Abstract
We provide a rigorous security proof of continuous-variable measurement-device-independent quantum key distribution which incorporates finite-size effects and composable terms. In order to use realistic and optimized parameters and be able to derive results close to experimental expectations, we run protocol simulations supported by a Python library, including all the protocol operations, from simulating the quantum communication till the extraction of the final key.
Similar content being viewed by others
Introduction
Quantum key distribution (QKD) uses a quantum channel for the transmission of signals between two distant legitimate parties to create a shared secret key1,2,3. The secret key can be later utilized for the symmetric encryption of confidential messages exchanged between the parties. In particular, based on the laws of quantum mechanics, QKD allows for the detection of the presence of an eavesdropper in the quantum channel and the quantification of the compromised amount of information4,5. Depending on this amount, the shared data after the quantum communication can be compressed into a shorter shared key, about which the eavesdropper possesses negligible knowledge. This leads to quantum-safe applications, i.e., applications safe against attacks by large quantum computers.
In the beginning, QKD protocols were based on a discrete-variable (DV) encoding6,7,8, such as the polarization of a photon. The security of such protocols has been thoroughly investigated. More recently, protocols that exploit continuous degrees of freedom, such as the position and momentum of the electromagnetic field9 have been developed10,11,12. These are called “continuous-variable” (CV) QKD protocols. CV-QKD is highly compatible with the current telecommunications and, consequently, promises simpler and cost-effective practical implementations. Furthermore, it produces high rates, which approach the capacity limit of repeaterless quantum communications, also known as PLOB bound13. Their performance with respect to larger distances has improved significantly14,15.
Crucial improvements have also been demonstrated in their security level. We have different levels of security (on top of the levels listed below, the security is characterized also by the level of attacks, i.e, individual, collective, or coherent ones9) according to the assumptions taken into consideration when one calculates the secret key rate (secret bits per channel use). The first is the asymptotic security which assumes an infinite number of signals. The finite-size security16 refers to the practical use of a finite number of signals. And finally, the composable framework17 considers all the post-processing subroutines in the evaluation of the security of the protocol.
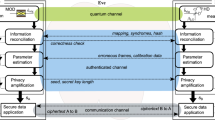
A standard QKD protocol provides security against channel attacks, where the eavesdropper interacts with the quantum signals propagating through the channel. However, equivalently crucial, if not more dangerous, are the attacks connected with the preparation or detection processes, where the eavesdropper has direct access to the labs of the two legitimate parties. These attacks are known as side-channel attacks1. MDI-QKD18,19 and CV-MDI-QKD20,21,22,23,24 have the intrinsic property of relieving the parties from any detection obligation. In fact, it uses an intermediate relay, which is responsible for the detection part of the protocol. The relay can be considered part of the channel, i.e., under the control of the eavesdropper. The outcomes of this detection are classically broadcast to the parties, who utilize them to build correlations between their data strings. This configuration can be used as a basis for constructing multi-user applications25,26 (see27, Appendix VII) that can be extended to QKD networks28. Experimental implementations have also taken place recently29,30.
Here, we focus on a simulation analysis similar to Ref.31,32 but for the CV-MDI protocol20,21. Its finite-size security analysis has been presented in Ref.33, with a first composable study discussed in Ref.34. In “Protocol and asymptotic secret key rate” section, we give a detailed summary of the protocol and the calculation of its asymptotic key rate. Then, we assume finite-size effects and describe the postprocessing subroutines. In “Composable security” section, we adapt the composable proof of Ref.17 to the CV-MDI protocol. This proof removes an issue from a previous treatment34 (see also27, Appendix VI). In “Privacy amplification” section, we explain how the parties apply the appropriate amount of compression to the data to extract a secret key, according to the previous analysis. We present all the results of the simulation with the help of a developed Python library in “Simulation and results” section. Conclusions are in “Conclusion” section.
Security analysis
In this section, we investigate the quantum communication part of the protocol (considering the classical postprocessing part ideal). We focus on the potential to build strong correlations secret to the eavesdropper considering an infinite number of signals between the parties. We present this analysis here because, as we show later, the asymptotic secret key rate is an integral part of the composable secret key rate, along with the correction terms because of the non-ideal character of the classical postprocessing procedures.
Protocol and asymptotic secret key rate
Alice and Bob prepare coherent states \(|\alpha \rangle\) and \(|\beta \rangle\) with amplitudes \(\alpha =(1/2)(Q_A+\textrm{i}P_A)\) and \(\beta =(1/2)(Q_B+\textrm{i}P_B)\), carried by modes A and B respectively. In particular, they encode the real vectorial variables \(\varvec{\alpha }=(Q_A,P_A)\) and \(\varvec{\beta }=(Q_B,P_B)\) following the Gaussian distributions
with variances \(\sigma _A^2\) and \(\sigma _B^2\) respectively. The two bosonic modes travel to an intermediate relay, where a Bell measurement is applied to them with outcome \(\gamma =(1/2)(Q_R+\textrm{i}P_R)\). We also use the notation \(\varvec{\gamma }=(Q_R,P_R)\).
Eve interacts with the traveling modes via a two-mode attack where mode \(E_1\) is mixed with mode A through a beam splitter with transmissivity \(T_A\) and mode \(E_2\) with mode B through a beam splitter with transmissivity \(T_B\) (see Fig. 1). The CM of Eve’s modes is given by
where the bona fide conditions for g and \(g^{\prime }\) are given in Ref.21. In fact, given the previous description (These attacks are collective Gaussian two mode attacks and represent the entangling cloner attack35,36 counterpart of a channel comprised of two links.), the best attacks are those with \(g<0\) and \(g^\prime >0\). Taking into consideration this area of values, one can see that as |g| and \(|g^\prime |\) become larger, the modes become more quickly and more strongly correlated (entangled). Then, one can choose \(g_\text {max}=\text {max}\{|g|,|g^\prime |\}\) and assume the attack with
as the worst-case scenario. In such a case, the quadratures can be treated equivalently, as they follow the same probability distribution.
Alice and Bob send coherent states \(|\alpha \rangle\) and \(|\beta \rangle\) with modes A and B to the intermediate relay. Eve’s modes \(E_1\) and \(E_2\) interact with the traveling modes via beam splitters with transmissivities \(T_A\) and \(T_B\) respectively. Eve’s two-mode attack is characterized by thermal noise parameters \(\omega _1\) and \(\omega _2\) (see Eq. 3). Eve’s modes are stored in a quantum memory waiting for an optimal measurement after the communication between the parties.
The outputs \(Q_R\) and \(P_R\) are dependent on the variables \(Q_A\), \(P_A\) and \(Q_B\), \(P_B\) according to the following equations:
where \(\tau _A\) and \(\tau _B\) are rescaling parameters connected to the overall attenuation via
and the noise variables \(Q_z\) and \(P_z\) have variance \(\sigma _{z}^2\) such that
where \(\eta _\text {eff}\) and \(v_\text {el}\) are the calibrated detection efficiency and electronic noise of the detectors respectively. In Supplementary Appendix V, we show the details of the calibrated noise attack and its connection to the uncalibrated one (see Supplementary Appendix IV). Subsequently, we obtain
with
In the EB representation, one introduces additional modes a and b in two-mode squeezed-vacuum (TMSV) states with modes A and B, respectively. These states have variances \(\mu _A=\sigma _A^2+1\) and \(\mu _B=\sigma _B^2+1\), respectively. Then, the encoding process is simulated by a heterodyne measurement on modes a and b with corresponding measurement outcomes \(\tilde{\varvec{\alpha }}\) and \(\tilde{\varvec{\beta }}\). The initial CM of the systems is given by
with \(\textbf{V}_{aA}(\mu _A)\) and \(\textbf{V}_{Bb}(\mu _B)\) being CMs of a TMSV state
and \(\textbf{Z}=\text {diag}\{1,-1\}\). The attack corresponds to applying a beam splitter with transmissivity \(T_A\) between the modes A and \(E_1\) and a beam splitter of transmissivity \(T_B\) between modes B and \(E_2\). The beam splitter symplectic operation with transmissivity T is given by
After the beam splitters, Alice’s and Bob’s modes \(A'\) and \(B'\) are mixed in a balanced beam splitter (i.e., \(T=1/2\)) and conjugate homodyne measurements are applied to the output modes with outcomes grouped in the variable \(\varvec{\gamma }\). In fact, starting from a CM with the following general form
if we apply a homodyne measurement to mode M with outcome \(x_M\), the CM after the measurement will be given by
with \(\varvec{\Pi }={{\,\textrm{diag}\,}}\{1,0\}\) (\(\varvec{\Pi }={{\,\textrm{diag}\,}}\{0,1\}\)) for a Q(P)-measurement and \((.)^{-1}\) being the pseudo-inverse operation.
In this description, the CM after the relay measurements is given by
where
The conditional CM after the heterodyne measurement of mode b with outcome \(\tilde{\varvec{\beta }}\) is given by
From the matrices
and \(\textbf{V}_{a|\varvec{\gamma }\tilde{\varvec{\beta }}}\), we can calculate the mutual information between \(\tilde{\varvec{\beta }}\) and Alice’s outcome \(\tilde{\varvec{\alpha }}\) which is
One may also calculate, from the CM in Eq. (17), Eve’s Holevo information
which is expressed in terms of conditional von Neumann entropies. Then by the assumption that Eve’s systems \(E=E_1'E_2'e\) purify the whole output state, we have that the von Neumann entropy of the state \(\rho _{E|\varvec{\gamma }}\) equals that of \(\rho _{ab|\varvec{\gamma }}\), and similar equivalence holds between \(\rho _{E|\tilde{\varvec{\beta }}\varvec{\gamma }}\) and \(\rho _{a|\tilde{\varvec{\beta }}\varvec{\gamma }}\). These entropies are not dependent on the outcomes \(\tilde{\varvec{\beta }}\) and \(\varvec{\gamma }\) and can be expressed in terms of the symplectic eigenspectra \(\{\nu _{\pm }\}\) and \(\tilde{\nu }\) of of the CMs \(\textbf{V}_{ab|\varvec{\gamma }}\) and \(\textbf{V}_{a|\tilde{\varvec{\beta }}\varvec{\gamma }}\) respectively, so that
with
In terms of mutual information, the measurement variables \(\varvec{\tilde{\alpha }}\) and \(\varvec{\tilde{\beta }}\) in the EB scheme are equivalent to the rescaled P&M variables, \(\varvec{\alpha }\) and \(\varvec{\beta }\). Then the conditioning on \(\varvec{\gamma }\) is equivalent to a displacement on the variables \(\varvec{\alpha }\) and \(\varvec{\beta }\) so that key-extraction variables, \(\textbf{x}=(Q_x,P_x)\) and \(\textbf{y}=(Q_y,P_y)\), need to be suitably constructed. In fact, the parties use the following relations
An optimal option for the parameters u and v is given by assuming a minimal correlation between the new variables, \(\textbf{x}\) and \(\textbf{y}\), and the relay outputs. This is explained by the fact that Eve should know as less as possible about \(\textbf{x}\) and \(\textbf{y}\) by knowing \(\varvec{\gamma }\). Therefore, we impose
so to obtain (These are the regression coefficients. Given a bipartition of a multivariate Gaussian distribution \(\{\textbf{x}_1,\textbf{x}_2\}\) with CM \(\varvec{\Sigma }\), the regression coefficients are given by the matrix \(\varvec{\Sigma }_{12}\varvec{\Sigma }_{22}^{-1}\). One may write that \(\textbf{y}=\textbf{x}_1|\textbf{x}_2=\textbf{x}_1-\varvec{\Sigma }_{12}\varvec{\Sigma }_{22}^{-1}\textbf{x}_2\).)
Therefore, one may write
where the first equality is proven in Ref.27, Appendix I.
The quantum mutual information between Eve’s system \(E=E^\prime _1E^\prime _2e\) and Bob’s key-extraction variable \(\textbf{y}\) when she has access to the variable \(\varvec{\gamma }\) is given by37, Lemma 7.4.4

and it is equal to the Holevo information \(\chi (E:\textbf{y}|\varvec{\gamma })\) since \(\textbf{y}\) is a classical variable. In particular, we have that, given \(\varvec{\gamma }\), there is a function \(\textbf{y}=f(\varvec{\beta })\) determined by the relations in Eqs. (31) and (32) such that \(\varvec{\beta }=f^{-1}(\textbf{y})\). This allows us to apply the data processing inequality in both directions with respect to y and \(\beta\) and obtain
At this point, one may define the asymptotic key rate
which is calculated starting from the CM in Eq. (17) as in Ref.21. Note that \(\zeta\) is the reconciliation parameter defined later in Eq. (70). This parameter accounts for the proportion of mutual information given to Eve during the public channel communication of the parties performing a non-ideal reconciliation process.
Parameter estimation
Here we follow the PE proposed in Ref.33. An alternative way is described in27, Appendix II.B based on extra simplifying assumptions. In particular, based on m samples \([Q_A]_i\), \([Q_B]_i\), \([Q_R]_i\), for \(i=1,\dots , m\), the parties calculate the maximum likelihood estimators (MLEs) of the covariances \(\text {Cov}( Q_A, Q_R)=\langle Q_A Q _R\rangle =-\tau _A \sigma _A^2\) and \(\text {Cov}( Q_B, Q_R)=\langle Q_B Q _R\rangle =\tau _ B\sigma _B^2\). These estimators are given by
From these, they define estimators for \(T_A\) and \(T_B\), i.e.,
Then they define an estimator for \(\sigma ^2_{z}\). This estimator is given by
with
and obtain the associated variances27, Appendix II.A
Based on \(\widehat{\sigma }_z^2\) they find an estimator for \(\Xi\) given by
with variance equal to
Finally, worst-case scenario values can be derived given the PE error \(\epsilon _\text {PE}\). These values are
where
Using the previous values, the parties can compute a secret key rate with an overestimated Holevo information
Note here that \(m=N-n\) where N is the number of signals sent through the channel and n is the number of signals devoted to secret key extraction for each block. In a practical situation, where the transmission can be assumed stable over a large number of blocks \(n_{\text {bks}}\), one can use m signals on average from each block in order to estimate the channel parameters. Thus the parties sacrifice \(M=m n_\text {bks}\) for PE and the corresponding rate is given by
The mutual information and the correlation between the two variables \(\textbf{x}\) and \(\textbf{y}\) are connected as follows38, Eq. (8.56) (see also27, Eq. (2)):
One may derive the estimator for the correlation between the variables by replacing with the MLEs of the transmissivities and noise into the mutual information, namely,
which helps in the calculation of the a priori probabilities for the initialization step of the decoding sum-product algorithm of the error correction step31,32.
Data reconciliation
The parties apply the transformations of Eqs. (29)–(32) based on the quantities in Eqs. (34)–(37) calculated via the MLEs of the previous section. Bob and Alice combine their data from the Q and P quadratures into one variable. In particular, Alice and Bob apply the following mapping to their data:
in order to obtain 2n samples from each block. Afterwards, the parties apply the EC procedure using non-binary LDPC codes following Ref.32, Sect. III.B (for extra details see also Ref.31). More specifically, they define the worst-case estimator (up to an error probability \(\epsilon _\text {ent}\)) for the reconciliation parameter \(\zeta\) appearing in Eq. (43) which is given by
where \(2(\widehat{H}(\mathsf{l})-\delta _\text {ent})\) is the worst-case scenario entropy of the raw-key string described by \(\textsf{l}\), the normalized and discretized version of y. In particular, \(2\widehat{H}(\mathsf{l})\) is the estimator of the previous entropy, \(-R_\text {code}q+p\) is the maximum data exchanged for reconciliation per channel use when one uses a non-binary LDPC code with the rate \(R_\text {code}\) associated with the Galois filed \(\mathcal {G}(2^q)\) and discretization of p bits. We take into consideration here that Bob applies the LDPC encoding only to the q bits of \(\mathsf{l}\) while the rest \(p-q\) bits are entirely sent through the public channel. \(I(\textbf{x}:\textbf{y})|_{\widehat{T}_A,\widehat{T}_B,\widehat{\Xi }}\) is the ideal mutual information between the parties according to the data (i.e., after parameter estimation) which appears in Eq. (63). In fact by replacing \(\hat{\zeta }\) in the previous equation, one obtains the practical key rate
The parties started with two different sequences of \(n_\text {bks}\) blocks each with 2N initial samples and, in the process (after PE and EC), these are reduced to two indistinguishable binary sequences (with probability \(1-\epsilon _\text {EC}\)) that consist of \(p_\text {EC}n_\text {bks}\) blocks each carrying 2np bits:
Note that \(\overline{\mathsf{l}}_\text {bin}^n\) corresponds to the part of the original variable \(\mathsf{l}\) in binary form that has been sent through the public channel using the LDPC encoding, \(\underline{\mathsf{l}}_\text {bin}^n\) is the part in binary form that has been sent unchanged through the public channel, and \(\widehat{\mathsf{l}}_\text {bin}^n\) is the binary form of the successfully decoded and verified part with probability \(p_\text {EC}\). The parties need to apply on these sequences the appropriate amount of compression during the PA step so that the previous raw-data strings become a secret key. This is determined by the composable key rate calculated below. Concatenating appropriately the previous parts, the parties end up with the raw data sequences \(\mathsf{l}_\text {bin}\) for Bob and \(\tilde{\mathsf{l}}_\text {bin}\) for Alice in binary form.
Composable security
We adopt the composable framework security analysis presented in Ref.17, Appendix G to the requirements of the CV-MDI-QKD protocol. More specifically, the secret key is characterized by certain properties stemming from certain post-processing procedures, and there is an overall probability \(\epsilon\) that the key fails to possess at least one of these properties.
According to the previous analysis, one may write for the length of the secret key17, Eq. (G12):
where l is defined according to the bidirectional mapping
where \(\mathsf{l}_{Q}\)(\(\mathsf{l}_{P}\)) is the \(\textsf{l}\) instance corresponding to the q(p)-quadrature. Note that here we have used a virtual concatenation assumption (see Appendix A of 32) to pass from a description based on the single-quadrature variable \(\textsf{l}\) (normalized and discetized) to one based on the vectorial variable l. One may also observe that, in this case, Eve’s system is described by the group of modes E plus the classical variable \(\varvec{\gamma}\). In particular, \(H(l|{E\varvec{\gamma }})\) is the conditional von Neumann entropy of the variable l conditioned on E and \(\varvec{\gamma}\), and39, Eq. (61)
with \(|\mathcal {L}|\) being the cardinality of the discretized variable l, which in our case is \(2^{2p}\). Note that, for the conditional mutual information, we have 37, Def. 7.4.1
In particular, this mutual information is between a classical variable l and a quantum system E (conditioned on another classical variable \(\varvec{\gamma }\)). This is therefore the Holevo information \(\chi (E:l|\varvec{\gamma })\), i.e., an upper bound for the accessible information on l given that Eve possesses E (and knows the variable \(\varvec{\gamma }\)). Therefore, by reversing Eq. (76), one may write
where \(H(l|\varvec{\gamma })=H(l)\) (see Eq. 33) is the Shannon entropy of l. In more detail, using the data processing inequality, we manipulate Eve’s Holevo bound as follows
Therefore we have
We may replace Eq. (79) in Eq. (73) and then set
In this way, we derive
where we include the asymptotic secret key rate of Eq. (43). One may replace \(R_\text {asy}\) with \(R_{M}^{\textrm{EC}}\) of Eq. (71) into Eq. (81) to obtain (see also17,32,39)
with composable terms
The overall security parameter is equal to
where we note that the factor 3 is due to the fact the \(\epsilon _\text {PE}\) is defined per parameter.
One may also derive an approximate key rate, which is not based on the data postprocessing
where \(\bar{R}_{M}\) is the rate in Eq. (63) but where the estimators are approximated using the initial values of the simulation (see, e.g., the steps in Sects. III.B.1 and III.B.2 in Ref.31). In fact, one may define \(\bar{R}_{M}\) from Eq. (63) but where the following substitutions have been made:
and
where \(\sigma _{T_A}\), \(\sigma _{T_B}\), and \(\sigma _{\Xi }\) have been calculated through Eqs. (53), (54), and (57), respectively, after replacing \(T_A\), \(T_B\), and \(\sigma _z^2\) in those formulas. Note that the rates presented in this section do not rely on the conjecture mentioned in27, Appendix VI.
Privacy amplification
Now the parties are ready to apply the appropriate amount of compression indicated by Eq. (82) on their binary strings in Eq. (72) to create a secret key through the PA step. To achieve this, they compress them via universal hashing. More specifically, they apply a modified Toeplitz matrix \(\textbf{G}(\textbf{I}_r|\textbf{T}_{r,2np-r})\) to their sequences in order to extract the secret key40
where \(r=2np\tilde{R}\), the Toeplitz matrix \(\textbf{T}_{r,2np-r}\) is of \(r\times 2np-r\) dimensions and \(\textsf{I}_r\) is the \(r \times r\) identity matrix, with \(\textsf{l}_\text {bin}^{r}\) we denote the first r bits of the raw key string and with \(\textsf{l}_\text {bin}^{2np-r}\) the rest.
Simulation and results
In our simulations, the attack is handled by initially defining values for the excess noise of Alice’s (\(\xi _{A}\)) and Bob’s (\(\xi _{B}\)) channels. These values, along with the transmissivity of each channel, constitute the thermal noise \(\omega\) for each channel respectively as follows:
Using Alice’s thermal noise value, we can estimate the correlation parameter g from Eq. (11). We now have all components to find the excess noise variance \(\Xi\), which is shown in Eq. (10). Finally, the noise variance \(\sigma ^2_{z}\) is calculated through Eq. (9).
The parameters used to execute the simulations are listed in Table 2. To begin with, the symmetric version of the protocol is examined, which means that the signal variance and the channel parameters will be the same between Alice and Bob, i.e. \(\mu _{A}=\mu _{B}\), \(T_{A}=T_{B}\) and \(\xi _{A}=\xi _{B}\).
To find a signal variance range, for which the composable rate R becomes positive, the asymptotic rate \(R_\text {asy}\) was maximized using a modulation variance optimization function. Table 1 shows that a positive R can be achieved, when \(45\le \mu _{A}, \mu _{B} \le 50\). Under these conditions, the SNR spans from approximately 10 to 11.89. As presented in the Table, the choice of the reconciliation efficiency is important, when trying to maximize the value of R. It is important to note that neither the asymptotic nor the composable rate will further grow, as the signal variances increase. This means that, at some point, the rates will saturate and eventually become negative again.
Knowing the variables, for which the composable rate becomes positive, we can now identify what is the maximum tolerable excess noise in the system. For this purpose, \(\mu _{A} = \mu _{B} = 46\) is chosen, in order to produce a high rate (and therefore tolerate more excess noise), while performing a faster EC procedure (when compared to that for \(\mu _{A} = \mu _{B} = 49\)). Therefore, in Fig. 2, the symmetric case of the protocol is considered again, with \(\mu _{A}=\mu _{B}=46\) and with the excess noise being variable. As observed from the plot, \(\xi\) can take values up to 0.008, before the protocol is deemed unsafe for key distribution.
Composable secret key rate R (bits/use) versus Alice’s and Bob’s excess noise values \(\xi =\xi _{A}=\xi _{B}\). Every point represents the average value of R, which is obtained after 5 simulations. Here we use \(N=5 \times 10^{5}\) and \(n_\text {bks}=100\). All simulations have achieved \(p_\text {EC} \ge 0.95\). The signal variances used by Alice and Bob are constant and equal (\(\mu _{A}=\mu _{B}=46\)). The values of the reconciliation efficiency \(\zeta\) are shown on the top axis. Other parameters are taken as in Table 2.
Composable secret key rate R (bits/use) versus Alice’s transmissivity \(T_{A}\). Every point represents the average value of R, which is obtained after 5 simulations. Here we use \(N=5.88 \times 10^{5}\) and \(n_\text {bks}=100\). All simulations have achieved \(p_\text {EC} \ge 0.95\). The signal variances used by Alice and Bob are constant (\(\mu _{A}=60\), \(\mu _{B}=50\)). The values of the reconciliation efficiency \(\zeta\) are shown on the top axis. Other parameters are taken as in Table 2.
Composable secret key rate (bits/use) versus Alice’s excess noise value \(\xi _{A}\). Every point represents the average value of R, which is obtained after 5 simulations. Here we use \(N=5.88 \times 10^{5}\) and \(n_\text {bks}=100\). All simulations have achieved \(p_\text {EC} \ge 0.95\). The signal variances used by Alice and Bob are constant (\(\mu _{A}=60\), \(\mu _{B}=50\)). The values of the reconciliation efficiency \(\zeta\) are shown on the top axis. Other parameters are taken as in Table 2.
Next, we investigate the asymmetric version of the protocol, where the channel parameters, as well as the signal variances, are different between Alice and Bob. Here, two cases are examined: Fig. 3 shows the behaviour of Alice’s transmissivity against the composable key rate and Fig. 4 displays the maximum tolerable values for Alice’s excess noise. Regarding the former case, it is possible for Alice’s channel to reach transmissivity values of about \(T_{A} = 0.94\), which translates to a fiber length of 1.34 km. The latter case shows that it is feasible to achieve a positive R under relatively high values for the excess noise, which can be extended to \(\xi _{A}=0.01\). To ensure a positive composable rate is positive under harsher noise settings, it is possible to employ a larger LDPC matrix with a block length very close to the order of \(10^6\) (The use of non-binary LDPC codes allows for block sizes under \(10^6\). A fair comparison with existing research (using binary LDPC codes) would be to multiply the current block sizes with the Galois field component q. Note that the stable channel assumption (see Eq. 63) and the use of high SNR in our study contribute, as well, to obtaining rates with these block size values.) and \(R_\text {code}=0.875\) for the task. Because of the finite-size effect, a larger LDPC block size leads to higher values for the reconciliation efficiency, when all other values remain the same.
Conclusion
In this study, we give a rigorous proof for the composable security of the Gaussian-modulated CV-MDI protocol and we calculate its rate. Depending on this rate, the appropriate amount of compression is applied, in order to extract a secret key. We simulate the quantum communication step and we apply all the classical postprocessing steps on the generated data. All of these procedures are performed by means of an associated Python library. This library allows us to calibrate and optimize all the relevant parameters with direct benefits for experimental implementations.
Data availability
The datasets and the Python library used and/or analyzed during the current study are available from the corresponding author upon reasonable request.
References
Pirandola, S. et al. Advances in quantum cryptography. Adv. Opt. Photon. 12, 1012–1236 (2020).
Gisin, N., Ribordy, G., Tittel, W. & Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 74, 145 (2002).
Cao, Y. et al. The evolution of quantum key distribution networks: On the road to the Qinternet. IEEE Commun. Surv. Tutor. https://doi.org/10.1109/COMST.2022.3144219 (2022).
Park, J. The concept of transition in quantum mechanics. Found. Phys. 1, 23–33 (1970).
Wootters, W. & Zurek, W. A single quantum cannot be cloned. Nature 299, 802–803 (1982).
Bennett, C. H. & Brassard, G. Quantum cryptography: public key distribution and coin tossing. In Proceedings of the International Conference on Computers, Systems & Signal Processing, Bangalore, India 175–179 (1984).
Ekert, A. K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67, 661 (1991).
Bennett, C. H. Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68, 3121 (1992).
Weedbrook, C. et al. Gaussian quantum information. Rev. Mod. Phys. 84, 621 (2012).
Grosshans, F. & Grangier, P. Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 88, 057902 (2002).
Weedbrook, C. et al. Quantum cryptography without switching. Phys. Rev. Lett. 93, 170504 (2004).
Usenko, V. C. & Grosshans, F. Unidimensional continuous-variable quantum key distribution. Phys. Rev. A 92, 062337 (2015).
Pirandola, S., Laurenza, R., Ottaviani, C. & Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 8, 15043 (2017).
Zhang, Y. et al. Long-distance continuous-variable quantum key distribution over 202.81 km of fiber. Phys. Rev. Lett. 125, 010502 (2020).
Zhou, C. et al. Continuous-variable quantum key distribution with rateless reconciliation protocol. Phys. Rev. Appl. 12, 054013 (2019).
Ruppert, L., Usenko, V. C. & Filip, R. Long-distance continuous-variable quantum key distribution with efficient channel estimation. Phys. Rev. A 90, 062310 (2014).
Pirandola, S. Limits and security of free-space quantum communications. Phys. Rev. Res. 3, 013279 (2021).
Braunstein, S. L. & Pirandola, S. Side-channel-free quantum key distribution. Phys. Rev. Lett. 108, 130502 (2012).
Lo, H.-K., Curty, M. & Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108, 130503 (2012).
Pirandola, S., Ottaviani, C., Spedalieri, G., Weedbrook, C. & Braunstein, S. L. Continuous-variable quantum cryptography with untrusted relays. Preprint at http://arxiv.org/abs/1312.4104v1 (2013).
Pirandola, S. et al. High-rate measurement-device-independent quantum cryptography. Nat. Photon. 9, 397–402 (2015).
Ma, X.-C., Sun, S.-H., Jiang, M.-S., Gui, M. & Liang, L.-M. Gaussian-modulated coherent-state measurement-device-independent quantum key distribution. Phys. Rev. A 89, 042335 (2014).
Li, Z., Zhang, Y.-C., Xu, F., Peng, X. & Guo, H. Continuous-variable measurement-device-independent quantum key distribution. Phys. Rev. A 89, 052301 (2014).
Tian, Y. et al. Experimental demonstration of continuous-variable measurement-device-independent quantum key distribution over optical fiber. Optica 9, 492–500 (2022).
Papanastasiou, P., Weedbrook, C. & Pirandola, S. Continuous-variable quantum key distribution in fast fading channels. Phys. Rev. A 97, 032311 (2018).
Ottaviani, C., Lupo, C., Laurenza, R. & Pirandola, S. Modular network for high-rate quantum conferencing. Commun. Phys. 2, 118 (2019).
Papanastasiou, P., Mountogiannakis, A. G. & Pirandola, S. Supplementary Material: Composable Security of CV-MDI-QKD: Secret Key Rate and Data Processing.
Ghalaii, M., Papanastasiou, P. & Pirandola, S. Composable end-to-end security of Gaussian quantum networks with untrusted nodes. http://arxiv.org/abs/2203.11969v1.
Liao, Q., Wang, Y., Huang, D. & Guo, Y. Dual-phase-modulated plug-and-play measurement-device-independent continuous-variable quantum key distribution. Opt. Express 26, 19907–19920 (2018).
Hajomer, A. A. E., Andersen, U. L. & Gehring, T. Real-world data encryption with continuous-variable measurement device-independent quantum key distribution. http://arxiv.org/abs/2303.01611.
Mountogiannakis, A. G., Papanastasiou, P., Braverman, B. & Pirandola, S. Composably secure data processing for Gaussian-modulated continuous-variable quantum key distribution. Phys. Rev. Res. 4, 013099 (2022).
Mountogiannakis, A. G., Papanastasiou, P. & Pirandola, S. Data post-processing for the one-way heterodyne protocol under composable finite-size security. Phys. Rev. A 106, 042606 (2022).
Papanastasiou, P., Ottaviani, C. & Pirandola, S. Finite-size analysis of measurement-device-independent quantum cryptography with continuous variables. Phys. Rev. A 96, 042332 (2017).
Lupo, C., Ottaviani, C., Papanastasiou, P. & Pirandola, S. Continuous-variable measurement-device-independent quantum key distribution: Composable security against coherent attacks. Phys. Rev. A 97, 052327 (2018).
Papanastasiou, P., Ottaviani, C. & Pirandola, S. Security of continuous-variable quantum key distribution against canonical attacks. Int. Conf. Comput. Commun. Netw. 2021, 1–6. https://doi.org/10.1109/ICCCN52240.2021.9522349 (2021).
Pirandola, S., Braunstein, S. L. & Lloyd, S. Characterization of collective Gaussian attacks and security of coherent-state quantum cryptography. Phys. Rev. Lett. 101, 200504 (2008).
Renner, R. Quantum Information Theory, Lecture Notes (2013).
Cover, T. M. & Thomas, J. A. Elements of Information Theory (Wiley, 2012).
Pirandola, S. Composable security for continuous-variable quantum key distribution: Trust levels and practical key rates in wired and wireless. Phys. Rev. Res. 3, 043014 (2021).
Tang, B., Liu, B., Zhai, Y., Wu, C. & Yu, W. High-speed and large-scale privacy amplification scheme for quantum key distribution. Sci. Rep. 9, 15733 (2019).
Acknowledgements
A. M. was supported by the Engineering and Physical Science Research Council (EPSRC) via a Doctoral Training Partnership EP/R513386/1. S. P. was supported by the European Union’s Horizon 2020 Research and Innovation Action under Grant Agreement No. 862644 (FET-OPEN project: Quantum readout techniques and technologies, QUARTET).
Author information
Authors and Affiliations
Contributions
P.P. adapted the simulation steps and the composable theory proof to the CV-MDI-QKD setting. A.M. Created the simulation the code and the results and plots of this study. S.P. organized and supervised the previous tasks and proposed the main idea of this study. All participated equally in creating the document.
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Papanastasiou, P., Mountogiannakis, A.G. & Pirandola, S. Composable security of CV-MDI-QKD with secret key rate and data processing. Sci Rep 13, 11636 (2023). https://doi.org/10.1038/s41598-023-37699-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/s41598-023-37699-5
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.