulting in 256 value vectors. If the generated S-box is not balanced, the system will repeat itself with new learning samples. Their method is ineffective for real-time applications due to space and execution constraints. Furthermore, they did not fulfill the avalanche and NIST criteria and did not undertake cryptanalytic investigations to validate the algorithm's efficacy against specific attacks, rendering it vulnerable to certain threats.
Similarly, with recent advances in quantum computations, the author proposed quantum spinning operators to develop confusion components74 with properties similar to traditional benchmarks, such as nonlinearity, BIC, SAC, and several others. Although the author employed quantum attributes to initiate the true random sequence, and the statistics are favorable, the approach is based on a random walk with Brownian motion. To overcome the challenge of superposition states into definite, as shown in Fig. 1d, e, the author launched a random walk with states on a classical system. The method focuses on random walk rather than true randomization characteristics to balance the confusion component of block cipher.
These methodologies produce better outcomes for confusion components, however, their integration with traditional systems in real-time environments is impractical because of the initial execution period and computational complexities. The developed model is simple and produces true random sequences, overcomes the aforementioned challenges, and produces superior outcomes than existing frameworks. It also has a higher resistance to hostile cryptographic attacks. The functions assessed in Tables 2, 3 are substantially compact without information loss and complex enough to be considered random. We observed from Tables 4, 5, 6, 7 that these functions maintain high resistivity in terms of linear cryptanalysis by:
-
Maintaining the magnitude of the function's discrepancy lower and satisfying the 0/1 balance test,
-
Satisfying the pairwise independence of the avalanche variables for a given set of avalanche vectors by complimenting a single plain bit, and
-
Providing the least possible Hamming distance to the reference function from the set of all variable affine functions.
These functions validate the resistivity against differential and side-channel attacks while maintaining the diffusion characteristics. By witnessing the results in Table 8, the evaluated functions provide:
-
Differential uniformity with small DP and \(\delta\) value,
-
Sufficiently high signal-to-noise ratio, and
-
Immunity to correlation and algebraic attacks.
In comparison to recent neural network architectures and available quantum-assisted classical computation schemes for SPN network design, the proposed framework is easy to develop and deploy with favorable cryptographic characteristics, and has a high potential to resist statistical and differential attacks.
Conclusion and future works
The security strength of block ciphers greatly relies on the confusion components to resist differential and linear attacks, and the threat of cryptanalysis using quantum classification by performing the reverse computation or executing brute force is one of the core issues of this decade. The produced design provides insights into quantum dots evolved from spin states to generate a truly random sequence for the confusion components, with high nonlinearity and low linear and differential probabilities, to overcome the quantum threats to block ciphers. To evaluate the efficiency of the proposed methodology, we compared the consequences of the intended S-boxes, based on widely accepted cryptographic and cryptanalytic measures, with benchmarks and state-of-the-art outcomes. The exhaustive contrast of these analyses showed that the algorithm is free of algebraic weakness with outstanding performance and provides robustness against linear and differential attacks.
We strongly believe that there is room for further improvements to envisioned structures with even better cryptographic properties. This model is designed for classical machines and can be used to modify the AES structure. The notions of the developed structure can be extended into a qubit model to protect the block ciphers against quantum computation threats. Reckonings of quantum dots in Bloch symmetry are possible when classical bits can be mapped into a qubit or in the form of quantum state(s).
Data availability
Correspondence and requests for materials should be addressed to H.M. Waseem or S.O. Hwang.
References
Zhang, L. Y. et al. On the security of a class of diffusion mechanisms for image encryption. IEEE Trans. Cybern. 48(4), 1163–1175 (2017).
W. C. Barker and E. B. Barker, NIST Special Publication 800-67 Revision 1: Recommendation for the Triple Data Encryption Algorithm (TDEA) Block Cipher, (NIST, 2012).
Advanced Encryption Standard (AES) (Federal Inf. Process, 2001).
Daemen, J. & Rijmen, V. The Design of Rijndael: AES—The Advanced Encryption Standard, Heidelberg (Springer, 2002).
Lai, X. & Massey, J. L. A proposal for a new block encryption standard. in Proc. Workshop Theory Appl. Cryptograph. Techn. 389–404 (1990).
Fips Publication 46–3: Data Encryption Standard (DES) (NIST, 1999).
Shannon, C. E. Communication theory of secrecy systems. Bell Syst. Tech. J. 28(4), 656–715 (1949).
Zhang, T., Chen, C. L. P., Chen, L., Xu, X. & Hu, B. Design of highly nonlinear substitution boxes based on I-Ching operators. IEEE Trans. Cybern. 48(12), 3349–3358 (2018).
Zhou, Y., Panetta, K., Agaian, S. & Chen, C. L. P. (n, k, p)-Gray code for image systems. IEEE Trans. Cybern. 43(2), 515–529 (2013).
Khan, M. & Asghar, Z. A novel construction of substitution box for image encryption applications with Gingerbreadman chaotic map and S8 permutation. Neural Comput. Appl. 29(4), 993–999 (2018).
He, Y., Ying-Qian, Z., Xin, H. & Xing-Yuan, W. A new image encryption algorithm based on the OF-LSTMS and chaotic sequences. Sci. Rep. 11(1), 1–22 (2021).
Abd El-Latif, A. A. et al. Secure data encryption based on quantum walks for 5G Internet of Things scenario. IEEE Trans. Netw. Serv. Manag. 17(1), 118–131 (2020).
Asgari-Chenaghlu, M. et al. Cy: Chaotic yolo for user intended image encryption and sharing in social media. Inf. Sci. 542, 212–227 (2021).
Abd El-Latif, A. A., Abd-El-Atty, B. & Venegas-Andraca, S. E. A novel image steganography technique based on quantum substitution boxes. Opt. Laser Technol. 116, 92–102 (2019).
Cho, J. Y. Linear cryptanalysis of reduced-round Present. In Cryptographers’ Track at the RSA Conference. (Springer, Berlin, Heidelberg, 2010).
Heys, H. M. A tutorial on linear and differential cryptanalysis. Cryptologia 26(3), 189–221 (2002).
Yu, F., Xinhui, G., Hanpeng, L. & Shihong, W. Differential cryptanalysis of image cipher using block-based scrambling and image filtering. Inf. Sci. 554, 145–156 (2021).
Siddiqui, N. et al. A highly nonlinear substitution-box (S-box) design using action of modular group on a projective line over a finite field. PLoS One 15(11), e0241890. https://doi.org/10.1371/journal.pone.0241890 (2020).
Xing, C. & Wang, K. Website information retrieval of web database based on symmetric encryption algorithm. J. Amb. Intell. Human. Comput. https://doi.org/10.1007/s12652-020-02819-w (2021).
Zhang, W. & Pasalic, E. Highly nonlinear balanced S-Boxes with good differential properties. IEEE Trans. Inf. Theory 60(12), 7970–7979 (2014).
Piret, G., Roche, T. & Carlet, C. PICARO—a block cipher allowing efficient higher-order side-channel resistance. Appl. Cryptogr. Netw. Secur. 7341, 311–328 (2012).
Bernardo-Gavito, R. et al. Extracting random numbers from quantum tunnelling through a single diode. Sci. Rep. 7(1), 1–6 (2017).
Ray, B. & Milenković, A. True random number generation using read noise of flash memory cells. IEEE Trans. Electron. Devices 65(3), 963–969 (2018).
Pironio, S. et al. Random numbers certified by Bell’s theorem. Nature 464(7291), 1021–1024 (2010).
Li, D., Yu-Guang, Y., Jing-Lin, B., Jia-Bin, Y. & Juan, X. Controlled alternate quantum walks based quantum hash function. Sci. Rep. 8(1), 1–7 (2018).
Abd, A. A., El-Latif, B.A.-E.-A., Amin, M. & Iliyasu, A. M. Quantum-inspired cascaded discrete-time quantum walks with induced chaotic dynamics and cryptographic applications. Sci. Rep. https://doi.org/10.1038/s41598-020-58636-w (2020).
Alghafis, A. et al. A novel digital contents privacy scheme based on quantum harmonic oscillator and schrodinger paradox. Wirel. Netw. https://doi.org/10.1007/s11276-020-02363-7 (2020).
Arute, F. et al. Quantum supremacy using a programmable superconducting processor. Nature 574(7779), 505–510 (2019).
Alghafis, A., Waseem, H. M., Khan, M. & Jamal, S. S. A hybrid cryptosystem for digital contents confidentiality based on rotation of quantum spin states. Physica A 554, 123908 (2020).
El-Latif, A., Ahmed, A., Bassem, A. E. A., Salvador, E. V. A. & Wojciech, M. Efficient quantum-based security protocols for information sharing and data protection in 5G networks. Future Generat. Comput. Syst. 100, 893–906 (2019).
Guo, S. et al. Exploiting the incomplete diffusion feature: a specialized analytical side-channel attack against the AES and its application to microcontroller implementations. IEEE Trans. Inf. Forensics Secur. 9, 999–1014 (2014).
Hu, W. H. & Junnian, W. Cross subkey side channel analysis based on small samples. Sci. Rep. 12(1), 1–11 (2022).
Nakahara Jr, J. , Barreto, P. S., Preneel, B., Vandewalle, J. & Kim, H. Y. SQUARE Attacks on Reduced-Round PES and IDEA Block Ciphers. In IACR Cryptol. ePrint Arch., 68 (2001).
Wang, Y. et al. A genetic algorithm for constructing bijective substitution boxes with high nonlinearity. Inf. Sci. 523, 152–166 (2020).
Wang, X., Nana, G., Hongyu, Z., Siwei, W. & Yingqian, Z. A new image encryption scheme based on coupling map lattices with mixed multi-chaos. Sci. Rep. 10(1), 1–15 (2020).
Hussain, I., Shah, T., Mahmood, H. & Gondal, M. A. A projective general linear group based algorithm for the construction of substitution box for block ciphers. Neural Comput. Appl. 22(6), 1085–1093 (2013).
Zhou, Y., Hua, Z., Pun, C. & Philip Chen, C. L. Cascade chaotic system with applications. IEEE Trans. Cybern. 45(9), 2001–2012 (2015).
Behera, P. K. & Gangopadhyay, S. Evolving bijective S-Boxes using hybrid adaptive genetic algorithm with optimal cryptographic properties. J. Amb. Intell. Human. Comput. https://doi.org/10.1007/s12652-021-03392-6 (2021).
Bolufé-Röhler, A. & Dania, T. V. Machine learning based metaheuristic hybrids for S-box optimization. J. Ambient. Intell. Humaniz. Comput. 11(11), 5139–5152 (2020).
Li, Y.-L. et al. Differential evolution with an evolution path: a DEEP evolutionary algorithm. IEEE Trans. Cybern. 45(9), 1798–1810 (2015).
Shen, M., Chen, W.-N., Zhang, J., Chung, H.S.-H. & Kaynak, O. Optimal selection of parameters for nonuniform embedding of chaotic time series using ant colony optimization. IEEE Trans. Cybern. 43(2), 790–802 (2013).
Khan, M. F., Saleem, K., Alshara, M. A. & Bashir, S. Multilevel information fusion for cryptographic substitution box construction based on inevitable random noise in medical imaging. Sci. Rep. https://doi.org/10.1038/s41598-021-93344-z (2021).
Selçuk, A. A. On probability of success in linear and differential cryptanalysis. J. Cryptol. 21(1), 131–147 (2008).
Hermelin, M. & Nyberg, K. Linear cryptanalysis using multiple linear approximations. In Advanced Linear Cryptanalysis of Block and Stream Ciphers 29–53. (IOS Press, 2011).
Chen, J., Chen, L. & Zhou, Y. Universal chosen-ciphertext attack for a family of image encryption schemes. IEEE Trans. Multimedia 23, 2372–2385 (2021).
Li, C. & Preneel, B. Improved interpolation attacks on cryptographic primitives of low algebraic degree. In Selected Areas in Cryptography – SAC 2019: 26th International Conference, Waterloo, ON, Canada, August 12–16, 2019, Revised Selected Papers (eds Paterson, K. G. & Stebila, D.) 171–193 (Springer International Publishing, Cham, 2020). https://doi.org/10.1007/978-3-030-38471-5_8.
Zhao, K., Cui, J. & Xie, Z. Algebraic cryptanalysis scheme of AES-256 using Gröbner basis. J. Electr. Comput. Eng. 2017, 1–9. https://doi.org/10.1155/2017/9828967 (2017).
Carlet, C., Faugere, J. C., Goyet, C. & Renault, G. Analysis of the algebraic side channel attack. J. Cryptogr. Eng. 2(1), 45–62 (2012).
Semenov, A., Zaikin, O., Otpuschennikov, I., Kochemazov, S. & Ignatiev, A. On cryptographic attacks using backdoors for SAT. Proc. AAAI Conf. Artif. Intell. https://doi.org/10.1609/aaai.v32i1.12205 (2018).
Sugita, M., Mitsuru, K. & Hideki, I. Relation between the XL algorithm and Grobner basis algorithms. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 89(1), 11–18 (2006).
Wentan, Y. I., Linzhen, L. U. & Chen, S. Integral and zero-correlation linear cryptanalysis of lightweight block cipher MIB. J. Electron. Inform. Technol. 38(4), 819–826 (2016).
Zhang, Y. The unified image encryption algorithm based on chaos and cubic S-Box. Inf. Sci. 450, 361–377 (2018).
Hua, Z. & Yicong, Z. Image encryption using 2D logistic-adjusted-sine map. Inf. Sci. 339, 237–253 (2016).
Li, C., Feng, B., Li, S., Kurths, J. & Chen, G. Dynamic analysis of digital chaotic maps via state-mapping networks. IEEE Trans. Circuits Syst. I Regul. Pap. 66(6), 2322–2335 (2019).
Khan, M. F., Ahmed, A. & Saleem, K. A novel cryptographic substitution box design using Gaussian distribution. IEEE Access 7, 15999–16007 (2019).
Hua, Z. & Zhou, Y. Dynamic parameter-control chaotic system. IEEE Trans. Cybern. 46(12), 3330–3341 (2016).
Preishuber, M., Hütter, T., Katzenbeisser, S. & Uhl, A. Depreciating motivation and empirical security analysis of chaos-based image and video encryption. IEEE Trans. Inf. Forensics Secur. 13(9), 2137–2150 (2018).
Deng, Y., Hanping, H., Naixue, X., Wei, X. & Lingfeng, L. A general hybrid model for chaos robust synchronization and degradation reduction. Inf. Sci. 305, 146–164 (2015).
Wu, X., Dawei, W., Jürgen, K. & Haibin, K. A novel lossless color image encryption scheme using 2D DWT and 6D hyperchaotic system. Inf. Sci. 349, 137–153 (2016).
Hua, Z., Zhou, B. & Zhou, Y. Sine Chaotification model for enhancing chaos and its hardware implementation. IEEE Trans. Industr. Electron. 66(2), 1273–1284 (2019).
Hua, Z., Jin, Fan, Binxuan, Xu. & Huang, H. 2D logistic-sine-coupling map for image encryption. Signal Process. 149, 148–161. https://doi.org/10.1016/j.sigpro.2018.03.010 (2018).
Alawida, M., Azman, S., Je, S. T. & Rami, S. A. A new hybrid digital chaotic system with applications in image encryption. Signal Process. 160, 45–58 (2019).
Cao, C., Kehui, S. & Wenhao, L. A novel bit-level image encryption algorithm based on 2D-LICM hyperchaotic map. Signal Process. 143, 122–133 (2018).
Tran, M. T., Bui, D. K. & Duong, A. D. Gray S-Box for Advanced Encryption Standard. In 2008 International Conference on Computational Intelligence and Security 253–258, (2008).
Tiwari, N. & Kumar, A. Security effect on AES in terms of avalanche effect by using alternate S-box. In International Conference on Intelligent Data Communication Technologies and Internet of Things (ICICI) 2018 (eds Hemanth, J. et al.) 1–14 (Springer International Publishing, 2019). https://doi.org/10.1007/978-3-030-03146-6_1.
Sahoo, O. B., Kole, D. K. & Rahaman, H. An optimized S-box for advanced encryption standard (AES) design. In International Conference on Advances in Computing and Communications 154–157 (IEEE, 2012).
Dong, Y., Geng, Z., Yingjie, M., Zhou, P. & Rui, W. A novel image encryption scheme based on pseudo-random coupled map lattices with hybrid elementary cellular automata. Inf. Sci. 593, 121–154 (2022).
Ibrahim, S. & Abbas, A. M. Efficient key-dependent dynamic S-boxes based on permutated elliptic curves. Inf. Sci. 558, 246–264 (2021).
Mahmood Malik, M. S. et al. Generation of highly nonlinear and dynamic AES substitution-boxes (S-Boxes) using chaos-based rotational matrices. IEEE Access 8, 35682–35695 (2020).
Siddiqui, N., Khalid, H., Murtaza, F., Ehatisham-Ul-Haq, M. & Azam, M. A. A novel algebraic technique for design of computational substitution-boxes using action of matrices on Galois field. IEEE Access 8, 197630–197643 (2020).
Yang, Y. G., Qing-Xiang, P., Si-Jia, S. & Peng, X. Novel image encryption based on quantum walks. Sci. Rep. 5(1), 1–9 (2015).
Yang, Y. G. & Qian-Qian, Z. Novel pseudo-random number generator based on quantum random walks. Sci. Rep. 6(1), 1–11 (2016).
Waseem, H. M., Alghafis, A. & Khan, M. An efficient public key cryptosystem based on dihedral group and quantum spin states. IEEE Access 8, 71821–71832 (2020).
Alghafis, A. Quantum half and full spinning operator-based nonlinear confusion component. IEEE Access 9, 31256–31267 (2021).
Boixo, S. et al. Characterizing quantum supremacy in near-term devices. Nat. Phys. 14(6), 595–600 (2018).
Crutchfield, J. P. Between order and chaos. Nat. Phys. 8(1), 17–24 (2012).
Montiel, O., Yoshio, R., Cynthia, O. & Ajelet, R. Quantum-inspired acromyrmex evolutionary algorithm. Sci. Rep. 9(1), 1–10 (2019).
Zeng, M. & Ee-Hou, Y. Discrete-time quantum walk with phase disorder: localization and entanglement entropy. Sci. Rep. 7(1), 1–9 (2017).
Tsafack, N. et al. Design and implementation of a simple dynamical 4-D chaotic circuit with applications in image encryption. Inform. Sci. 515, 191–217 (2020).
Bernstein, D. J. & Tanja, L. Post-quantum cryptography. Nature 549(7671), 188–194 (2017).
Khan, M. & Waseem, H. M. A novel image encryption scheme based on quantum dynamical spinning and rotations. PLoS One 13(11), e0206460. https://doi.org/10.1371/journal.pone.0206460 (2018).
Cui, L. & Cao, Y. A new S-box structure named affine-power-affine. Int. J. Innov. Comput. Inform. Control 3(3), 751–759 (2007).
Kim, J. & Phan, R. C. Advanced differential-style cryptanalysis of the NSA’s skipjack block cipher. Cryptologia 33(3), 246–270 (2009).
Gao, W., Idrees, B., Zafar, S. & Rashid, T. Construction of nonlinear component of block cipher by action of modular group PSL(2, Z) on projective line PL(GF(28)). IEEE Access 8, 136736–136749 (2020).
Qiao, H. et al. Conditional teleportation of quantum-dot spin states. Nat. Commun. 11(1), 1–9 (2020).
Parvaz, R. & Zarebnia, M. A combination chaotic system and application in color image encryption. Opt. Laser Technol. 101, 30–41 (2018).
Rukhin, A., Soto, J. & Nechvatal, J. A statistical test suite for random and pseudorandom number generators for cryptographic applications. Proc. NIST 1–164, (2010).
Jakimoski, G. & Kocarev, L. Chaos and cryptography: block encryption ciphers based on chaotic maps. IEEE Trans. Circuits Syst. I Fundam. Theory Appl. 48(2), 163–169 (2001).
Silva-García, V. M., Flores-Carapia, R., Rentería-Márquez, C., Luna-Benoso, B. & Aldape-Pérez, M. Substitution box generation using chaos: an image encryption application. Appl. Math. Comput. 332, 123–135 (2018).
Mazumdar, B., Mukhopadhyay, D. & Sengupta, I. Constrained search for a class of good bijective S-boxes with improved DPA resistivity. IEEE Trans. Inf. Forensics Secur. 8(12), 2154–2163 (2013).
Abughazalah, N. et al. Construction of multivalued cryptographic boolean function using recurrent neural network and its application in image encryption scheme. Artif. Intell. Rev. https://doi.org/10.1007/s10462-022-10295-1 (2022).
Acknowledgements
This work was supported by National Research Foundation of Korea (NRF) grants funded by the Korea government through Ministry of Science and ICT (MSIT) (2020R1A2B5B01002145).
Author information
Authors and Affiliations
Contributions
H.M.W. conceived and conducted the experiments and S.O.H. analyzed the results. Both authors reviewed and approved the manuscript.
Corresponding authors
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Muhammad Waseem, H., Hwang, S.O. Design of highly nonlinear confusion component based on entangled points of quantum spin states. Sci Rep 13, 1099 (2023). https://doi.org/10.1038/s41598-023-28002-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-023-28002-7
This article is cited by
-
A probabilistic model of quantum states for classical data security
Frontiers of Physics (2023)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.